ISO27001 - Risk Analysis on ISO27001:2013 Sample by Fernando

Contents
-
1 Introduction
-
2 Asset Analysis
-
2.1 Definition of asset weighting based on assumptions
-
3 Controls Analysis
-
3.1 Controls Analysis by control
-
3.2 General Kiwiat Controls Analysis
-
4 Threat categorization
-
5 Risk Analysis
-
6 Risk treatment plan
-
7 Security Incident Analysis
-
8 Conclusions
-
9 Bibliography
1. Introduction
Because security requirements are increasingly present in today’s systems, standards were created which established guidelines that allow a data management to ensure that companies implement all appropriate controls on confidentiality, integrity and availability of information, so you can protect the information of stakeholders, which should be included as customers, employees, business partners and society in general is required to have a management of assets. This asset is called Information Security Management System (ISMS). This document was created in order to perform a pre-audit to the Belmond Hotel Monasterio organization in order to implement an ISMS, complying with the controls and domains established in the ISO 27001:2013 standard.
The Belmond Hotel Monasterio is a luxury hotel (five stars) located in the city of Cusco, Peru. It has been established on the former premises of the Seminary of San Antonio Abad dating from the seventeenth century and is of Andean baroque style built on Inca walls. The hotel is located three hundred meters from the Plaza de Armas.
History
In 1598, the bishop of Cusco Antonio de Raya Navarrete founded, in accordance with the decrees of the Council of Trent, the Seminary of San Antonio Abad and granted its administration to the Society of Jesus. The purpose was to provide ecclesiastical education to young people who wanted to be part of the Church, mainly the sons of impoverished conquerors. The seminary was built on the walls of the old Amaru Qhata palace. The original building was destroyed by the earthquake of 1650 and in its reconstruction a chapel of Andean baroque style was built. In the middle of the 20th century, the Jesuits obtained authorization from Cardinal Richard Cushing, Archbishop of Boston, to build a new building, to which they moved in 1965.
Hotel
At that time, the seminary facilities were acquired and remodeled by the Peruvian state company Entur Perú to house the hotel. The building is currently considered a historical monument and has been part of Cusco’s Monumental Zone since 1972.1 Its façade still bears Spanish coats of arms and its chapel contains ancient frescoes of the Cuzco school in gold leaf frames. In the center of the hotel there is a cloister with a fountain and an ancient cedar tree that is 300 years old. The hotel also has a Peruvian restaurant and a bar.
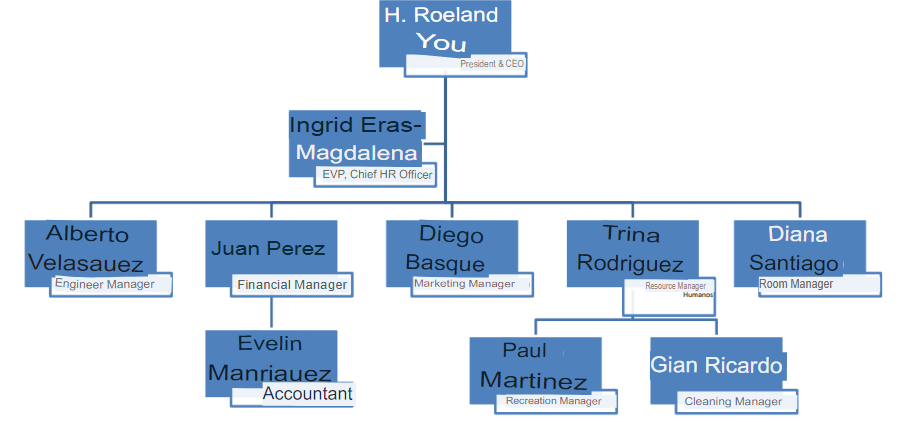
Organizational chart
List of Assets:
| Name of the Asset | Asset to consider (*) |
|---|---|
| 1. Customer Data | * |
| 2. General Equipment in the facilities | * |
| 3. Itinerary Application | * |
| 4. Meeting Room | * |
| 5. HR Management System | * |
| 6. Technical Systems Staff | |
| 7. Cloud Server | * |
| 8. Cooking Class Application | * |
| 9. Pisco Tasting | |
| 10. Restaurant Reservation Application | * |
| 11. Personal Data | |
| 12. Inventory | |
| 13. Network Wiring | |
| 14. Routers and Switches | * |
| 15. Local Server for Human Resources | * |
Mission
Belmond Monasterio Hotel’s mission is “We open the door to a new world of places, people and travel. We express ourselves with personality, based on knowledge and a sense of place and purpose.” (Alarcon, Montoya, & Zamalloa, 2014)
Vision
The vision of Belmond Monasterio Hotel is “We bring together the charming, the unexpected, the authentic and the meaningful. We celebrate individuality, diversity and personality in each of our experiences. In an idyllic paradise with a traditional setting in the city of Cusco”. (Alarcon, Montoya, & Zamalloa, 2014)
Staff
More than 125 people work at the hotel, and the Front Desk alone employs 20 people, 10 of whom work in shifts in Guest Services and Reception. The organizational structure is as follows:
(Disclaimer: The data, assets, services and many other considerations taken into account do not reflect the behavior, reality or structure of the company. It was simply mentioned to try to make a practical case and assumptions were made without any basis to meet the requirements of the activity.
- The considerations as services were taken by investigating the profile of a former employee of the company (https://pe.linkedin.com/in/################### : who is mentioned to work with C#-Sql architectures and Azure servers).
- On the other hand the assumptions of services provided by Belmond LTD are other assumptions because it is a large organization.
- In the case of the mentioned systems, they are not close to reality because I do not know how it works because I never worked in it, so I emphasize that they are my inventions. So the operation and structure of the organization does not reflect reality either).
2. Asset Analysis
We were instructed to choose the 10 assets to be considered for this activity, therefore, we chose the 10 most important of the 15, based on 2 criteria value and services necessary for guests to carry out their normal activities; these were considered based on the individual activity. individual activity.
| Assets |
|---|
| 1. Customer Data |
| 2. General Equipment in the facilities |
| 3. Itinerary Application |
| 4. Meeting Room |
| 5. HR Management System |
| 6. Cloud Server |
| 7. Cooking Class Application |
| 8. Restaurant Reservation Application |
| 9. Routers and Switches |
| 10. Local Server for Human Resources |
5. Emarisma tool logs
6. Asset categorization
| Type | Name | Value Strategic | Cost | Owner | Responsible | Description | Remarks |
|---|---|---|---|---|---|---|---|
| [S] Services | Application Cooking Classes | Low | 2,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | An application for cooking classes where users can access with a username and password that is assigned to them, so they can see the dishes they prepare, their equivalents, nutritional table and steps to follow in their respective languages of origin. | - |
| [SW] Applications (software) | Itinerary Application | Very High | 15,000.00€ | Hotel Belmond Monasterio | Alberto Velasquez | Application where guests can check their itinerary and reservations. | - |
| [SW] Applications (software) | Restaurant Reservation Application | Medium | 4,000.00€ | Alberto Velasquez | Hotel Belmond Monasterio | The Hotel Belmond Monasterio has an application to make reservations in its restaurants. Whether someone is a guest or not of the hotel. | - |
| [D] Data / Information | Customer Data | Very High | 100,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | The registry of the clients who stayed at the hotel. | - |
| [HW] Computer equipment (hardware) | General equipment in the facilities | Very High | 6,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | This is the equipment found in the organization, which is used to verify records and process requests. | - |
| [COM] Communication networks | Routers and Switches | High | 1,000.00€ | Belmond Monasterio Hotel | Alberto Velasquez | All the connection equipment such as Routers and Switches at the Belmond Monasterio Hotel. | Uninterrupted connectivity in Belmond Hotels is indispensable, especially because most of their guests are businessmen or people who need to be connected all the time. |
| [L] Facilities | Meeting Room | Very High | 5,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | In this area users can connect and hold their conferences. | - |
| [S] Services | Cloud Server | Very High | 50,000.00€ | Belmond LTD | Belmond LTD | The Belmond LTD organization owns a private PaaS type cloud server, which is assigned to each hotel in the world. This service is in charge of collecting all the information from all areas, staff and customers, for a subsequent CRM. | - |
| [HW] Hardware | Local Server for Human Resources | Medium | 5,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | Local rack server for the Human Resources software, which is in charge of workload management and attendance registration. | - |
| [SW] Applications (software) | Human Resources Management System | Medium | 3,000.00€ | Hotel Belmond Monastery | Alberto Velasquez | This system keeps track of the work attendance of the organization’s personnel. | - |
2.1. Definition of asset weighting based on the following assumptions
-
Customer data: For a company that is dedicated to the hotel industry, one of the most important assets is customer information, since it contains sensitive data that could put guests at risk or even lose their privacy; another characteristic of customer information is to be able to generate business intelligence from the information obtained by registering them and making decisions regarding the needs they present. Therefore, it is considered as the most important asset to be considered.
-
General Equipment in the facilities: The terminals or well called general equipment of the facilities, are equipment which the company has, these terminals have access to the various systems of the same, translated into long-term risks, from these could generate internal attacks to the organization, causing irreparable damage to information and reputation.
-
Itinerary Application: Guests can review their itinerary in this application and their reservations, some unscrupulous people could take advantage of this information and use it in different ways, such as theft, kidnapping, etc. Therefore, it is considered an important asset to consider.
-
Meeting Room:The Belmond Monasterio hotel has this area users where guests (Executives, businessmen, etc.) can connect and hold their conferences; therefore, if an attack were to be carried out in this area, information could be obtained on meetings that guests may have.
-
HR Management System: This system keeps track of the work attendance of the organization’s personnel. This system can efficiently manage the shifts assigned to them, compliance with working hours and the functions assigned to them during those shifts.The biggest concerns would be if the system were to fail and the personnel could not be managed efficiently, workers who did not comply with their workload, ghost workers, identity theft, etc.6.Cloud Server: The Belmond LTD organization owns a private PaaS cloud server, which is assigned to each of its employees which is assigned to each hotel in the world. This service is responsible for collecting all the information from all areas, staff and customers, for a subsequent CRM. This information does not only include the Belmond Monasterio headquarters, so that a third party access to this value, can symbolize an incalculable damage to the entire organization.
-
Cloud Server: The Belmond LTD organization has a private PaaS cloud server, which is assigned to each hotel in the world. This service is responsible for collecting all the information from all areas, staff and customers, for a subsequent CRM. This information does not only include the Belmond Monasterio headquarters, so that a third party access to this value, can symbolize an incalculable damage to the entire organization.
-
Cooking Classes Application: Within the Belmond hotel’s cooking classes application, the recipes used by the hotel itself for the dishes they serve to their guests are given, so a competitor could use this resource to try to compete based on this information.
-
Restaurant Reservation App: The restaurant reservation application is an important asset since even you have diners who are not guests and only come to try the delicacies served by the hotel, the flow of this information is important to be able to manage the reservations of the diners that you will have by dates, number of people, etc. Thus, a failure in this is counterproductive for the reputation of the hotel.
-
Routers and Switches: Connection equipment such as switches and routers are those through which information passes for the various requests from the internal network or to the hotel’s external network. A third party application that can receive the information sent by these devices would represent a violation of the guests’ privacy and may even symbolize a future hacking of the organization’s systems.
-
Local HR server: The local server for HR management contains the essential information of the company’s workers, payroll, HR management system, user passwords, etc. Violating this server can give access to different types of permissions that were assigned to the workers.
3. Analysis of controls
3.1. Analysis of controls by control. As expressed in the scope of the audit, the following controls are evaluated and analyzed:
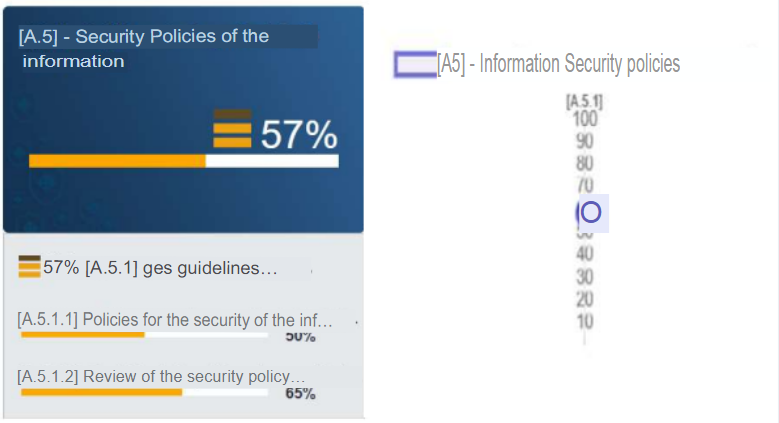
a. A.5 - Information Security Policies:
It can be observed that the percentage of compliance with the objectives exposed in the control corresponds to 57%. This percentage is due to the fact that the hotel has policies for information security which are partially supported by management but are not well communicated to new users. Likewise, the review of security policies is not well structured since it does not have an adequate control in terms of structure, schedules and criteria, since it is developed simply by the only person in charge of the technological area, the Engineering Manager, and not by a security expert, so it is evident that the review of the security policy is not performed on a regular or planned basis or with adequate input data (preventive and corrective actions, process performance, trends related to threats, among others). Thus, this is one of the critical points to be considered since it does not exceed 75% approval.
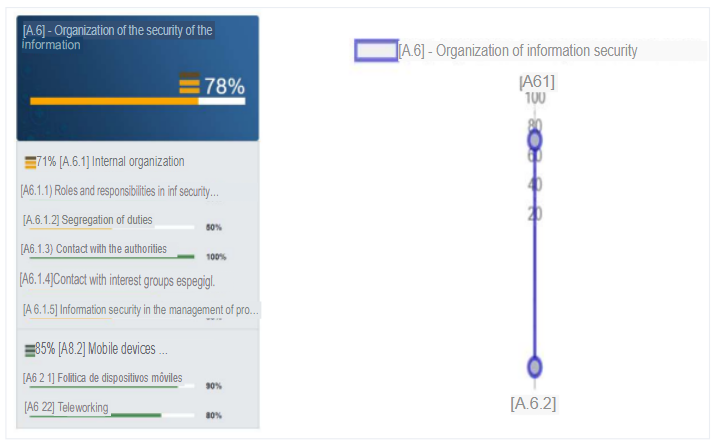
b. A.6 - Organization of information security:
It can be observed that the percentage of compliance with the objectives exposed in the control corresponds to 78%. The reason for this, although there are no established security policies regarding specific roles or security management or segregation of duties, is because there is a good management of values required for teleworking and mobile device policies provided by the organization. Although this control is higher than 75%, it is recommended to take into account that the internal organization only reaches 71%. Due to the fact that there is a very poor segregation of duties with respect to information security, because all tasks related to information security are in charge of the IT manager. Also, the assets associated to each particular system and the authorization levels that a position may have are not clearly defined, as well as the relevant security information is not constantly updated and there is no interest in knowing the trends regarding technologies, products, threats, vulnerabilities, consultancies, etc. by the IT manager.
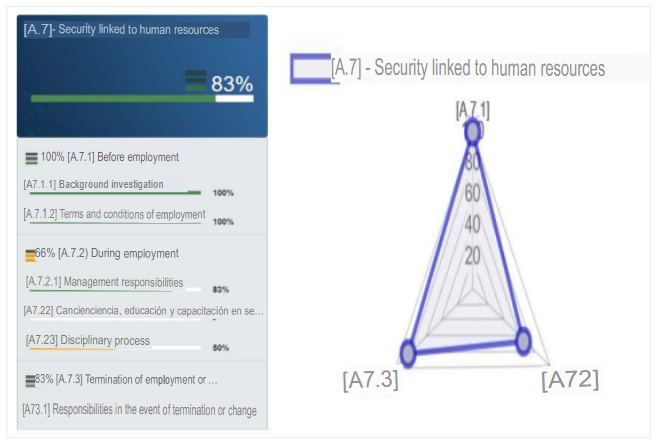
c. A.7 - Security linked to human resources
The percentage of compliance in this control is 83%. This is due to the fact that the personnel screening process is well elaborated to verify the personnel to be hired and the terms and conditions try to be as detailed as possible. However, during employment awareness is so low that it is not even considered for employee education, the disciplinary process is too lax and the only thing they can rely on is the previously established management responsibility. Yet they also have criteria at the time of contract termination.
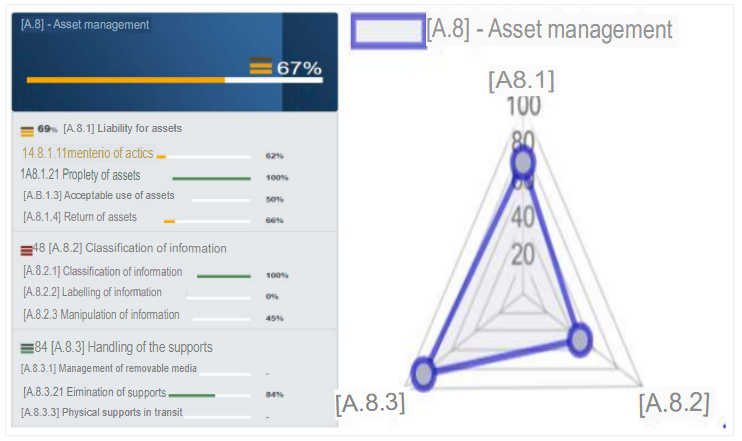
d. A.8 - Asset management
The percentage of compliance with the objectives set out in the control corresponds to 67%, being this control not acceptable. We have a somewhat structured asset inventory, a well-defined asset ownership, an acceptable use of assets at 50% and a respectable return of assets. In the case of information classification, there is no labeling of the information, so it is not considered and the handling of information is deplorable because there is no expeditious responsible control. The handling of removable media in the case of removable media does not exist, the elimination of media is consequent and physical media in transit are not used since there is a Cloud server. Therefore, it is recommended to review this control for a better management of assets and handling of information, since these points are critical in this type of organizations.
e. A.9 - Access control
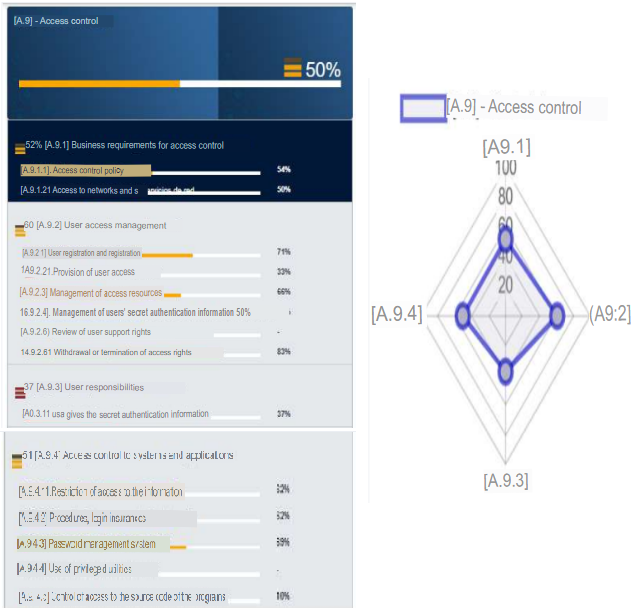
In the case of this control, compliance with this control is 50%. In general it is one of the least controlled controls (although it sounds redundant). This is due to the fact that there are no policies on the principles of necessity, there are no commercial records and the internal systems can be accessed through the internal network. In the case of user management the IDs are specific for continuous tracking and there are no general users for minor work, etc. In the responsibilities of users, although their commitments are defined, it is not really possible to follow up on their correct use of the facilities or the access they are given. And although the control of access to systems and applications tries to raise the perception of this control, there are no utilities with privileges, but only types of users who will be identified to perform their tasks. Therefore, this control must be considered for an audit and improvement process.
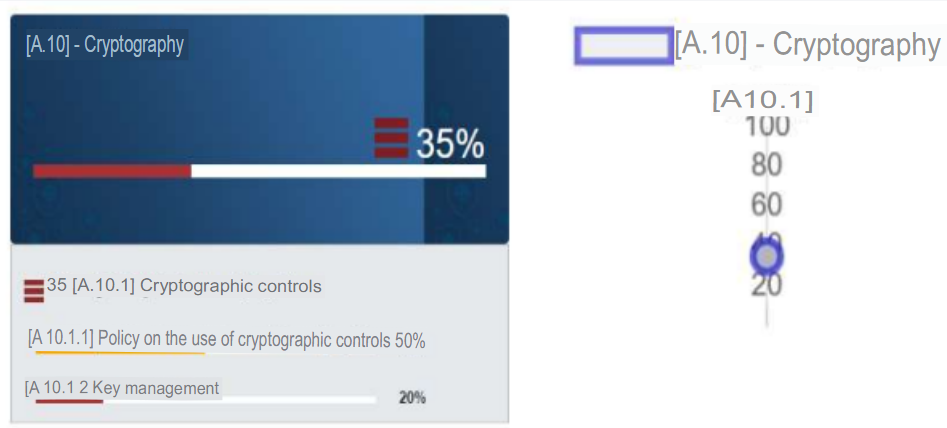
f. A.10 - Cryptography
In terms of compliance with the objectives, cryptography represents the lowest figure obtained (35%). The policy of use of cryptographic controls is based on the hashing of passwords so that they cannot be recovered by a reverse method. While in the case of key management, there are no secure methods or procedures to ensure the reliability of key management. So this should be one of the primary controls to be addressed to comply with the standard.
3.2. General Kiwiat Controls Analysis
To summarize the information presented, we will give a brief general summary of each control that was developed, so we can concisely explain the current situation of the company.
The Information Security Management Guidelines: Control 5, establishes that the control of information security policies is moderately implemented, since they are partially supported by management, but are not well communicated to new users or periodically reviewed.
Information Security Organization: Control 6, security policies were not established for specific roles and there is no adequate segregation of duties. At the same time, relevant security information is not constantly updated.
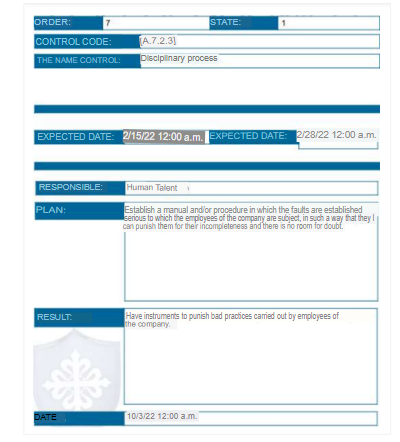
Security linked to human resources: Control 7, there is no awareness of information leakage or properly implemented disciplinary processes.
Asset management: Control 8, assets are managed but not in the best way, there is no correct handling of information and there is no management of removable media.
Access control: Control 9, there are no policies on principles of necessity and user management is by unique ID’s, there is no correct handling of information and there is no management of removable media. management is based on unique IDs; it is not possible to verify that access to the facilities is correctly delimited or to ensure their security, since all clients and workers are constantly moving around the facilities. movement through the facilities.
Cryptography: Control 10, there is no mechanism to guarantee security by restricting access to encrypted information, nor were policies established to ensure confidentiality.
4. Threat categorization
For the categorization of threats, threats that do not have a very low probability of occurrence will be used, but since we have 2 by default, which are natural disasters and unintentional errors and failures generated by the eMarisma tool itself, we will leave aside the unintentional errors and failures, since the city of Cusco has several months where rain is common.
| Code Type | Threat Code | Type Threat | Name Threat | Probability Occurrence | Percentage Degradation | Selected | ||
|---|---|---|---|---|---|---|---|---|
| [A] | Intentional attacks | [A.14] | Interception of information (eavesdropping) | High | (80.0%) | Medium | (60.0%) | Yes |
| [A] | Deliberate attacks | [A.15] | Deliberate modification of information | High | (80.0%) | Low | (40.0%) | Yes |
| [A] | Intentional attacks | [A.18] | Destruction of information | High | (80.0%) | Very Low | (20.0%) | Yes |
| [A] | Intentional attacks | [A.19] | Disclosure of information | High | (80.0%) | High | (80.0%) | Yes |
| [A] | Intentional attacks | [A.24] | Denial of Service | High | (80.0%) | Very Low | (20.0%) | Yes |
| [A] | Intentional attacks | [A.28] | Unavailability of personnel | High | (80.0%) | Low | (40.0%) | Yes |
| [A] | Intentional attacks | [A.30] | Social engineering (picaresque) | High | (80.0%) | Low | (40.0%) | Yes |
| [A] | Intentional attacks | [A.5] | Impersonation of user identity | High | (80.0%) | Low | (40.0%) | Yes |
| [N] | Natural Disasters | [N.2] | Water Damage | High | (80.0%) | Very Low | (20.0%) | Yes |
In the current activity we will consider 3 main factors of the 5 existing factors for the assetsXthreats; which are: Confidentiality, Availability and Integrity. Therefore, we will The threats chosen on the basis of the group’s criteria will be discussed.
Threat 1: Information Disclosure
As explained in point 2.1, one of the most important assets for organizations in the hospitality industry is guest information, this information can be very sensitive as it may contain too much guest information and if obtained by third parties can cost the reputation of the organization. The information records can contain personal numbers, email, health conditions, who they stay with, etc. Because of this it is considered the most important asset for this line of business. The consideration of the eMarisma tool is that this control has a value of 80% in confidentiality.
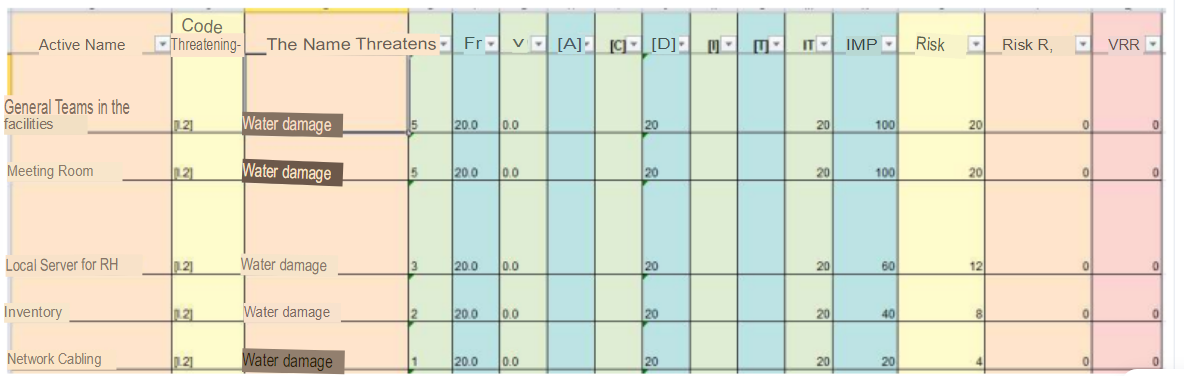
Threat 2: Water damage
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [N.2] | Water Damage | [HW] | General Equipment in facilities. | This is the equipment found in the organization, which is used to verify records and process requests | High (80.0%) | - | - | 20 | - | - |
| [N.2] | Water damage | [L] | Meeting Room | In this area users can connect and hold conferences | High (80.0%) | - | - | 20 | - | - |
| [N.2] | Water damage | [AUX] | Inventory | Peripheral equipment and auxiliary cables to keep hardware failures to a minimum | High (80.0%) | - | - | 20 | - | - |
| [N.2] | Water damage | [L] | Network cabling | Cabling Wiring of all rooms, Reception and Business Center | High (80.0%) | - | - | 20 | - | - |
| [N.2] | Water damage | [HW] | Local HR | Server Local rack server for HR software, which is in charge of workload management and attendance recording | High (80.0%) | - | - | 20 | - | - |
In the city of Cusco, the rainy season lasts approximately 7 months, from September to April. Although the equipment may be properly protected, it is not 100% certain that the facilities can provide total security for all the equipment, thus causing failures due to leaks to occur. Although the probability of occurrence is very high, the degree of degradation is low because certain minor equipment can be replaced, in the assets where this would most affect guests and staff are: Local Server for HR and the Meeting Room, this because without the local server it is not possible to work normally and for the case of the meeting room it can generate inconvenience for guests. The degradation percentage is 20% and is given in availability.
Threat 3: Information Interception (eavesdropping)
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.14] | Information interception (eavesdropping) | [COM] | Routers and Switches | All connection equipment such as routers and switches in the Belmond Monasterio Hotel. | Medium (60.0%) | 60 |
Having a network for guests does not ensure that any of them can activate a sniffing program on the network and then disclose the information of other guests. If this were to happen, the responsibility would be entirely that of the hotel, taking into account the corresponding legal considerations and the prestige of the organization at stake. The probability of occurrence is medium level 60% and the percentage of degradation is 60% in confidentiality.
Threat 4: Equipment tampering
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.23] | Handling of equipment | [HW] | General equipment on the premises. | This is the equipment found in the organization, which is used to verify records and to process requests | Medium (60.0%) | 40 | 40 | |||
| [A.23] | Equipment handling | [AUX] | Inventory | Peripheral equipment and auxiliary cables to keep hardware failures to a minimum | Medium (60.0%) | 40 | 40 | |||
| [A.23] | Equipment handling | [HW] | Local HR server | Local rack-type server for HR software, which is in charge of workload management and attendance recording | Medium (60.0%) | 40 | 40 |
It is not possible to ensure that the equipment provided to the personnel can be exchanged among them, lent to relatives (teleworking) and even the accesses that were saved by their own cellular equipment end up in the hands of people outside the business. Therefore, the average occurrence is considered medium level with a value of 60% and the average degradation of 40% distributed in 40% of confidentiality and 40% of availability.
Threat 5: Social Engineering
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.30] | Social engineering (picaresque) | [P] | Systems Technical Staff | This staff is responsible for providing technical support for facilities and troubleshooting minor systems problems | Medium (60.0%) | 40 | 40 | 40 |
Social engineering may occur to the technical systems personnel hired to support and maintain the equipment, since they are assigned passwords and users, but it is not possible to ensure the maintenance of the personnel for an indefinite period, so if social engineering is applied to them and since passwords are not changed periodically after the personnel leaves, someone could try to access the systems through the wifi, posing as a guest. The probability of occurrence is an intermediate 60% and the probability of degradation is 40% distributed between confidentiality, availability and integrity of information.
Threat 6: Deliberate information modification
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.15] | Deliberate modification of information | [D] | Client Data | The registry of customers who stayed at the hotel | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [SW] | Itinerary application | Application where guests can review their itinerary and reservations | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [L] | Meeting Room | In this area users can connect and hold their conferences | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [SW] | HR Management System | This system keeps track of the work attendance of the organization’s personnel | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [S] | Cloud server | The Belmond LTD organization owns a private PaaS type cloud server, which is assigned to each hotel in the world. This service is responsible for collecting all the information from all areas, staff and customers, for a subsequent CRM | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [S] | Cooking Class Application. | An application for cooking classes where users can access with a user name and password assigned to them, so that they can see the dishes they prepare, their equivalents, nutritional table and steps to follow in their respective source languages | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [S] | Pisco Tasting | An application for the tasting of pisco (Peruvian liquor) where users can access with a username and password that is assigned to them, so that they can see the cocktails they prepare with the ingredients, their equivalences, nutritional table and steps to follow in their respective languages of origin. | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [SW] | Restaurant Reservation Application | The Belmond Monasterio Hotel has a separate application to make reservations in its restaurants. Whether someone is a guest or not of the hotel | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [D] | Personal Data | Personal information of Belmond Monasterio Hotel employees: DNI, first and last names, telephone, cell phone, salary, workload, etc. | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [L] | Network cabling | Wiring of all rooms, Reception and Business Center | Low (40.0%) | 40 | ||||
| [A.15] | Deliberate modification of information | [COM] | Routers and Switches | All connection equipment such as Routers and Switches in the Belmond Monasterio Hotel | Low (40.0%) | 40 |
It could be the case that an annoyed worker, before resigning from the company, could make some modification to the information, causing This could cause problems with the integrity of the information. This depending on the level could occur in 10 of the 15 assets, the probability of occurrence is low with 40% and the percentage of degradation is 40%, distributed in integrity, integrity of information and integrity of information.
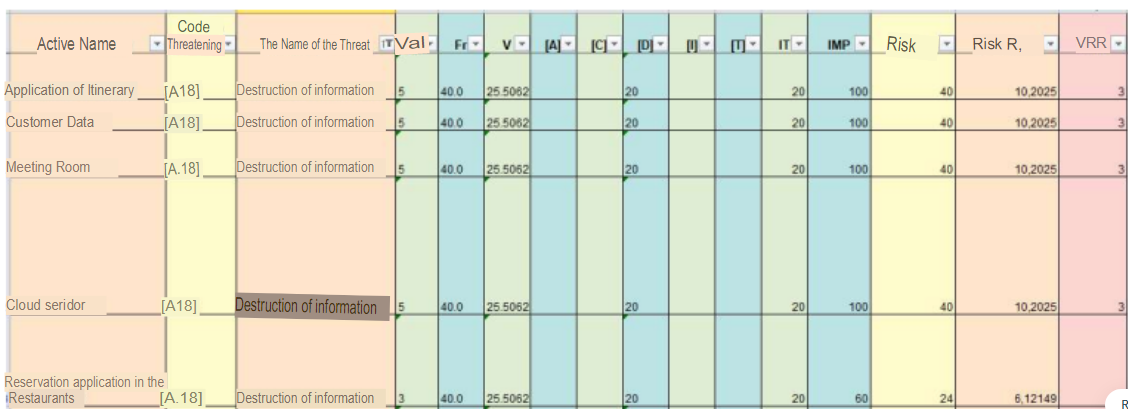
Threat 7: Destruction of information
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.18] | Destruction of information | [D] | Customer Data | The record of customers who stayed at the hotel | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [SW] | Itinerary Application | Application where guests can check their itinerary and reservations | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [L] | Meeting Room | In this area users can connect and hold conferences | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [SW] | HR Management System | This system keeps track of the work attendance of the organization’s personnel | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [S] | Cloud server | The Belmond LTD organization has a private PaaS cloud server, which is assigned to each hotel in the world.This service is in charge of collecting all the information from all areas, staff and customers, for a subsequent CRM | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [S] | Cooking Classes | Application An application for cooking classes where users can access with a username and password that is assigned to them, so they can see the dishes they prepare, their equivalents, nutritional table and steps to follow in their respective source languages | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [S] | Pisco Tasting | An application for the tasting of pisco (liquor of Peruvian origin) where users can access with a user name and password assigned to them, so that they can see the cocktails they prepare with the ingredients, their equivalences, nutritional table and steps to follow in their respective languages of origin. | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [SW] | Restaurant Reservation Application | The Belmond Monasterio Hotel has a separate application for making reservations in its restaurants. Whether someone is a guest or not of the hotel | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [D] | Personal Data | Personal information of Hotel Belmond Monasterio employees ID number, first and last names, telephone number, cell phone number, salary, workload, etc. | Low (40.0%) | 20 | ||||
| [A.18] | Destruction of information | [L] | Network cabling | Cabling of all rooms, Reception and Business Center | Low (40.0%) | 20 |
As in the previous case, it could happen that some annoyed worker, before resigning from the company, could destroy the information, causing The information could be destroyed, causing information integrity problems. This depending on the level could occur in 10 of the 15 assets, the probability of occurrence is low with 40% and the percentage of degradation is 20% distributed in availability.
Threat 8: Destructive Attack
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.26] | Destructive attack | [HW] | General equipment on the premises This is the equipment found in the organization, which is used to verify records and process requests | Low (40.0%) | 20 | |||||
| [A.26] | Destructive attack | [L] | Meeting room In this area users can connect and hold conferences | Low (40.0%) | 20 | |||||
| [A.26] | Destructive attack | [AUX] | Inventory Peripheral equipment and auxiliary cables to keep hardware failures to a minimum | Low (40.0%) | 20 | |||||
| [A.26] | Destructive attack | [L] | Network cabling Cabling of all rooms, Front Desk and Business Center | Low (40.0%) | 20 | |||||
| [A.26] | Destructive Attack | [HW] | Local HR Server Local rack server for HR software, which is responsible for workload management and attendance recording | Low (40.0%) | 20 |
This threat can be perpetrated by internal personnel, by people outside the Organization or by people hired on a temporary basis from the Organization. This threat can be perpetrated by internal personnel, by people outside the organization or by people hired on a temporary basis from the organization’s internal network or through access to the web page. access to the web page. The probability of occurrence is 40% and the percentage of degradation is 20% in availability. is 20% in availability.
Threat 9: Staff Unavailability
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.28] | Unavailability of personnel | [P] | Technical Systems Personnel | This personnel is in charge of providing technical support for the facilities and solving minor systems problems | Low (40.0%) | 40 |
As mentioned in the description of the controls, the most important personnel is the Head of Engineering. Engineering Manager, so his presence is necessary for certain tasks, and his absence can lead to a bad outcome. can lead to a bad performance of the organization. The probability of occurrence is The probability of occurrence is 40% and the probability of degradation is 40% in availability.
Threat 10: User impersonation
| Code Threat | Name Threat | Type Active | Name Active | Description Active | P. of Occurrence | [A] | [C] | [D] | [I] | [T] |
|---|---|---|---|---|---|---|---|---|---|---|
| [A.5] | User identity spoofing | [D] | Customer Data | The record of customers who stayed at the hotel | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [SW] | Itinerary Application | Application where guests can check their itinerary and reservations | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [SW] | HR Management System | This system keeps track of the work attendance of the organization’s staff | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [S] | Cloud server | The Belmond LTD organization owns a private PaaS cloud server, which is assigned to each hotel in the world. This service is in charge of collecting all the information from all areas, staff and customers, for a subsequent CRM | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [S] | Cooking Classes Application | An application for cooking classes where users can access with a username and password that is assigned to them, so that they can see the dishes they prepare, their equivalents, nutritional table and steps to follow in their respective source languages | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [S] | Pisco Tasting | An application for the tasting of pisco (Peruvian origin liquor) where users can access with a user name and password assigned to them, so that they can see the cocktails they prepare with the ingredients, their equivalences, nutritional table and steps to follow in their respective languages of origin. | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [SW] | Restaurant Reservation Application | The Belmond Monasterio Hotel has a separate application for making reservations in its restaurants. Whether someone is a guest or not of the hotel | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [D] | Personal Data | Personal information of Belmond Monasterio Hotel employees ID number, first and last names, telephone number, cell phone number, salary, workload, etc. | Low (40.0%) | 40 | 40 | 40 | 40 | |
| [A.5] | User identity spoofing | [COM] | Routers and Switches | All connection equipment such as routers and switches in the Hotel Belmond Monasterio. | Low (40.0%) | 40 | 40 | 40 | 40 |
The impersonation of a user with a specific role is a concern because the different accesses have certain levels of role, so that a user providing user and password information to another colleague can lead to information leakage, damage to the integrity of the information and the sale of these accesses to third parties. Therefore, although this threat has a low probability of 40%, it has a 40% probability of degradation in confidentiality and integrity (authenticity is not considered for this work).
I recommend to attach this document https://pilar.ccncert.cni.es/index.php/docman/documentos/2-magerit-v3-libro-ii-catalogo-de-elementos/file to better understand and read the values within the eMarisma audit.
5. Risk Analysis.
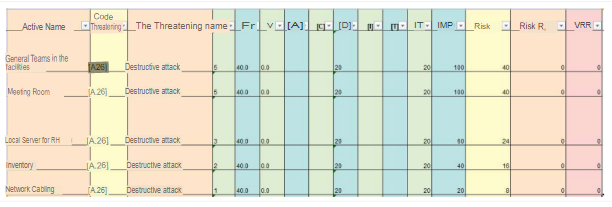
The respective threats to which the information assets are exposed will be analyzed. assets will be grouped by the same type of threat, the current condition in which the Belmond Hotel maintains the asset will be described and in each case the reasons for the threat will be established. the current condition in which the Belmond Hotel maintains the asset and will establish in each case the reasons for the which they obtained their Risk Value rating will be established in each case. Threat: Destructive attack Risk: Loss of availability due to destructive attack to information assets.
Asset status:
- General computer equipment, threat “Destructive attack”, on this asset we can identify that the frequency of occurrence of the threat is medium 40, the availability affectation value is low 20, the impact is 100, being so the current controls are being effective since the risk is being mitigated adequately, therefore the asset is not at risk resulting in a VRR 0, additionally we could add that there is a backup of the information assets and that there is a backup of the information assets. additionally we could add that there is backup of the information in network folder and contingency computer contingency computers that can be moved to the places where this risk materializes. this risk materializes.
- Meeting rooms, threat “Destructive attack”, on this asset we can identify that the frequency of occurrence of the threat is medium 40. that the frequency of occurrence of the threat is medium 40, the value of availability is low 20, the impact is 100. the impact is 100, thus the current controls are being effective since the risk is being mitigated adequately. effective since the risk is being mitigated in an adequate manner, therefore the asset is not at risk, resulting in a risk, resulting in a VRR 0, additionally we could add that there is an access control system in place to control access to the asset. access control system by card, protocol of delivery and return of rooms, security doors, and security and return protocol, security doors, and closed-circuit surveillance to restrict access to unauthorized users who could access to unauthorized users who may attempt against the furniture or videoconferencing equipment.
- Local Server for HR, “Destructive attack” threat. the frequency of occurrence of the threat is medium 40, the value of impact on availability is low 40, the impact on vailability is low 20, the impact of the threat is low 20.the impact is 100, thus the current controls are being effective since we are mitigating the threat.The current controls are being effective since the risk is being adequately mitigated, therefore the asset is not at risk resulting in a VRR 0, additionally we could add that there is an equipment room with security door, biometric fingerprint access, the room where it is located is located in an access area restricted only to systems personnel.
Threat: Water Damage (Industrial Origin) Risk: Loss of availability due to water damage to information assets.
Asset status:
- General computer equipment, threat Water damage (Industrial origin), on this asset we can identify that the frequency of occurrence of the threat is low 20, the availability affectation value is low 20, the impact is 100, being so the current controls are being effective and the risk is being mitigated adequately, Therefore the asset is not at risk resulting in a VRR 0, additionally we could add that the computer equipment has been installed in areas away from water pipe crossings, the equipment is installed in suitable furniture that allows them to be exposed.
- Meeting rooms, threat Water damage (Industrial origin), on this asset we can identify that the frequency of occurrence of the threat is low 20, the value of availability affectation is low 20, the impact is 100, thus the current controls are being effective and the risk is being mitigated adequately, therefore the asset is not at risk resulting in a VRR 0, additionally we could add that the meeting room is located far from water pipes, but it is next to a bathroom, which could generate a leak that could affect the floor of the meeting room.
- Local Server for HR, threat Water Damage (Industrial Origin), on this asset we can identify that the frequency of occurrence of the threat is low 20, the value of availability affectation is low 20, the impact is 60, thus the current controls are being effective and the risk is being mitigated adequately, Therefore the asset is not at risk resulting in a VRR 0, additionally we could add that the server is located in a computer room through which no water pipes pass but is adjacent to a bathroom which could generate a leak that could affect the server.
- Inventory, threat Water damage (Industrial origin), on this asset we can identify that the frequency of occurrence of the threat is low 20, the value of affectation of availability is low 20, the impact is 40, thus the current controls are being effective and the risk is being mitigated adequately, therefore the asset is not at risk resulting in a VRR 0, additionally we could add that there is a physical inventory located in an administrative area of the hotel, could be affected if the fire extinguishing system is activated.
- Network cabling threat Water damage (Industrial origin), on this asset we can identify that the frequency of occurrence of the threat is low 20, the availability affectation value is low 20, the impact is 20, thus the current controls are being effective and the risk is being mitigated adequately, Therefore, the asset is not at risk, resulting in a VRR of 0. Additionally, we could add that measures have been taken to prevent the data network from being far from the water pipes, but at some point the fire extinguishing system could be activated and partially wet the cabling network.
Threat: Destruction of information. Risk: Loss of availability due to data destruction.
Asset status:
- Itinerary application, Destruction of information, on this asset we can identify that the frequency of occurrence of the threat is medium 40, the availability affectation value is low 20, the impact is 100, being so the current controls can be improved, the risk is being mitigated but not enough, therefore the asset requires improvement or implementation of new controls to reduce the VRR 3, Additionally we could add that the application of itinerary, reservations, checkin, contains the history of all hotel customers, there are backup copies of the database, some stored externally, if a computer crime erased the database would prevent the validation of the data generating discomfort for users and difficulty in their attention.
- Customer data, Destruction of information, on this asset we can identify that the frequency of occurrence of the threat is medium 40, the value of availability affectation is low 20, the impact is 100, thus current controls can be improved, the risk is being mitigated but not enough, therefore the asset requires improvement or implementation of new controls to reduce the VRR 3, Additionally, we could add that there are customer databases in the hotel’s information system, and also in databases scattered in the equipment of the administrative staff, there are backups of this information in external custody, the destruction of customer data would generate setbacks for the proper provision of the service of the Belmond Hotel.
- Meeting room, Destruction of information, on this asset we can identify that the frequency of occurrence of the threat is medium 40, the availability affectation value is low 20, the impact is 100, thus the current controls can be improved, the risk is being mitigated but not enough, therefore the asset requires improvement or implementation of new controls to reduce the VRR 3, additionally we could add that, there is configuration information of the meeting room equipment, equipment manuals, architectural plans, audio-visual equipment warranties, if any type of related information were to be destroyed it would be very difficult to manage warranties, make changes in the room design, make new configurations in the room and the availability time of the room would be reduced.
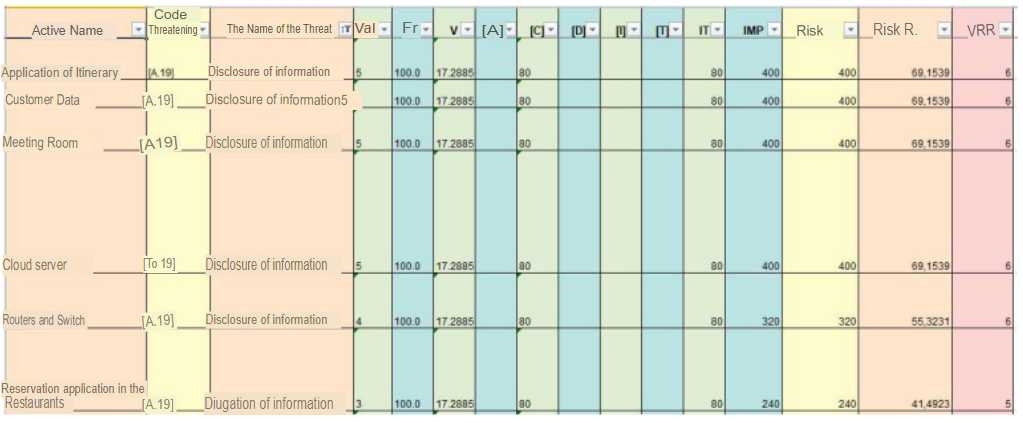
Threat: Disclosure of information. Risk: Loss of confidentiality due to disclosure of information.
Status of the asset:
- Itinerary application, Disclosure of information, on this asset we can identify that the frequency of occurrence of the threat is high 100, the value of affectation of confidentiality is high 80, the impact is 400, being so the current controls requires to be reviewed, risk mitigation is not being effective, therefore the asset requires to improve or implement new controls to reduce the VRR 6, additionally we could add that the application of itinerary, reservations, checkin, contains the history of all customers of the hotel, There are backup copies of the database, some of which are kept externally, there is a double authentication system for access to the information system database, a strategy has been created so that employees who require customer data export the minimum amount necessary, so that if a database is compromised, 100% of the customers’ information will not be revealed, the staff has been trained to work on information displayed from the system and not to download data unless strictly necessary.
- Customer data, Disclosure of information, on this asset we can identify that the frequency of occurrence of the threat is high 100, the value of affectation of confidentiality is high 80, the impact is 400, thus the current controls need to be reviewed, risk mitigation is not being effective, therefore the asset requires improving or implementing new controls to reduce the VRR 6, additionally we could add that, there are customer databases that reside in the hotel information system, and also in scattered bases in the equipment of administrative staff, There are backups of this information in external custody, the disks of the computer equipment of the administrative areas of the hotel have been encrypted in such a way that if they are extracted from the area the information cannot be read without the cryptographic key, a strategy has been created so that the workers who require customer data export the minimum amount necessary, In this way, if a database is compromised, 100% of the clients’ information will not be revealed. Personnel have been trained to work on information visualized from the system and not to download data unless it is strictly necessary.
- Meeting room, Disclosure of information, on this asset we can identify that the frequency of occurrence of the threat is high 100, the value of affectation of confidentiality is high 80, the impact is 400, thus the current controls need to be reviewed, risk mitigation is not being effective, therefore the asset requires improvement or implementation of new controls to reduce the VRR 6, additionally we could add that the meeting room is constantly reviewed to prevent the existence of video cameras or audio recorders of people who want to extract confidential information, access to the meeting room is authorized by electronic card, in the periphery of the meeting room is prohibited access of staff.
- Cloud Server, Disclosure of information, on this asset we can identify that the frequency of occurrence of the threat is high 100, the value of affectation of confidentiality is high 80, the impact is 400, thus the current controls need to be reviewed, risk mitigation is not being effective, therefore the asset requires improving or implementing new controls to reduce the VRR 6, additionally we could add that there is a contract with the cloud computing service provider with clauses that guarantee minimum levels of computer security, the cloud resources are protected by several protection mechanisms of recognized manufacturers but as the administration is shared IT staff of the hotel are also responsible for the information contained in the cloud computing service.
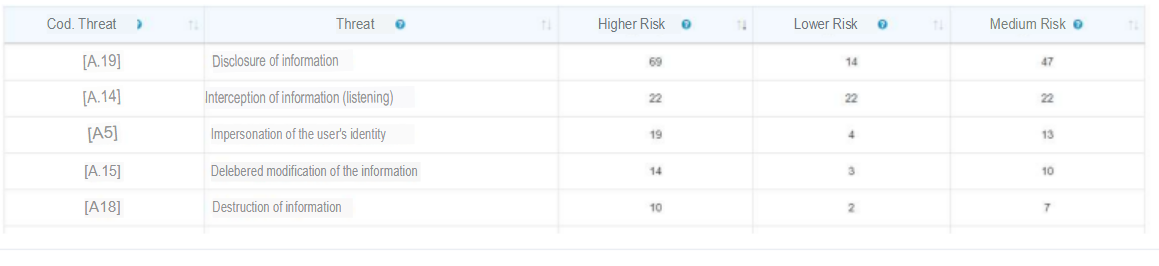
Threats Risks
According to the above table generated in the eMarisma tool we can see that the top 5 risks faced by the Belmond Hotel are the following:
Information Disclosure, Information Interception, User ID Impersonation, Deliberate modification of information and Destruction of information, with this information we can generate shock plans that allow us to focus the effort to mitigate the risks to which we are more susceptible, also by attacking these threats we can positively affect the indicators.
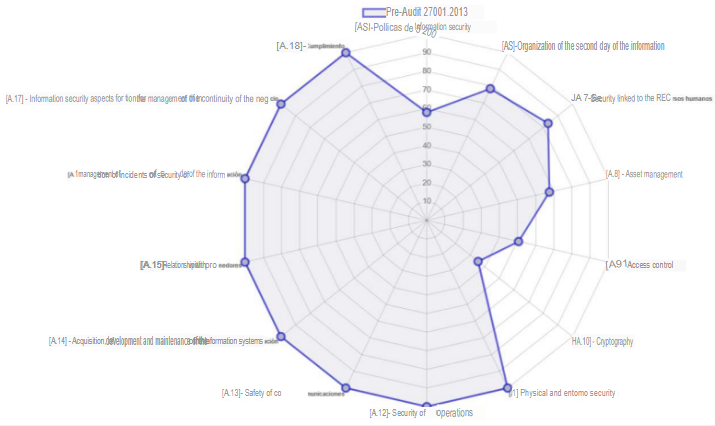
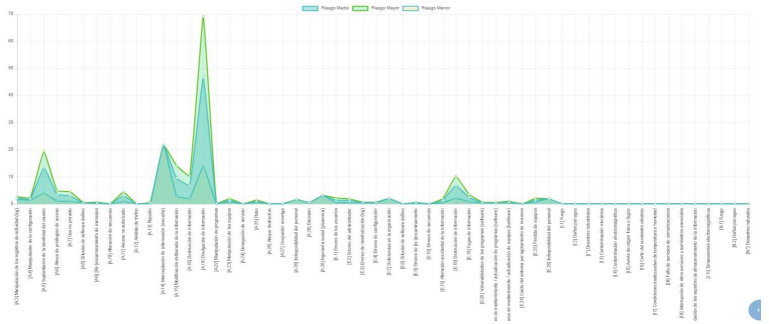
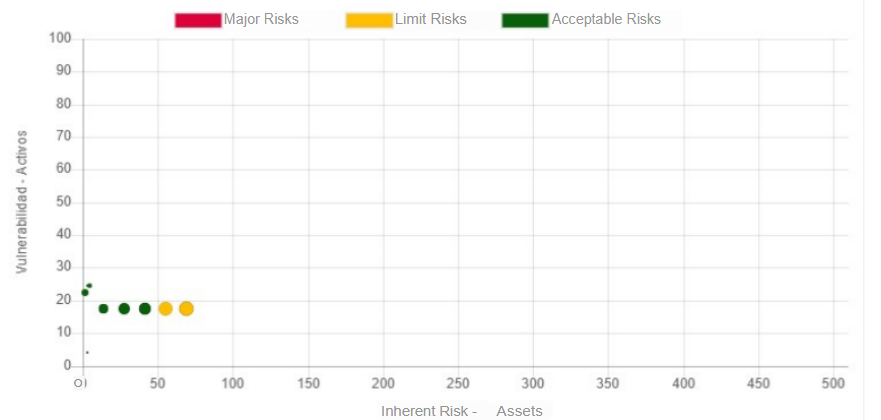
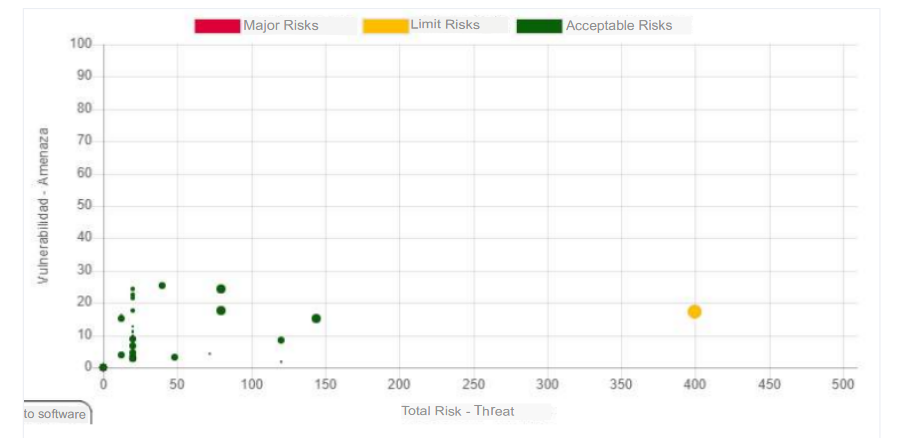
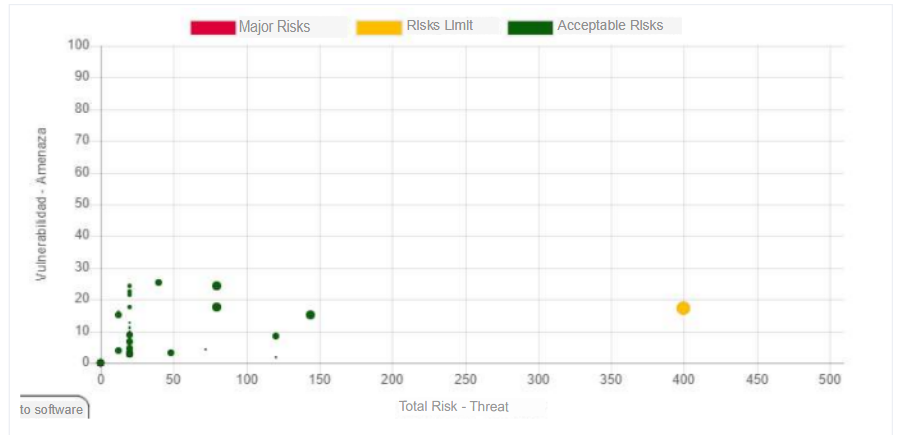
Behavior of the number of risks by type of hazard. Risk Map
In the previous graph we can see that the vulnerabilities of our assets are concentrated in a risk below 80 and that there are very few assets that exceed this threshold, before the application of controls.
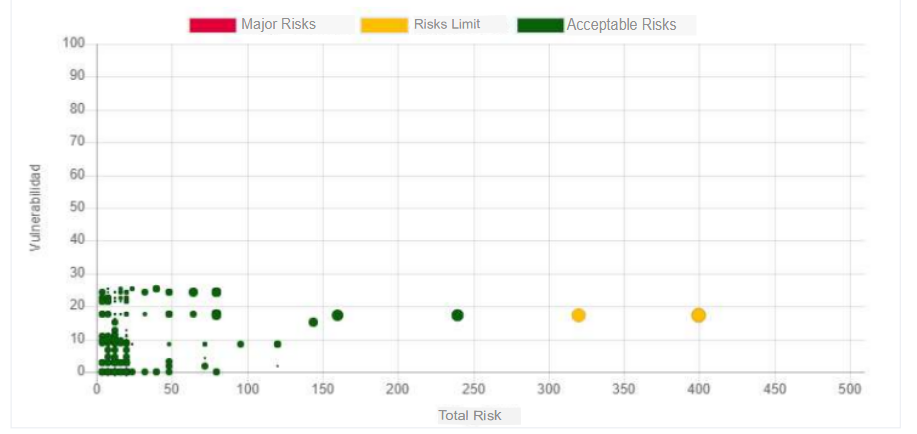
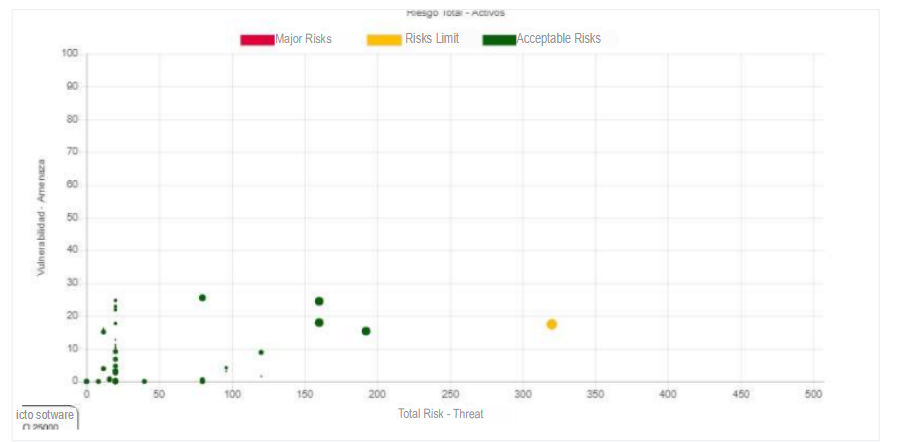
In the previous graph we can see that most of the assets were able to mitigate the risk, the more points we see above zero means that the better the controls have been applied, in this case we must work on the assets with inherent risk.
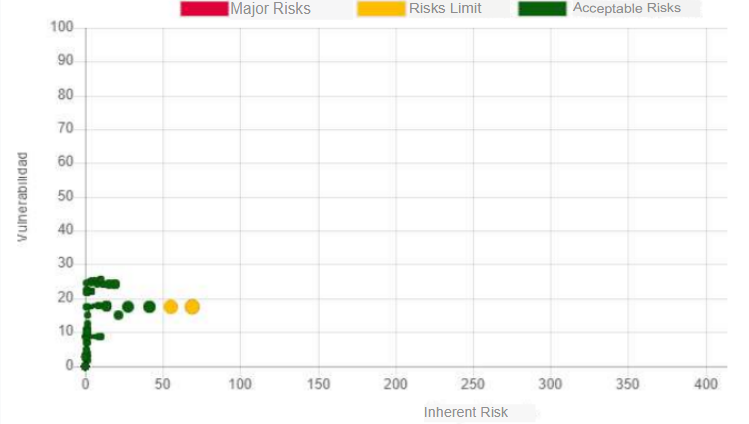
In the previous graph we can see a good behavior of the vulnerabilities prior to the application of controls.
In the previous graph we can see the behavior of vulnerabilities after the application of controls.
In the previous graph we can see the behavior of the risk value against the number of vulnerabilities that share that risk before controls, for this case we can see that there are about 18 vulnerabilities with a total risk of 400, this is a value that comes out of the general behavior.
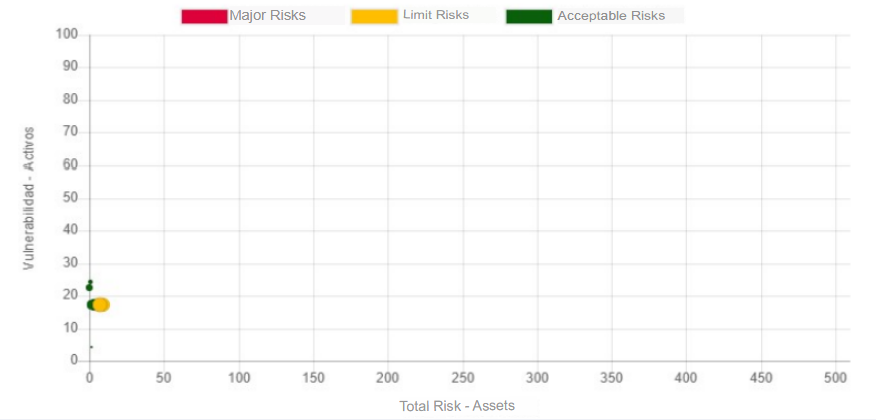
In the previous graph we can see the number of vulnerabilities after the application of controls.
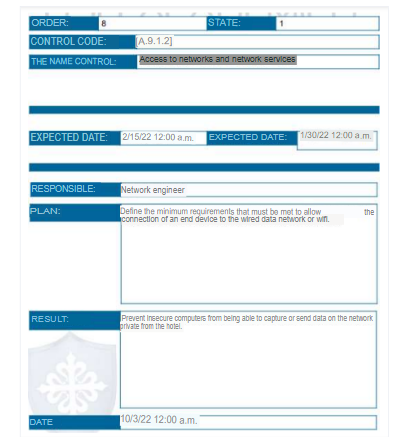
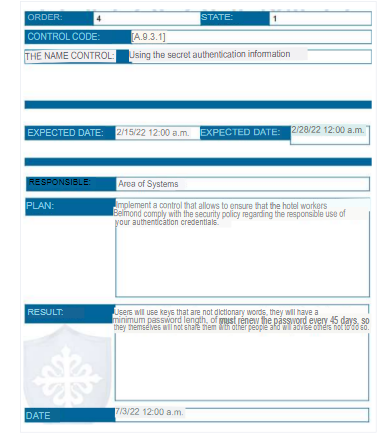
6. Risk treatment plan
Below is the risk treatment plan generated by the eMarisma tool.
7. Security Incident Analysis
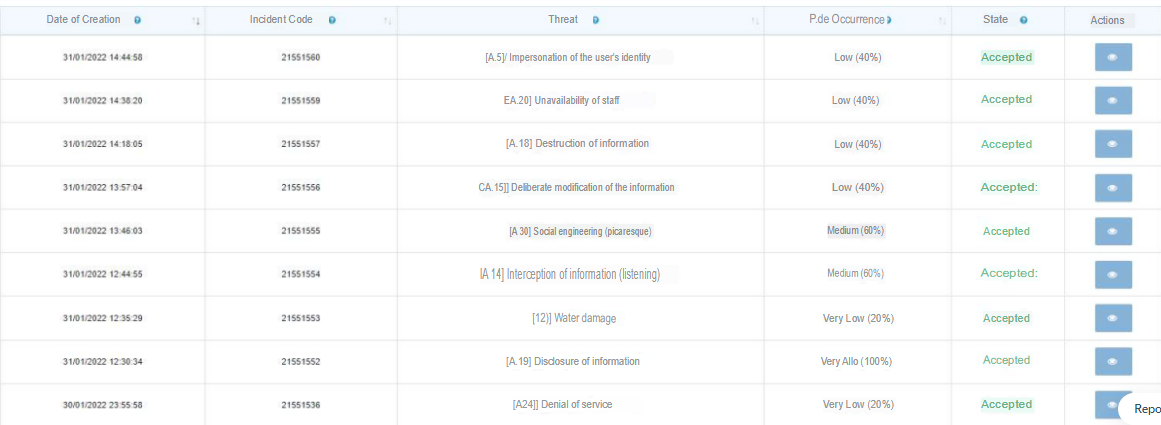
To begin the analysis of security incidents it is necessary to load the incidents in the eMarisma tool, for each incident we will add a possible solution and the person responsible for the incident, a conclusion will also be made to establish if the proposed solution is adequate, the export generated by the process will be shown below.
| Code | Opening Date | Responsible | Description | Cause | Solution | Conclusion |
|---|---|---|---|---|---|---|
| 21551536 | 01/31/2022 | Infrastructure Engineer | The cloud server is where the Hotel’s information system runs | Failure in the dedicated channel, access to the Cloud server is lost | Add a second dedicated data channel | Adding another data channel will increase the availability percentage since it will be possible to access the server if one of the channels is offline. |
| 21551552 | 01/31/2022 | Human Talent Staff Human | Talent staff mistakenly sent the salary assignment data of all hotel employees to all employees, causing discomfort between them and the administration. | In a mail merge process an erroneous selection of data was made, which caused the outgoing mail to include the payroll information of all employees. | Establish a continuous training process for the tools used by the company’s employees. | This incident did not have economic repercussions, but it did cast doubt on the rigorousness with which the hotel’s employee data is processed. |
| 21551553 | 01/31/2022 | Head of maintenance | Failure to regularly clean the rainwater gutters led to a clog in one of the downspouts, which caused water to overflow and stagnate on one of the hotel roofs; when the water overflowed, it took a different path than expected, causing a leak that damaged one of the computer equipment in a box on the upper floors. | Lack of maintenance of rainwater gutters and downspouts. | Include in the maintenance personnel’s activity schedules the cleaning of rainwater downspouts. | Failure to implement adequate control resulted in a leak that affected a computer equipment; if this control had been included, this vulnerability would not have been exploited. |
| 21551554 | 01/31/2022 | Infrastructure Engineer | At a convention of companies in the energy sector, a hacker undercover as an occasional tourist took the opportunity to enter the hotel’s Wifi network and sniff communications, one of the businessmen used a laptop that did not have the windows Update service active, which allowed the hacker to steal his information. | A client did not follow the recommendations provided by the hotel for secure network access. | 1. A control will be implemented to warn all users of the hotel network of the risks to which they are exposed by using a shared use network. 2. An authentication control will be implemented to prevent the use of passwords with no expiration date. | Reputational damage was caused to the hotel because when this event occurred, clients associated the Belmond Hotel as an unsafe place to hold their meetings, seminars and conferences. This could have been avoided by better informing clients that the networks that the hot el has at its disposal are for shared use, that they subscribe to a policy of use and that it is also the responsibility of the users to keep their information protected. |
| 21551555 | 01/31/2022 | Technology Process | A fraudster posing as a hotel biller got the system administrator to cancel several charges that had been made by a customer during his stay at the hotel. | The system administrator did not correctly validate the fraudster’s identity. | A coordinate card system is implemented to improve the privilege validation process, so that staff requiring changes to billable items will have to provide these numbers to ensure that the orders come from authorized personnel. | In the absence of mechanisms to verify the identity of employees requesting telephone support, it was very easy to carry out social engineering attacks. Due to the size of the Belmond Hotel, it is necessary to implement more efficient access controls since the hotel relies heavily on billing for all services to keep the hotel in operation. |
| 21551556 | 01/31/2022 | Billing | A biller invited a friend to spend a stay at the hotel, and intentionally changed the amount of services his friend had requested, causing economic damage to the hotel. | There is no control to establish if there is a match between what is provided in the restaurant and the soda fountain and what is billed. | Integrate the ordering system to the restaurant and the soda fountain, so that from these areas it is recorded on the invoice if the dishes or drinks went out and were included in the invoice. | As some areas of the hotel were not fully systematized, workers abused this vulnerability for their own benefit and did not invoice the totality of the consumption. |
| 21551557 | 01/31/2022 | Human Resources | A hotel employee in the payroll area deleted all the files on his computer because he found out he was going to be fired. | There is no control for periodic backups of users’ computers. | A backup strategy is implemented to ensure that all equipment in the administrative area is backed up regularly. | Not enough importance was given to the information handled by the employee until the day of his retirement, nor were controls implemented to prevent the intentional elimination of information. |
| 21551558 | 31/01/2022 | Infrastructure Engineer | In one of the hotel’s computers, the blocking of USB ports was not verified and one of the workers placed a USB memory stick containing a ransomware virus that was activated and erased all the information contained on the hard disk. | It is the duty of the systems personnel to verify that all USB ports on computer equipment are disabled; if this control was not carried out correctly, one computer was used to copy information to USB and was infected by a virus that used this vector. | Generate a control that allows periodic verification of the activity status of the USB ports of all the hotel’s computer equipment. | There is a system for disabling USB ports, but unfortunately the equipment that suffered the problem was not checked to see if the blocking system was working properly, which allowed the virus threat to materialize. |
| 21551559 | 01/31/2022 | Information System Administrator Engineer | During the last monthly closing, the engineer who manages the information system was incapacitated due to a health problem, and during the month’s financial closing there was a problem with some new developments that were not being loaded into the system, which caused an additional delay in the process | There was a change in the version of the application and the personnel performing the financial closing was not adequately trained in the new functionalities of the system, causing problems in the loading of information | A better structured training system will be implemented to enable workers to be able to solve low-difficulty problems by themselves so that they will not be dependent on support personnel all the time | By having more than one person within the company trained in the support of the information system, there will be less risk that the operation will be stopped due to the lack of one of them. |
| 21551560 | 01/31/2022 | Information system administrator | One of the hotel employees pretended to be the personnel administrator in order to change the shifts he had scheduled for the season in order to improve his salary conditions. | The identity of the user who was making the request was not properly validated, so it was assumed that the requests were valid. | A control is implemented through coordinate cards to validate the authenticity of the users to avoid unauthorized changes in the information. This validation will be performed by the system administrator each time an employee calls in and a change is required. | In the absence of proper identity verification requests made to the system administrator would affect to some degree billing or asset management processes creating dissatisfaction among employees and even users. |
Once the incidents have been registered, eMarisma using artificial intelligence algorithms will propose some adjustments to the Security Management System suggesting a change in the probability of occurrence of some of the incidents, in this case the suggestions will be accepted as long as we agree with them. The following image shows the suggestions provided by eMarisma.
The eMarisma tool will show us the controls that must be fine-tuned to maintain the levels of information security in the organization, for this we must select each one, select a range of dates of design and implementation, add the proposed plan and the expected result. The following images show the new exported treatment plan.
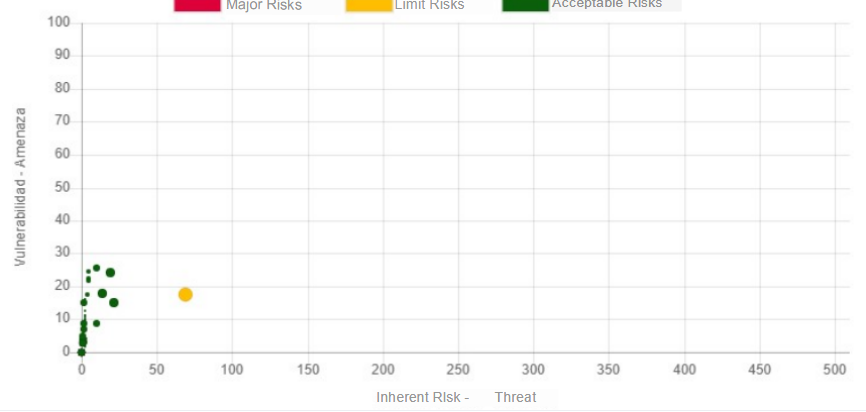
When reviewing the graphs we can observe that they have changed, for example the following graph that shows the vulnerabilities-threats by risk - threat
Before adding vulnerabilities
After adding incidences
We can observe a greater number of points in the last graph, which means that a greater number of threats have been mapped that had not been previously foreseen, additionally we can see that the risk value has been recalculated for each of them due to the implementation of new controls.
8. Conclusions
-
The vulnerability mitigation process is a cyclical process that is refined as we add information to our system, this generates iterations that require additional adjustments and may change our vision and management of information assets in the organization.
-
The Information Security Management System depends on the commitment of all the staff of the organization, we see that many treatment plans are the responsibility of a leader of a process or area, but if we talk about its execution this depends largely on the employees who are in the operation, and if they do not understand the value of information assets that protect the work done for the deployment of the ISMS will not generate added value.
-
Thanks to the generation of risk maps it is possible to establish the status of our security levels within the organization and detect through the graph which ISMS controls should be prioritized, this allows us to generate controls that have a much greater impact on security levels and thus obtain the expected results.
-
eMarisma is an application that allows us to model the status of the ISMS of our organization, but its potential cannot be fully exploited if quality data is not entered, it is required to make an analysis of each data that is loaded into the tool because when computed will affect the rating and display of vulnerabilities and risks that must be addressed with higher priority, therefore the understanding of ISO 27000, reading manuals and monitoring recommendations will allow a more accurate analysis of the data and results more in line with those required by organizations.
9. Bibliography
Alarcon, C., Montoya, D., & Zamalloa, J. (20 de Junio de 2014). MIRAFLORES PARK HOTEL. Obtenido de https://prezi.com/zslfatrgdspo/miraflores-park-hotel/
Bojanc, R., & Jerman-Blaznic, B. (25 de 2 de 2013). A Quantitative Model for Information-Security Risk Management. EMJ. Engineering Management Journal,
http://www.espaciotv.es:2048/referer/secretcode/scholarly-journals/quantitative-modelinformation-security-risk/docview/1434438214/se-2, 25-37.
CALLEJAS, N. T., & RODRIGUÉZ, A. F. (2018). AUDITORIA INTERNA A LOS ACTIVOS FÍSICOS DEL ÁREA DE TI EN LA UNIVERSIDAD COOPERATIVA DE COLOMBIA SEDE IBAGUÉ, APLICANDO EL ESTÁNDAR ISO/IEC 27002:2013. Obtenido de https://repository.ucc.edu.co/bitstream/20.500.12494/5037/2/Auditoria%20interna%20a%20los%20activos%20f%C3%ADsicos%20del%20%C3%A1rea%20TI%20en%20la%20Universidad.pdf
Gamboa, C. G. (2019). LA SATISFACCIÓN LABORAL Y SU RELACIÓN CON EL SERVICIO DE CALIDAD DE BELMOND PARA SUS TRENES PERURAIL VISTADOME EN LA RUTA: SAN PEDRO MACHUPICCHU-SAN PEDRO, AÑO 2019. Obtenido de https://repositorio.uandina.edu.pe/bitstream/handle/20.500.12557/3502/Cesar_Tesis_bachiller_2019.pdf?sequence=1&isAllowed=y
LVMH. (s.f.). Organigrama Belmond. Obtenido de
https://www.theofficialboard.es/organigrama/belmond#
navarro, c. q. (s.f.). HOTEL BELMOND MONASTERIO. Obtenido de
https://prezi.com/3nckjg0lcdva/hotel-belmond-monasterio/
Santos-Olmo Parra, A., Sánchez Cres, L., & Fernandez-Medina, P. (2020). Methodology for the Analysis of Risks on Information Systems, using Meta-Pattern and Adaptability (thesis. Escuela Superior de Informática.