ISO27001 - ISMS pre-audit Sample by Fernando

Contents
- 1 Introduction
- 2 Description of the company
- 3 Organizational chart
- 4 Project description
- 5 Emarisma tool records
- 6 Asset categorization
- 7 Controls analysis
- 8 SOA analysis
- 9 Conclusions
- Bibliography
1. Introduction
Because security requirements are increasingly present in today’s systems, standards were created which established guidelines that allow a data management to ensure that companies implement all appropriate controls on confidentiality, integrity and availability of information, so you can protect the information of stakeholders, which should be included as customers, employees, business partners and society in general is required to have a management of assets. This asset is called Information Security Management System (ISMS). This document was created in order to perform a pre-audit to the Belmond Hotel Monasterio organization in order to implement an ISMS, complying with the controls and domains established in the ISO 27001:2013 standard.
2. Company Description
The Belmond Hotel Monasterio is a luxury hotel (five stars) located in the city of Cusco, Peru. It has been established on the former premises of the Seminary of San Antonio Abad dating from the seventeenth century and is of Andean baroque style built on Inca walls. The hotel is located three hundred meters from the Plaza de Armas.
History
In 1598, the bishop of Cusco Antonio de Raya Navarrete founded, in accordance with the decrees of the Council of Trent, the Seminary of San Antonio Abad and granted its administration to the Society of Jesus. The purpose was to provide ecclesiastical education to young people who wanted to be part of the Church, mainly the sons of impoverished conquerors. The seminary was built on the walls of the old Amaru Qhata palace. The original building was destroyed by the earthquake of 1650 and in its reconstruction a chapel of Andean baroque style was built. In the middle of the 20th century, the Jesuits obtained authorization from Cardinal Richard Cushing, Archbishop of Boston, to build a new building, to which they moved in 1965.
Hotel
At that time, the seminary facilities were acquired and remodeled by the Peruvian state company Entur Perú to house the hotel. The building is currently considered a historical monument and has been part of Cusco’s Monumental Zone since 1972.1 Its façade still bears Spanish coats of arms and its chapel contains ancient frescoes of the Cuzco school in gold leaf frames. In the center of the hotel there is a cloister with a fountain and an ancient cedar tree that is 300 years old. The hotel also has a Peruvian restaurant and a bar.
The Hotel Monasterio was bought by the Sousa group after the privatization process of the state-owned Entur Peru in 1994 and opened its doors in CADE 1995. It was inaugurated after its restoration by Peruvian businessman Lorenzo Sousa Debarbieri, in 1995, who is considered the promoter of luxury tourism in Cusco, the Sacred Valley and Macchu Picchu. Since then, the Hotel Monasterio has been remodeled twice to update its rooms and common areas. It was the first hotel in Cusco to include supplemental oxygen in its rooms to lessen the effects of altitude on guests.
In 1999 the Orient-Express Hotels Ltd. hotel chain partnered with Lorenzo Sousa. Hotel Monasterio is now an equally owned consortium called Peru Orient Express Hotels SA with the participation of Lorenzo Sousa and his family as well as Belmond Ltd., and has won the most awards in the industry for Peruvian hotels over the past 15 years.
In 2014 the Hotel Monasterio was rebranded as Belmond Hotel Monasterio. This marked the rebranding of the Orient-Expressa Belmond Ltd. brand. In total there are 122 rooms and suites. Two restaurants, Lobby Bar and Deli Monasterio. Andean bath service in bathtub, massage room. Artistic tours, cooking classes and pisco lessons. Meeting rooms including the San Antonio Abad Chapel for weddings and business events.
(Additional comments: To meet the proposed requirements for the activity some assets will be added to reach the minimum of 15; In the same way there is no knowledge of the servers, services and infrastructure that owns this hotel so I will use resources such as linkedin where someone who worked in this hotel appears in this way could assume the technological resources that the organization has and as for the organization there is no organization chart so I will use a hybrid between the organization chart that was made for a work on a sister organization “Hotel Plaza Nazarenas”, “Hotel Belmond Miraflores Park” and the organization chart of the organization Belmond Limited).
The hotel is consistently recognized as one of the best in Peru. It has the following facilities:
- Meeting Room including the San Antonio Abad Chapel for weddings and business events, Andean Bath Service in bathtub, Massage Room, Spa, , SPA, Outdoor Swimming Pool.
- Two Restaurants, one with typical food and the other with Peruvian food.
- Lobby Bar
- Laundry service
- Recreational packages
List of Assets:
- Customer Data
- General Facility Equipment
- Itinerary Application
- Meeting Room
- HR Management System
- Technical Staff Systems
- Cloud Server
- Cooking Class Application
- Pisco Tasting
- Restaurant Reservations Application
- Personal Data
- Inventory
- Network Cabling
- Routers and Switches
- Local HR Server
Mission
Belmond Monasterio Hotel’s mission is “We open the door to a new world of places, people and travel. We express ourselves with personality, based on knowledge and a sense of place and purpose.” (Alarcon, Montoya, & Zamalloa, 2014)
Vision
The vision of Belmond Monasterio Hotel is “We bring together the charming, the unexpected, the authentic and the meaningful. We celebrate individuality, diversity and personality in each of our experiences. In an idyllic paradise with a traditional setting in the city of Cusco”. (Alarcon, Montoya, & Zamalloa, 2014)
Staff
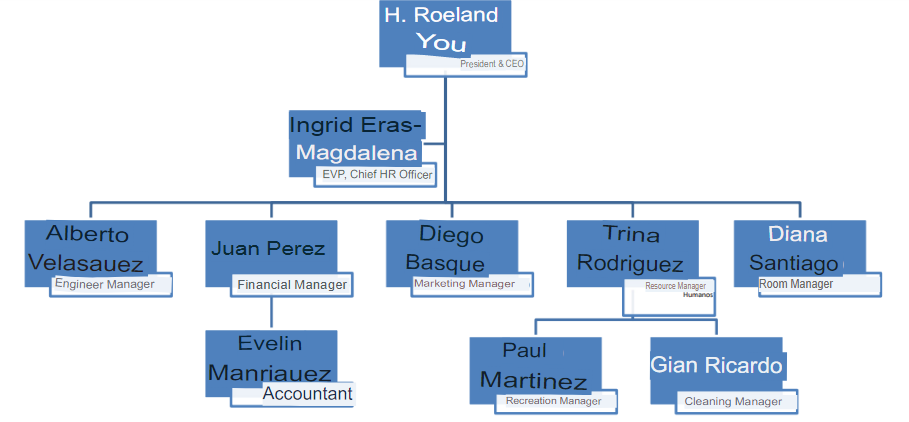
More than 125 people work at the hotel, and the Front Desk alone employs 20 people, 10 of whom work in shifts in Guest Services and Reception. The organizational structure is as follows:
(Disclaimer: The data, assets, services and many other considerations taken into account do not reflect the behavior, reality or structure of the company. It was simply mentioned to try to make a practical case and assumptions were made without any basis to meet the requirements of the activity.
- The considerations as services were taken by investigating the profile of a former employee of the company (https://pe.linkedin.com/in/################### : who is mentioned to work with C#-Sql architectures and Azure servers).
- On the other hand the assumptions of services provided by Belmond LTD are other assumptions because it is a large organization.
- In the case of the mentioned systems, they are not close to reality because I do not know how it works because I never worked in it, so I emphasize that they are my inventions. So the operation and structure of the organization does not reflect reality either).
3. Organizational chart
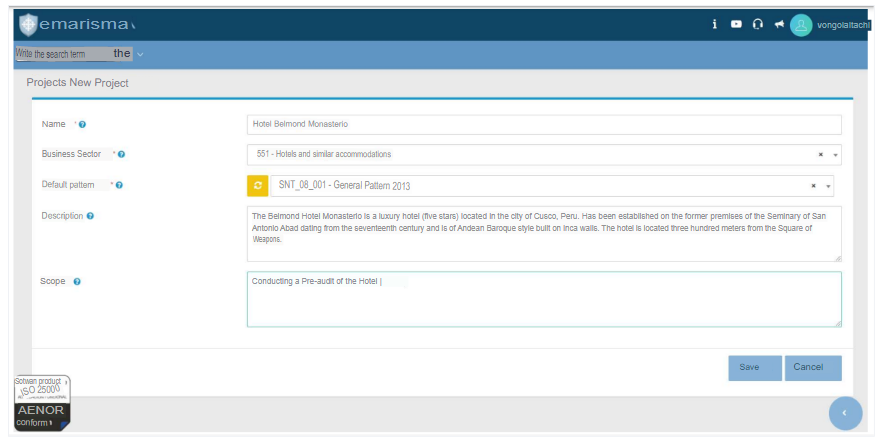
4. Description of the project
The main objective of the project is the verification and implementation of an ISMS to establish and maintain a secure environment, protecting customer information in an adequate manner and efficiently managing the use of resources and risk management. The purpose of all this is to ensure the availability, integrity, confidentiality and continuity of availability, integrity, confidentiality and continuity of the services provided by Hotel Belmond Monasterio to its clients, as well as identifying opportunities for improvement and strengths in information security and information asset management.
The scope of this project is the implementation of the ISMS for the headquarters of the Hotel Belmond Monasterio located in Cusco, Peru. In this headquarters, compliance with ISO 27001:2013 will be evaluated in the following controls:
a. A.5 - Information Security Policies.
b. A.6 - Information security organization
c. A.7 - Security linked to human resources
d. A.8 - Asset management
e. A.9 - Access control
f. A.10 - Cryptography
5. Emarisma tool logs
6. Asset categorization
| Type | Name | Value Strategic | Cost | Owner | Responsible | Description | Remarks |
|---|---|---|---|---|---|---|---|
| [S] Services | Application Cooking Classes | Low | 0.00€ | Hotel Belmond Monastery | Alberto Velasquez | An application for cooking classes where users can access with a username and password that is assigned to them, so they can see the dishes they prepare, their equivalents, nutritional table and steps to follow in their respective languages of origin. | - |
| [SW] Applications (software) | Itinerary Application | Very High | 0.00€ | Hotel Belmond Monasterio | Alberto Velasquez | Application where guests can check their itinerary and reservations. | - |
| [SW] Applications (software) | Restaurant Reservation Application | Medium | 0.00€ | Alberto Velasquez | Hotel Belmond Monasterio | The Hotel Belmond Monasterio has an application to make reservations in its restaurants. Whether someone is a guest or not of the hotel. | - |
| [L] Facilities | Network Wiring | Very Low | 0.00€ | Hotel Belmond Monastery | Alberto Velasquez | Wiring of all rooms, Reception and Business Center. | - |
| [S] Amenities | Pisco Tasting | Very Low | - | Hotel Belmond Monastery | Alberto Velasquez | An application for the tasting of pisco (liquor of Peruvian origin) where users can access with a username and password that is assigned to them, so they can see the cocktails that they prepare with the ingredients, their equivalences, nutritional table and steps to follow in their respective languages of origin. | - |
| [D] Data / Information | Customer Data | Very High | 0.00€ | Hotel Belmond Monastery | Alberto Velasquez | The registry of the clients who stayed at the hotel. | - |
| [D] Data / Information | Personal Data | Medium | 0.00€ | Hotel Belmond Monastery | Alberto Velasquez | Personal information of Hotel employees Belmond Monasterio: DNI, Names and Surnames, telephone, cell phone, salary, work load, etc. | - |
| [HW] Computer equipment (hardware) | General equipment in the facilities | Very High | - | Hotel Belmond Monastery | Alberto Velasquez | This is the equipment found in the organization, which is used to verify records and process requests. | - |
| [AUX] Auxiliary Equipment | Inventory | Low | - | Hotel Belmond Monastery | Alberto Velasquez | Peripheral equipment and auxiliary cables to keep hardware failures to a minimum. | - |
| [P] Staff | Systems Technical Staff | Medium | 0.00€ | Hotel Belmond Monastery | Alberto Velasquez | This staff is in charge of providing technical support for the facilities and troubleshooting minor systems problems. | - |
| [COM] Communication networks | Routers and Switches | High | - | Belmond Monasterio Hotel | Alberto Velasquez | All the connection equipment such as Routers and Switches at the Belmond Monasterio Hotel. | Uninterrupted connectivity in Belmond Hotels is indispensable, especially because most of their guests are businessmen or people who need to be connected all the time. |
| [L] Facilities | Meeting Room | Very High | - | Hotel Belmond Monastery | Alberto Velasquez | In this area users can connect and hold their conferences. | - |
| [S] Services | Cloud Server | Very High | - | Belmond LTD | Belmond LTD | The Belmond LTD organization owns a private PaaS type cloud server, which is assigned to each hotel in the world. This service is in charge of collecting all the information from all areas, staff and customers, for a subsequent CRM. | - |
| [HW] Hardware | Local Server for Human Resources | Medium | - | Hotel Belmond Monastery | Alberto Velasquez | Local rack server for the Human Resources software, which is in charge of workload management and attendance registration. | - |
| [SW] Applications (software) | Human Resources Management System | Medium | - | Hotel Belmond Monastery | Alberto Velasquez | This system keeps track of the work attendance of the organization’s personnel. | - |
7. Analysis of controls
As stated in the scope of the audit, the following controls are evaluated and analyzed:
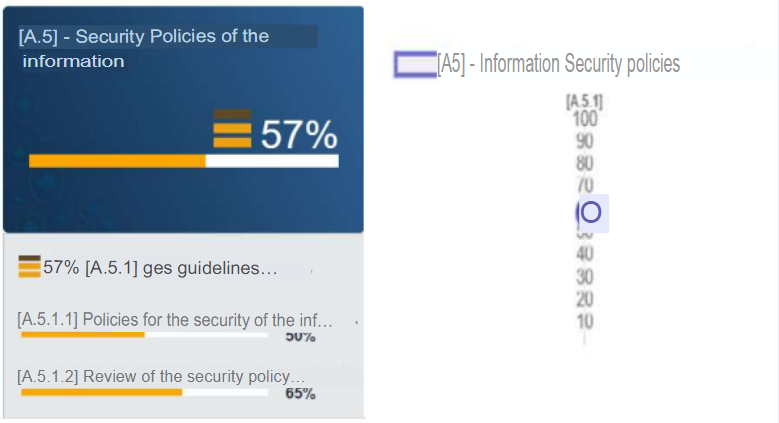
a. A.5 - Information Security Policies:
It can be observed that the percentage of compliance with the objectives exposed in the control corresponds to 57%. This percentage is due to the fact that the hotel has policies for information security which are partially supported by management but are not well communicated to new users. Likewise, the review of security policies is not well structured since it does not have an adequate control in terms of structure, schedules and criteria, since it is developed simply by the only person in charge of the technological area, the Engineering Manager, and not by a security expert, so it is evident that the review of the security policy is not performed on a regular or planned basis or with adequate input data (preventive and corrective actions, process performance, trends related to threats, among others). Thus, this is one of the critical points to be considered since it does not exceed 75% approval.
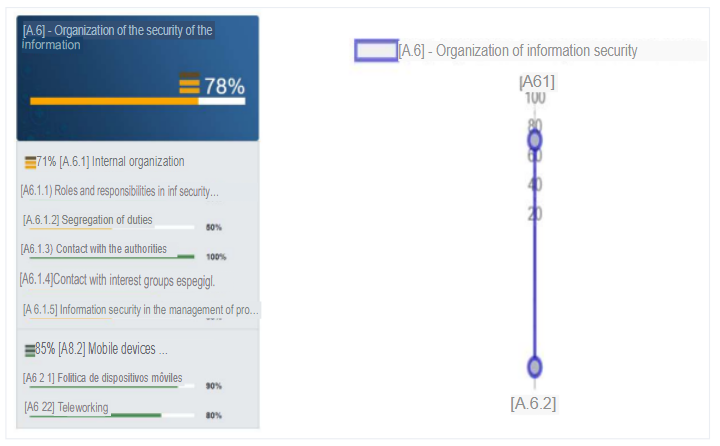
b. A.6 - Organization of information security:
It can be observed that the percentage of compliance with the objectives exposed in the control corresponds to 78%. The reason for this, although there are no established security policies regarding specific roles or security management or segregation of duties, is because there is a good management of values required for teleworking and mobile device policies provided by the organization. Although this control is higher than 75%, it is recommended to take into account that the internal organization only reaches 71%. Due to the fact that there is a very poor segregation of duties with respect to information security, because all tasks related to information security are in charge of the IT manager. Also, the assets associated to each particular system and the authorization levels that a position may have are not clearly defined, as well as the relevant security information is not constantly updated and there is no interest in knowing the trends regarding technologies, products, threats, vulnerabilities, consultancies, etc. by the IT manager.
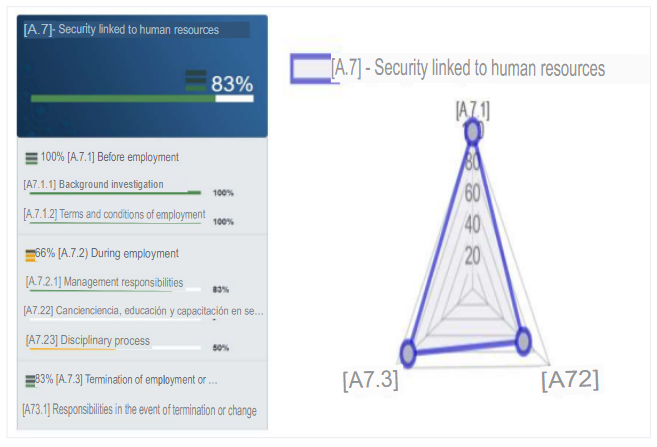
c. A.7 - Security linked to human resources
The percentage of compliance in this control is 83%. This is due to the fact that the personnel screening process is well elaborated to verify the personnel to be hired and the terms and conditions try to be as detailed as possible. However, during employment awareness is so low that it is not even considered for employee education, the disciplinary process is too lax and the only thing they can rely on is the previously established management responsibility. Yet they also have criteria at the time of contract termination.
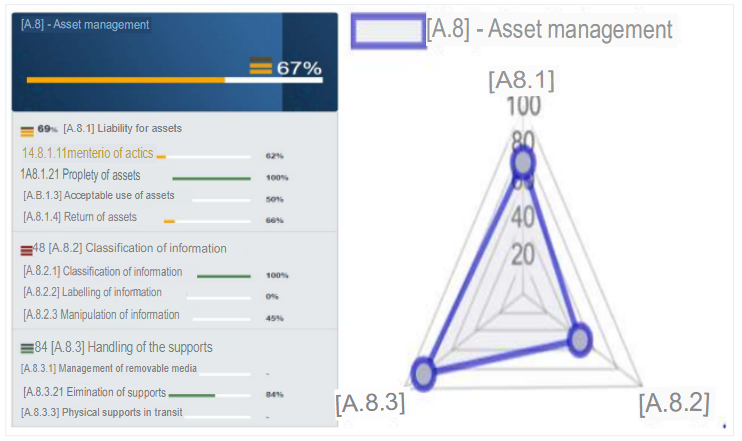
d. A.8 - Asset management
The percentage of compliance with the objectives set out in the control corresponds to 67%, being this control not acceptable. We have a somewhat structured asset inventory, a well-defined asset ownership, an acceptable use of assets at 50% and a respectable return of assets. In the case of information classification, there is no labeling of the information, so it is not considered and the handling of information is deplorable because there is no expeditious responsible control. The handling of removable media in the case of removable media does not exist, the elimination of media is consequent and physical media in transit are not used since there is a Cloud server. Therefore, it is recommended to review this control for a better management of assets and handling of information, since these points are critical in this type of organizations.
e. A.9 - Access control
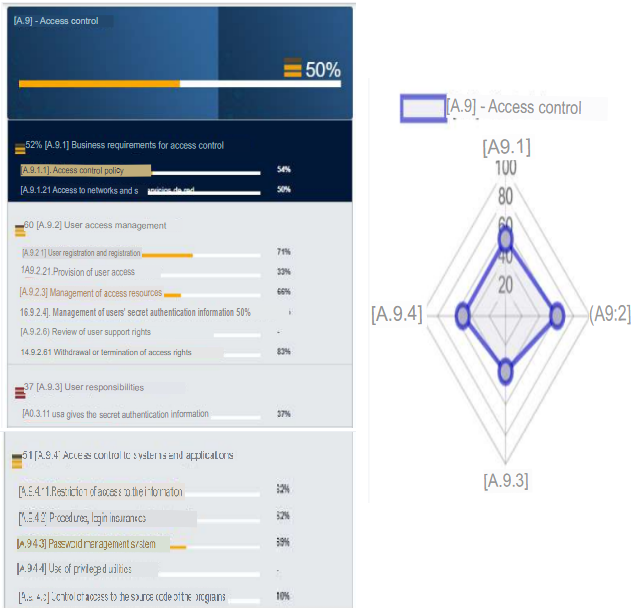
In the case of this control, compliance with this control is 50%. In general it is one of the least controlled controls (although it sounds redundant). This is due to the fact that there are no policies on the principles of necessity, there are no commercial records and the internal systems can be accessed through the internal network. In the case of user management the IDs are specific for continuous tracking and there are no general users for minor work, etc. In the responsibilities of users, although their commitments are defined, it is not really possible to follow up on their correct use of the facilities or the access they are given. And although the control of access to systems and applications tries to raise the perception of this control, there are no utilities with privileges, but only types of users who will be identified to perform their tasks. Therefore, this control must be considered for an audit and improvement process.
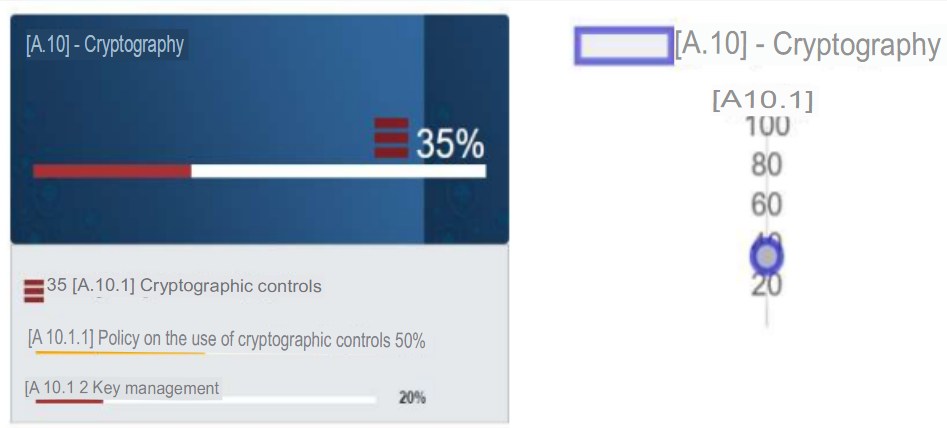
f. A.10 - Cryptography
In terms of compliance with the objectives, cryptography represents the lowest figure obtained (35%). The policy of use of cryptographic controls is based on the hashing of passwords so that they cannot be recovered by a reverse method. While in the case of key management, there are no secure methods or procedures to ensure the reliability of key management. So this should be one of the primary controls to be addressed to comply with the standard.
8. SOA Analysis
Detailed implementations were described for Hotel Belmond Monasterio in each of the controls defined in the scope of the pre-audit. The improvements in the implementations made to achieve the objectives of each of the items mentioned in ISO 27001:2013 for the first 6 controls are also described. One of the things to highlight is that most of the activities to be performed have as responsible the engineering manager, these activities should be delegated to other members of the organization or form a Technology team so that the workload is less and have the roles assigned correctly in each of the areas even though the Hotel Belmond Monasterio is only one of many branches. This is recommended to be implemented in the areas of BD, Security and infrastructure which are the main areas required, since the engineering manager is dedicated to the development of internal systems for the organization.
9. Conclusions
The Statement of Applicability (SoA) of the ISO 27001 standard for Information Security Management Systems (ISMS) is a document consisting of the complete list of assessable information security controls. Once the risk analysis and assessment have been carried out, the organization must define the treatment options for the risks and apply the security measures to be taken to mitigate them. It is at this point that the SoA document is usually developed, where the applicable security controls are recorded. When the analysis phases of the controls are completed and the SOA is defined in the pre-audit, improvement alternatives can be seen from the failures that are being recorded to the security processes that are currently in place in the organization. These opportunities for improvement can be a great help to continue with the implementation of the ISMS in the organization, since they are the basis for defining the risks, the way in which the implementation of the chosen controls will be carried out and the way in which the effectiveness of the ISMS will be measured when it is fully implemented. The pre-audit process also makes it possible to define the initial state of the company with respect to information security. This is done so that senior management has the possibility of making decisions regarding the reform, elimination or creation of new policies to protect the integrity, confidentiality and availability of the information handled by the organization, thus changing the organizational culture so that it revolves around information security and the importance of this to increase the reputation and reliability of customers in the organization.
Bibliography
Alarcon, C., Montoya, D., & Zamalloa, J. (20 de Junio de 2014). MIRAFLORES PARK HOTEL. Obtenido de https://prezi.com/zslfatrgdspo/miraflores-park-hotel/
beServices . (s.f.). Tipos de Cloud Computing. Obtenido de https://www.beservices.es/cloudcomputing-tipos-n-5324-es
CALLEJAS, N. T., & RODRIGUÉZ, A. F. (2018). AUDITORIA INTERNA A LOS ACTIVOS FÍSICOS DEL ÁREA DE TI EN LA UNIVERSIDAD COOPERATIVA DE COLOMBIA SEDE IBAGUÉ, APLICANDO EL ESTÁNDAR ISO/IEC 27002:2013. Obtenido de https://repository.ucc.edu.co/bitstream/20.500.12494/5037/2/Auditoria%20interna%20a%20los%20activos%20f%C3%ADsicos%20del%20%C3%A1rea%20TI%20en%20la%20Universidad.pdf
Fernandez, C. C. (Enero de 2020). El Nuevo Reglamento General de la Proteccion de Datos y su
Impacto en las Organizaciones TI. Obtenido de https://oa.upm.es/58096/1/TFG_CAROLINA_CARMONA_FERNANDEZ.pdf
LVMH. (s.f.). Organigrama Belmond. Obtenido de https://www.theofficialboard.es/organigrama/belmond#
Muñoz, R. I., Blanco, A. G., Ponce, K. E., & Maza, B. F. (Noviembre de 2020). PLAN
ESTRATÉGICO DEL HOTEL S BY SONIC PERIODO 2020-2024, HOTEL DE 4 ESTRELLAS UBICADO EN EL DISTRITO DE MIRAFLORES. Obtenido de https://repositorio.up.edu.pe/bitstream/handle/11354/2976/ArciniegaRene_Tesis_maes tria_2020.pdf?sequence=1 navarro, c. q. (s.f.). HOTEL BELMOND MONASTERIO. Obtenido de https://prezi.com/3nckjg0lcdva/hotel-belmond-monasterio/ Santos, A. (2022). Docente del Curso Gestión de la Seguridad . Presentación, Clases presencial-virtual UNIR.