ISO27001 - ITAF - Planning an IT audit Sample by Fernando

Content
- 1 Background
- 2 Purpose of the audit
- 3 Objectives of the audit
- 4 Scope of the technical security audit
- 5 Methodologies
- 6 Organization and resources required
- 7 Communication procedures with project managers
- 8 Planning
- 9 Budgeting
- 10 Project risk assessment
- 11 Annex I: Authorization Agreement
- 12 Annex II: Confidentiality Agreement (optional)
1. Background
The company Librería On-Line S.A., which sells books through its web portal, has been the victim of cybercriminals who managed to steal through its web portal has been the victim of cybercriminals who managed to steal the access credentials of its customers. the access credentials of its clients. As a result, Librería On-Line S.A. suffered a loss of reputation loss of reputation, trust and image, loss of market share, loss of reputation, trust and image, loss of market share, distrust in its shareholders, loss of loyal customers, decrease in sales, and uncertainty among sales and uncertainty among current customers. In order to change the aforementioned problems and reinforce the level of security of their Librería On-Line S.A. has decided to hire a security audit as the main to contract a security audit with the company InfoSecurity.
2. Purpose of the audit
The purpose of this technical security audit is to verify the level of security of Librería Online S.A.’s information systems and to make recommendations and safeguards for the identified findings.
3. Audit Objectives
To verify whether the information systems deployed in the company reasonably ensure the integrity, confidentiality and availability of the information. Along these lines, the following objectives are to be achieved:
- Verify the level of perimeter security.
- Evaluate the communications devices, router and switch.
- Analyze the security of the wifi zones.
- Review the e-mail messaging system.
- Validate the security of the main web site.
- Check compliance with the European Data Protection Regulation (GDPR).
4. Scope of the Technical Security Audit
The scope of the audit includes the following activities:
- External VPN access.
- DMZ zone: FW and IDS.
- Publication of the company’s web site.
- External and internal mail.
- Public DNS and FTP services.
- Network infrastructure: router and switch.
- Internal Intranet and corporate applications.
- Wifi zone.
- VLAN segmentation of the internal network: servers and users.
- AAA system (authentication, authorization and traceability).
- Antimalware system.
4.1. Detail of the tasks to be performed.
- Planning: Understanding of the activity Develop audit presentation document Elaborate audit program Delivery of information and documentation request document.
- Execution Initial meeting Interviews with activity managers Technical evaluation Field visit Information analysis Evaluation of controls Identification of findings Meeting to explain findings
- Closure Preparation of observations report Preparation of audit report Meeting to confront and elaborate closure minutes Finalization of audit report Closing meeting
4.2. Types of tests to be performed.
The tests to be performed are the following:
- Verification of accesses.
- Review of the network perimeter
- Validation of web sites
- Audit of messaging services
- Validation of public services
- Vulnerability scanning of internal and external applications
- Verification of wireless networks
- Penetration testing of internal network
- Intrusion testing of information systems
- Validation of security devices
- Verification of compliance with the European Data Protection Regulation (GDPR).
4.3. Identify applicable constraints.
In order to foresee possible events that may impact the development of this audit, a situational assessment of the organization’s context has been carried out, taking as an added value the company’s experience in similar audit services in other organizations.
The following limitations have been identified:
-
Obtaining technical information from the company in a timely manner. This information will serve as input for the planning phase, for example: network topology diagrams, architecture diagrams, inventory of IT assets, etc. Failure to receive this information in a timely manner is a constraint that can affect the initial assessment and impact execution times.
-
Dependence on external suppliers. Within the scope of the technological services to be evaluated, there are some that are outsourced to third parties, which may generate impacts for the execution of the programmed activities, due to the response times of the suppliers to provide the necessary facilities for the audit.
5. Methodologies
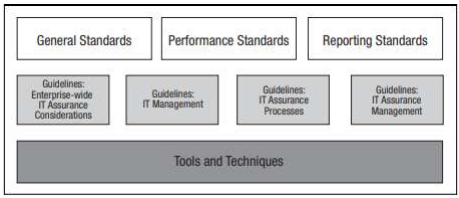
In order to perform the audit process on Librería On-Line S.A., ISACA’s “IT Audit Framework (ITAF)”, which is a framework of professional practices for IT auditing, has been selected as the audit methodology.
Image 1. ITAF - Practical IT Assurance Reference Framework.
ITAF is a comprehensive, best-practice reference model that:
-
Establishes standards that address IT systems auditing, professional roles and responsibilities; knowledge and skills, diligence, conduct and reporting requirements.
-
Defines terms and concepts specific to information systems assurance.
-
Provides guidance, tools and techniques in the planning, design, conduct and reporting of information systems auditing and assurance.
Information Systems Audit and Assurance
The ITAF General, Performance and Reporting Standards must be followed in all circumstances.In addition, the standards contain key aspects designed to assist IT systems auditing and professional assurance. The ITAF framework is composed of the elements shown in Figure 2. These include three categories of standards, General, Performance and Reporting. General Standards: These are the guiding principles under which the IT assurance profession operates. They apply to all IT audit behavioral assignments such as professional ethics, independence, objectivity, necessary care and competence in knowledge and skills.
Execution Standards: Deals with planning and supervision, delimitation, risk and materialization, resource mobilization, assignment supervision and management, audit and evidence assurance, and the exercise of professional judgment and due care.
Reporting Delivery Standards: directs the types of reports, forms of communication, and information communicated. Guidelines:
Reporting Standards: Addresses the types of reports, forms of communication and the information communicated. Guidelines:Provides the IT audit and assurance professional with information and guidance on the area of audit or assurance.In line with the three categories of standards mentioned above, the guidelines focus on various audit approaches, methodologies, tools and techniques, and related material to assist in the planning, execution, evaluation, review and reporting of IT processes, as well as related audit assurance controls and initiatives.
Tools and techniques: provides specific information on various methodologies, tools and templates, and provides guidance on their application and use to operationalize the information provided in the guide.
Image 2. ITAF taxonomy, as ITAF is hierarchically organized.
The ITAF audit methodology is divided into numerals for better understanding. The following is a table with the different components of the standard and their differentiation components of the standard and their differentiation depending on their objective.
| Section 1000: | Introduction to the IT Assurance Framework |
|---|---|
| - | 1001 Auditor Profile 1002 Organizational Independence 1003 Professional Independence 1004 Reasonable Expectation 1005 Due Professional Care 1006 Competence 1007 Assertions 1008 Criteria.Execution 1201 Engagement Planning 1202 Planning Risk Assessment 1203 Performance and Supervision 1204 Materiality 1205 Evidence 1206 Use of the Work of Other Experts 1207 Irregularity and Wrongful Acts 1208 Criteria. Reporting 1401 Reporting 1402 Follow-up activities |
| Section 2000: | IT Assurance Standards: Defining Common Benchmarks. |
|---|---|
| - | General 2001 Auditor Profile 2002 Organizational Independence 2003 Professional Independence 2004 Reasonable Expectation 2005 Due Professional Care 2006 Competence 2007 Assertions 2008 Performance Criteria 2201 Planning Engagement 2202 Planning Risk Assessment 2203 Performance and Oversight 2204 Materiality 2205 Evidence 2206 Use of Other Experts’ Work 2207 Irregularity and Wrongful Acts 2208 Sampling Report 2401 Reports 2402 Follow-up Activities |
| Section 3000: | Implementation Guidance: Standards in practice. |
|---|---|
| - | 3100 IT Assurance Guidelines: Overview and Usage. 3200 Business issues 3210 Involvement of enterprise-wide policies, practices and standards in the IT function 3230 Involvement of enterprise-wide assurance initiatives in the IT function 3250 Involvement of enterprise-wide assurance initiatives in IT assurance plans and activities 3270 Additional enterprise-wide issues and their impact on the IT function 3400 IT management processes 3410 IT governance (Mission, Objectives, Strategy, Corporate Alignment, Reporting) 3412 Determining the impact of business initiatives on IT assurance activities 3415 Using the work of other experts in performing IT assurance activities 3420 IT Project Management 3425 IT Information Strategy 3427 IT Information Management 3430 IT Strategy and Plans (Budgets, Funding, Metrics) 3450 IT Processes (Operations, Human Resources, Development, etc. ) 3470 IT risk management 3490 IT compliance support 3600 IT audit and assurance 3605 Relying on the Work of Specialists and Others 3607 Integration of IT audit and assurance work with other audit activities 3610 Use of COBIT in the IT assurance process 3630 Audit of IT general controls (ITGC) 3650 Audit application controls 3653 Audit of traditional application controls 3655 Enterprise resource planning (ERP) audit systems 3657 Audit of alternative software development strategies 3660 Specific audit requirements 3661 Government-specified audit criteria 3662 Industry-specified audit criteria 3670 Computer-assisted audit techniques (CAAT) audit 3680 IT audit and regulatory reporting 3690 Selection of assurance elements of interest 3800 IT assurance and audit management 3810 IT assurance or audit function 3820 Planning and Scope of IT assurance and audit objectives 3830 Planning and scope of IT assurance and audit work 3831 IT assurance and audit work 3832 IT assurance and audit planning and scope of work 3833 IT assurance and audit objectives 3810 IT audit or assurance function 3820 Planning and scoping of IT audit and assurance objectives 3830 Planning and scoping of IT audit and assurance work 3835 Planning and scoping risk assessments 3840 Managing the execution of the IT audit and assurance process 3850 Integration of the audit and assurance process 3860 Collection of evidence 3870 Documentation of IT audit and assurance work 3871 IT audit and assurance work 3875 Documentation and confirmation of IT audit and assurance findings 3880 Evaluation of results and development of recommendations 3890 Actual IT audit and assurance reports 3892 Reports of IT audit and assurance recommendations 3894 Reports on IT advisory and consulting reviews |
| Section 4000: | IT Assurance Tools and Techniques |
|---|---|
| - | X |
Table 1. Description of the numerals of the ITAF methodology.
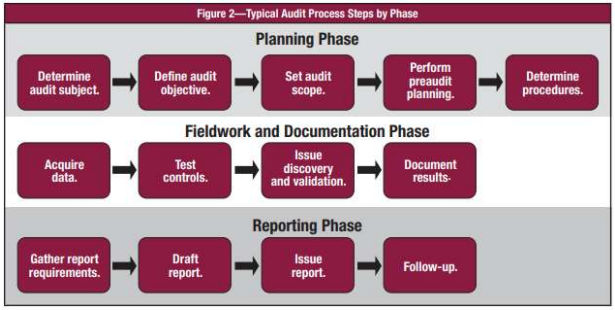
Typical audit procedure according to the ITAF framework.
Each phase in the audit process is subsequently divided into key steps for planning, defining, executing and reporting on the outcome of the line of engagement with the audit standards are shown in Figure 3 below. The organization and naming conventions of each step are described by the ITAF guidance and can be adjusted to meet the requirements of the business as they meet the applicability of the standards and fulfill the overall objective of the audit engagement.
Figure 3, Typical ITAF audit process, steps by phase.
Planning Phase
- Determine the audit subject.
- Define the audit objectives.
- Define the scope of the audit.
- Make a pre-audit plan.
- Determine procedures. Field work and documentation phase. Acquisition of data.
- Control points.
- Fault discovery and validation.
- Documenting results. Report delivery phase.
- Gather required reports.
- Prepare draft report.
- Sign draft report.
- Continue (perform the audit process one more time).
6. Organization and resources required
Regarding the specialists assigned to this project, we have the following specialists.
| Role | Name | Profession | Certificate |
|---|---|---|---|
| Audit Manager | Gerardo Andrade | Master in IT Security | Project Manager Professional, ITIL |
| Consultant Senior 1 | Camilo Jimenez | Master in IT Security | Project Manager Professional, COBIT 5 |
| Consultant Senior 2 | Carlos James | Master in Computer Security | ISO/IEC 27001, CEH, CISSP, CISM |
Table 2, Human resources for the audit.
Our professionals will be supported by the use of the following technological resources.
| Reference | Manufacturer | SO | HW | Purpouse |
|---|---|---|---|---|
| ThinkPad X Nano Gen 1 Black Model: 20UQS0KV | Lenovo Cert MIL-STD 810G | Windows 10 Pro 64 | -SSD 1TB -RAM 16 GB -Intel® Core™ i7-1180G -Wi-Fi 6, 802.11ax 2x2 Wi-Fi -Bluetooth 5.1, M.2 Card | In-house Testing |
| ThinkPad X Nano Gen 1 - Black Model: 20UQS0KV | Lenovo | Windows 10 Pro 64 | -SSD 1TB -RAM 16 GB -Intel® Core™ i7-1180G -Wi-Fi 6, 802.11ax 2x2 Wi-Fi + -Bluetooth 5.1, M.2 Card | External Testing |
| Dell Precision 7760 | Dell | Red Hat Enterprise | -SSD 1TB -RAM 16 GB | Red Team |
| - | - | Linux Server | Intel® Xeon® W-11955M, vPro® (24 MB cache, 8 cores, 16 threads, 2.60 GHz to 5. GHz Turbo, 45 W) | - |
| Dell Precision 7760 | Dell | Red Hat Enterprise Linux Server | - SSD M.2 2280 de 2 TB, 4.ª generación, PCIe x4 NVMe - RAM 128 GB, 4 x 32 GB, DDR4, 3200 MHz, ECC - Intel® Xeon® W-11955M, vPro® (24 MB cache, 8 cores, 16 threads, 2.60 GHz to 5. GHz Turbo, 45 W) - Intel Wi-Fi 6E AX210 Wireless Card with Bluetooth 5. | Blue Team |
Table 3. IT resources for the audit.
Some of the tools to be used in the different phases of this audit are described below.
| Phases | Tools | Description |
|---|---|---|
| Planning phase | Microsoft Office 365 Microsoft Project | For this phase we will mainly use Microsoft office tools together with its Microsoft Project tool, specialized in the development of plans, project tracking and report generation. |
| Field work and documentation phase. | Acrylic Maltego Acunetix MaxMind Advanced Scanner Metasploit Aircrack Microsoft Office 365 Airmon-ng Microsoft Project Airodump nbtstat Amap Nessus Pro Archive.org Netcat Armitage netScan Beef NetSparker Bettercap NetworkMiner Cain & Abel Nmap Censys OpenVas CLARA Ophcrack Core Impact OSINT Framework CrypCat OWASP ZAP dnsgoodies PwDump DNSSpoof RIPS EmailSpider SamSpade Ettercap SET ExploitKit Shodan Firewalking Sn1per Fortify SnifferPro GFI Languard SQLMap Google Dorks SSLStrip Google Maps Stalker HTTPPrint TCPDump Hunter TheHarvester Hydra Tinfoleak ICMP Traceroute Jhonthe ripper W3af Kismet Whois Online Krack Wifi Fern Look@lan Wireshark LUCY Yersinia Macof ZenMap | For this phase we will mainly use Microsoft office tools together with its Microsoft Project tool, specialized in the development of plans, monitoring/documentation of projects and generation of reports. Additionally, this phase also makes use of those tools of vital utility in the analysis, exploitation of vulnerabilities, Footprinting, Open Source Intelligence, Network and Port Scanning, etc. |
| Report delivery phase. | Microsoft Office 365 Microsoft Project | For this phase will be used mainly Microsoft office tools along with its Microsoft Project tool, specialized in the development of plans, project tracking and reporting. |
Table 4. Audit tools.
7. Communication procedures with project managers
Those responsible for this audit project will communicate mainly by e-mail to have time stamps and delivery support, and in special cases, verbally in pre-scheduled meetings only, given the above, telephone communication is limited only to cases of extreme urgency and will be carried between the directors (Auditor and Auditee) of the project.
The contact information is listed in the following table:
| Role | Name | Phone | |
|---|---|---|---|
| Audit Manager | Gerardo Andrade | gerenteauditoria@auditor.com | +57 3205554433 |
| Consultant Senior 1 | Camilo Jiménez | Consultorjunio1@auditor.com | NA |
| Consultant Consultant 2 | Carlos James | Consultorjunio2@auditor.com | NA |
| CEO | Juan Carlos López | juan.carlos@libreriaonline.com | +34 669 33 22 11 |
| CTO | José Luis Salas | jose.luis@libreriaonline.com | +34 669 33 22 10 |
Table 5. Audit contact information
The delivery of reports, evidences, supports and annexes will be done within the timeframe stipulated in the planning.
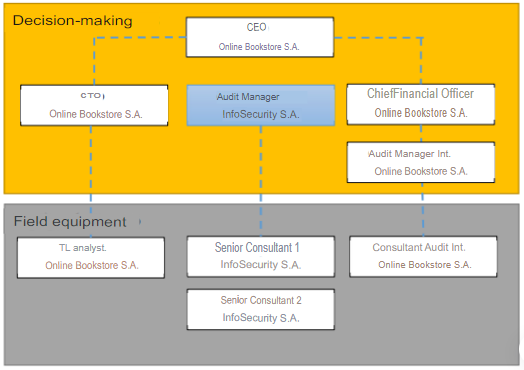
There is an escalation matrix in which it is clarified that the person who will act as liaison between Librería Online S.A. and InfoSecurity will be InfoSecurity’s audit manager, and all official communications will be made through him, although communications at a horizontal level are not ruled out for purposes of information gathering and management of processes inherent to the audit, without affecting the established objectives and purposes.
Image 4. Communication escalation matrix.
8. Planning
8.1. Content of the plan
The following key activities have been defined for the development of the audit plan. Understanding: in order to have a general understanding of the company’s context it is necessary to identify, among others:
- The procedures, responsibilities and organizational structure of the roles involved.
- General technology controls in the applications and technological platforms where they operate.
- Main modules that make up the applications and the processes they support.
- User management, configuration management and incident management procedures.
- Security scheme for applications and their technological platforms.
- Identification of key automatic controls of the applications that support business processes.
Definition of the assessment plan
According to the understanding obtained in the previous phase and the Company’s expectations, the review plans for the technological infrastructure will be designed. The tests defined for the evaluation of general technology controls for technology infrastructure and application development and maintenance will be performed based on the defined methodology and good security practices. The selection of mitigation controls will be made once the key controls that support the business processes have been identified in the previous phase.
Execution of the assessment plan
Based on the previously defined assessment plan, detailed work programs will be established where the following will be defined:
- Execute the detailed tests
- Documenting the results.
Presentation of results
Prepare and inform the roles involved and the areas deemed necessary, about the findings that mean risks for the company, as well as the recommendations that allow defining and executing improvement plans necessary to mitigate and manage the identified risks. The following activities will be carried out:
- Validate the findings and recommendations with the responsible areas.
- Request the areas responsible for defining and implementing the action plans and the implementation schedule, in order to facilitate follow-up.
- Submit a report with the findings and opportunities for improvement.
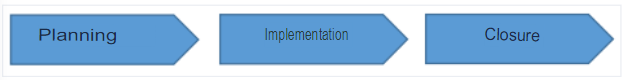
8.2. Phases of the audit performance.
The phases for the performance of the audit are the following: Planning, execution, closing
Image 5. Phases of an audit.
8.3. Task execution deadlines (diagram).
Planning
| Activity | Start | End | Assigned resources |
|---|---|---|---|
| Service understanding | 13/06/22 | 14/06/22 | Infosecurity Audit Manager, Senior Infosecurity Consultant |
| Prepare proposal of contractual agreements and audit service | 15/06/22 | 20/06/22 | Senior Infosecurity Consultant, Infosecurity Audit Manager |
| Develop audit program | 21/06/22 | 22/06/22 | Audit Manager Infosecurity, Senior Consultant Infosecurity |
| Send service proposal, contractual agreements and information request to client | 23/06/22 | 23/06/23/ | Infosecurity Audit Manager |
Table 6. Audit planning phase.
Execution
| Activity | Detail | Start | End | Infosecurity Resources | Participants / involved |
|---|---|---|---|---|---|
| Delivery of information requested from the client | Documentation to be used as input for the service | 24/06/2022 | 30/06/22 | Audit Manager | Manager of On Line Librería |
| Evaluation documentation | Review of information sent by the client | 01/07/2022 | 08/07/22 | Senior Consultant 1, Senior Consultant 2 | - |
| Kick-off meeting | Presentation of objectives and scope | 11/07/22 | 11/07/22 | Audit Manager, Senior Auditor, Junior Auditor | Managers, stakeholders of Librería On Line |
| Meetings with activity managers | Review of access process | 12/07/22 | 13/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with activity managers | Review of network and infrastructure management | 07/14/22 | 07/15/22 | Senior Consultant 1, Senior Consultant 2 | Librería On Line Stakeholders |
| Meetings with activity managers | Review of DMZ implementation and inbound and outbound traffic | 18/07/22 | 19/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with activity managers | Review of penetration tests and vulnerabilities | 20/07/22 | 21/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with activity managers | Review of security services and devices | 22/07/22 | 26/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with activity managers | Review of utilities and messaging services | 27/07/22 | 28/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with business managers | Review of internal and external applications | 27/07/22 | 28/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Meetings with activity managers | Review of GDPR compliance | 27/07/22 | 29/07/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders of Librería On Line |
| Information analysis and sample selection | Analysis of collected information | 01/08/22 | 05/08/22 | Senior Consultant 1, Senior Consultant 2 | - |
| Technical evaluation | Execution of technical reviews | 08/08/22 | 31/08/22 | Senior Consultant 1, Senior Consultant 2 | - |
| Documentation of results | Documentation of findings | 01/09/22 | 09/09/22 | Senior Consultant 1, Senior Consultant 2 | |
| Verification of results | Clarification of doubts | 12/09/22 | 12/09/22 | Senior Consultant 1, Senior Consultant 2 | Stakeholders involved in findings |
| Preparation of report of observations | Documentation of findings | 13/09/22 | 19/09/22 | Senior Consultant 1, Senior Consultant 2 | |
| Preparation of recommendations | Preparation of recommendations | 20/09/22 | 21/09/22 | Senior Consultant 1, Senior Consultant 2 | |
| Completion of the audit report | Completion of audit report | 22/09/22 | 22/09/22 | Senior Consultant 1, Senior Consultant 2 | - |
| Closing meeting | Final results presentation meeting | 23/09/22 | 23/09/22 | Senior Consultant 1, Senior Consultant 2 | Managers, stakeholders of Librería On Line |
Table 7. Audit execution phase.
9. Budget
Audit fees are impacted by the following factors: the depth of the review expected by the stakeholders and management, as well as the business risks, volume and complexity of the operations. Based on our experience in auditing other companies in the sector, taking into account that we have been auditing for years other entities in the same industry and based on our knowledge of the operations, as well as what we received from you in previous communications, we consider that we can provide the services described in the scope for the following investment: USD $50,000 (excluding taxes).
| Item | Category | Amount |
|---|---|---|
| 1 | Consulting Manager | $ 20,000 |
| 2 | Senior Consultant 1 | $ 12,000 |
| 3 | Senior Consultant 2 | $ 12,000 |
| 4 | Operating system licenses and auditing solutions | $ 5,000 |
| 5 | Computer equipment | $ 800 |
| 6 | Materials | $ 100 |
| 7 | Transportation | $ 100 |
| Total | - | $ 50,000 |
Table 8. Budget.
10. Project risk assessment
In order to successfully meet the objectives of the technical audit service, the following risks have been identified which, if they materialize, may have a negative impact on one or more of the service objectives.
| No. | Description | Strategy | Action Plan | Responsible Level | |
|---|---|---|---|---|---|
| 1 | Delay in the schedule due to late delivery of requested documentation | Mitigate | Prioritize the service as critical and follow up with those responsible for the delivery of documentation | Librería On Line | High |
| 2 | Delay in the schedule due to the subcontracted supplier’s delay in providing the facilities for the execution of the technical tests | Mitigate | Engage the outsourcing vendor to provide testing facilities | Librería On Line | High |
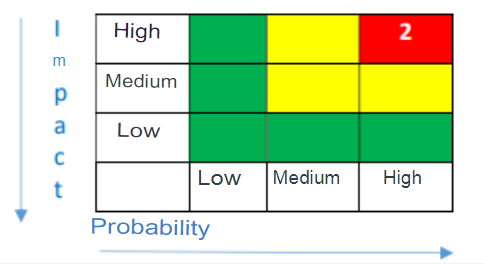
Table 9. Risk assessment.
Table 10. Risk level for the audit project.
11. Annex I: Authorization Agreement
Librería On-Line S.A with address at Plaza Ajuntament, 3 - B, Valencia, 46002, valencia and CIF B46057881, registered in the Mercantile Registry of Valencia, hereinafter referred to as THE COMPANY, authorizes: InfoSecurity, hereinafter referred to as THE PROVIDER to perform a security audit of its information and communications systems, including but not limited to different tests to check the level of cybersecurity that the technological infrastructure possesses. This review will be carried out from 06/13/2022 until 09/23/2022. Except as expressly stated by THE COMPANY, THE PROVIDER will not attempt to cause the servers to be out of service, nor will it carry out denial of service attacks. However, given the nature of the review, such circumstances may arise unintentionally, even though we have performed professional due diligence.
THEREFORE, THE PROVIDER DISCLAIMS ANY LIABILITY WHATSOEVER FOR ALL DAMAGES THAT MAY RESULT DIRECTLY OR INDIRECTLY FROM THE PERFORMANCE OF THE “PENETRATION TEST”, INCLUDING, BUT NOT LIMITED TO, DOWNTIME, LOSS OF DATA, ETC.
THE COMPANY declares that it has read and agrees with what is expressed in this document. On the other hand, THE SUPPLIER declares that it will perform this work with due professional diligence and in accordance with what is defined in the scope, in such a way that, as far as possible, it will not cause the COMPANY’s computer systems to be down or rendered unusable. The undersigned declares that he/she is duly authorized by his/her representative to authorize THE COMPANY to carry out the service in the terms indicated.
12. Annex II: Confidentiality Agreement (optional)
In accordance with the provisions of the relevant regulations, the parties agree as follows: a. The SUPPLIER undertakes to maintain and keep in strict confidentiality the characteristics, terms and conditions of this contract.
b. THE SUPPLIER undertakes to maintain and keep in strict reserve and absolute confidentiality all documents and information of THE COMPANY to which it has access in execution of this contract. It is understood that the obligation assumed by THE SUPPLIER refers not only to the documents and information indicated as “confidential”, but to all the documents and information that by reason of the present contract or related to the execution of the same, may be known by any means by THE COMPANY. Consequently, THE COMPANY shall refrain from disclosing such documents and information, either directly or indirectly. THE COMPANY agrees that all information provided under this contract is confidential and proprietary to LIBRERÍA ON-LINE S.A., and THE SUPPLIER may not use such information for any purpose other than that permitted or required to fulfill its obligations.
c. In both cases, THE SUPPLIER must prove, upon request of THE COMPANY, the removal of the information.
d. THE SUPPLIER may only disclose the documents and information referred to in the preceding paragraphs to the personnel strictly necessary for the performance of the activities under this contract.
e. THE SUPPLIER undertakes to take reasonable measures and precautions so that in general any person who has a relationship with THE SUPPLIER does not disclose to any third party the documents and information referred to in the preceding paragraphs. any third party the documents and information to which it has access, and shall be responsible for the responsible for the disclosure that may occur and assuming the payment of compensation for damages determined by the competent authority.
f. THE SUPPLIER undertakes not to disclose or disseminate, by any means whatsoever, any labor, tax, financial or any other information belonging or concerning THE COMPANY, as well as about know-how, legal processes and the like that may be known to THE COMPANY and, in general, about any information related to the Services here contracted or any relevant and important information that may be delivered by THE COMPANY by verbal, written and/or electronic means in the course of the rendering of the Services here contracted, including that which it may know or observe as a consequence of the execution of this Contract (the “Confidential Information”). Likewise, THE SUPPLIER undertakes not to disclose or disseminate by any means the reports generated as deliverables within the framework of the provision of the service and in general not to disclose or disseminate any other information or data obtained from THE COMPANY.
g. THE SUPPLIER shall keep the Confidential Information in absolute reserve and shall not make use of it for purposes other than those of this Agreement, and may not disclose it to third parties under any circumstances. Upon termination or termination of this Agreement, the SUPPLIER shall return to the COMPANY all the documents that the latter may have delivered to it.
h. Likewise, it is agreed that THE SUPPLIER is obliged to deliver to THE COMPANY, when requested by it, any type of documentation, accounting, technical or operative information in its possession in relation to the rendering of the contracted services.
i. In the event that THE SUPPLIER is required by any administrative or judicial authority to disclose the information and/or documentation referred to in this clause, THE SUPPLIER shall notify THE COMPANY within 24 hours of the event becoming known so that it may adopt the measures it considers necessary to protect the confidentiality of the information. The confidentiality obligation established in this additional clause operates from the subscription of this contract and shall remain in force indefinitely.
j. THE SUPPLIER agrees to return all the material provided by THE COMPANY at the time of resolution or termination of the present contract without being required to do so by THE COMPANY. SUPPLIER also agrees to erase from the memory of its equipment all information belonging to COMPANY, as well as to delete documents, video tapes, voice recording tapes, diskettes, compact discs or other magnetic media containing information owned by COMPANY. THE SUPPLIER declares that THE COMPANY may carry out the respective verifications when it deems it convenient.
k. THE SUPPLIER agrees to respect and apply in the service provided, the policies, procedures and security controls established by THE COMPANY, which he/she declares to know and accept.
l. THE SUPPLIER undertakes that in the event that the service provided to THE COMPANY consists of and/or requires the installation of new hardware and/or software, it must necessarily comply with the security management process for hardware and software configurations used by THE FINANCIERA.
m. THE COMPANY has the right to request from THE SUPPLIER the documentation certifying compliance with the obligations described in this clause.
n. THE SUPPLIER undertakes to provide all the necessary facilities for THE COMPANY to audit and/or monitor the information security aspects of the services and information assets subject of the contract.
ñ.In case THE SUPPLIER requires any type of access to the resources or tools of THE COMPANY, these must be previously authorized by THE COMPANY.
o.THE SUPPLIER and all personnel of THE SUPPLIER designated by THE SUPPLIER for the provision of the service is prohibited from accessing information related to the operations of THE COMPANY’s clients, subject to civil, criminal, administrative and any other legal consequences related to the violation of banking secrecy, The SUPPLIER assumes joint and several liability for the non-compliance of such personnel or third parties of the provisions of this clause, and unlimited liability for all damages caused to the COMPANY or its customers, as well as the payment of any penalties that may be imposed on the COMPANY in this regard.
p. THE SUPPLIER assumes responsibility for the loss, modification, destruction, falsification, theft, misuse and/or unauthorized disclosure of the COMPANY’s information assets, to the extent that this is attributable to THE SUPPLIER or its personnel. THE SUPPLIER must ensure that access to each office and/or work area that manages materials and information subject to the contract must be restricted to authorized persons only. All work environments must have the physical and environmental security necessary to adequately protect the COMPANY’s information assets.
q. Both parties understand as information assets the documents containing information of THE COMPANY, among these, client’s information bases, securities, contracts, client’s file, which is not exclusive.In case of security incidents, THE SUPPLIER:
r. Provide THE COMPANY with the necessary resources (human and material means) so that it can carry out the analysis of the incident and its correction.
s. It will allow THE COMPANY to analyze and investigate the logs of the systems, traces of the IDS elements, IPS, firewall and any network and security element implemented, whether they are located in THE SUPPLIER’s own facilities or in THE COMPANY’s facilities.
t. Ensure that the logs and traces referred to in the preceding paragraph are not deleted for at least seven (7) working days from the date of notification of the incidents.
u. Safeguard and isolate any electronic or any other type of evidence that may be useful, in order to be able to make, if necessary, a forensic copy of such evidence.
v. THE SUPPLIER declares to be fully aware of all the normative scopes contemplated in the internal regulations of the COMPANY; as well as the measures and/or sanctions for the non-compliance of the same.
w. Failure to comply with this clause will immediately result in the termination of this Contract, and the payment of a penalty, plus the corresponding compensation for damages and losses.