Appointment - Hack The Box

Appointment is a machine of Starting Point of HTB. The machine has a PHP web app and the objetive is find a command injection vulnerability in the site to claim the flag.
1st HTB Task Solving
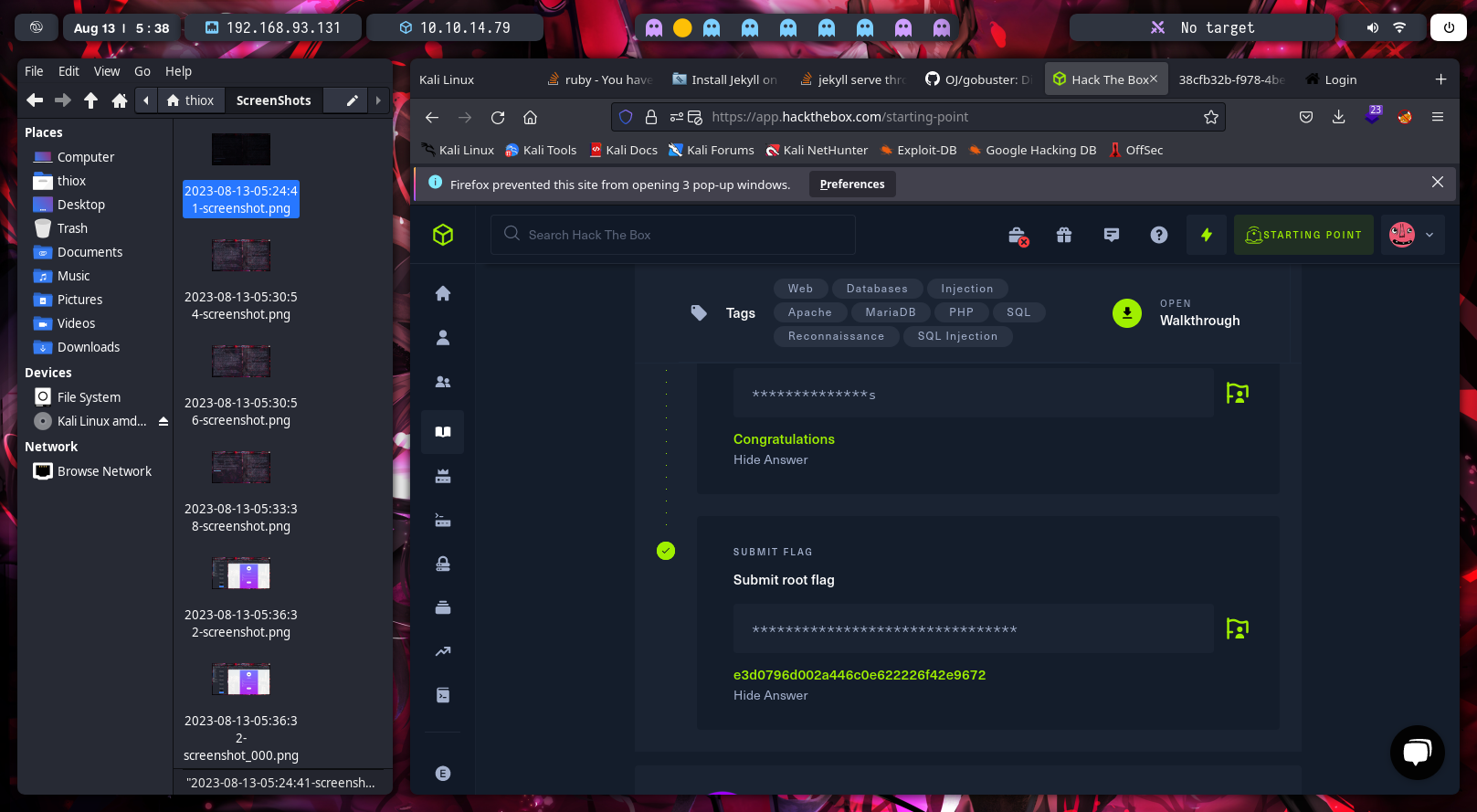
The initials goals of the HTB in this Starting Point are connect with the machine. We only need download vpn and connect with OVPN. Later, for the first task is about the name of SQL, that is an acronym of “Structured Query Language”. The second task is the name of one the most common vulnerability, as it begin with three letters, the response is “SQL injection”.
2nd HTB Task Solving
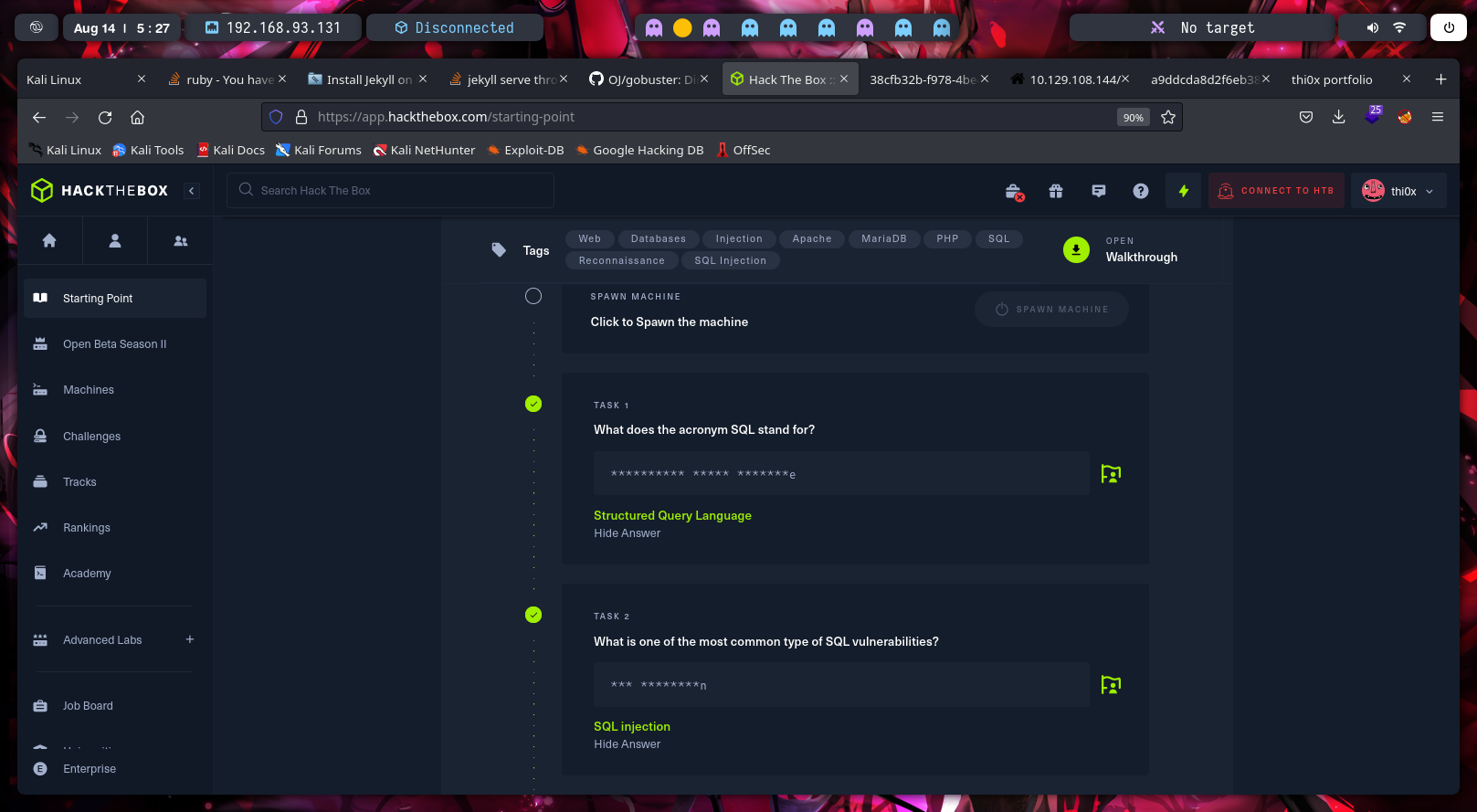
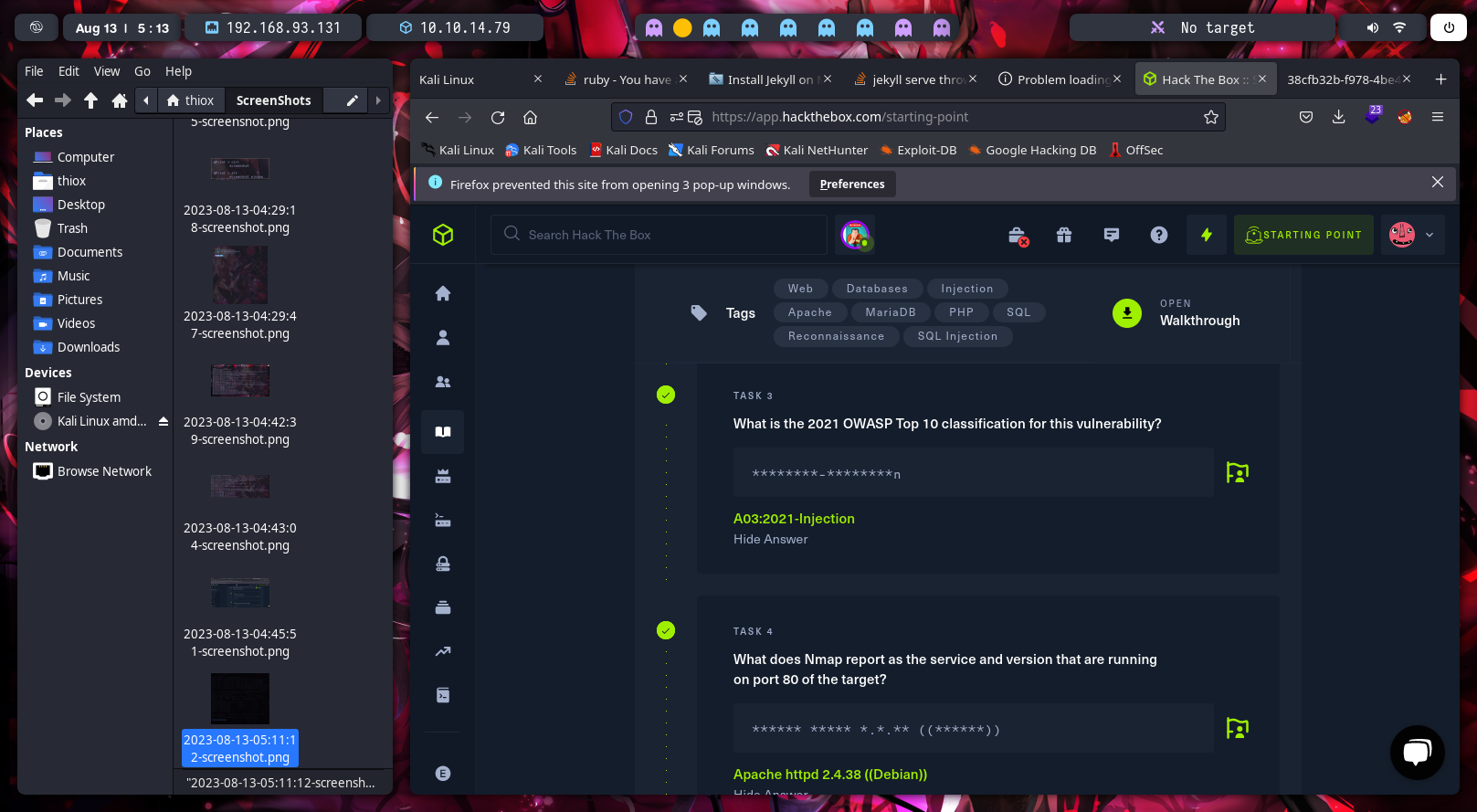
The third task is about the classification of the vulnerability SQL injection in 2021 Owasp Top 10. The correct name of this classification is “A03:2021-Injection”.
3rd HTB Task Solving
In the fourth task we need response which version of Apache has the machine, i got it using nmap -sV (Probe open ports to determine service/version info) -sC (equivalent to –script=default, it is using all defaults scrips of the nmap ) -p- (search in all ports) -T4 (it is the time for the requests, in the case of T5 is very aggresive and makes paranoic attack) IP (finally the IP of the objective machine is “10.129.108.144” ).
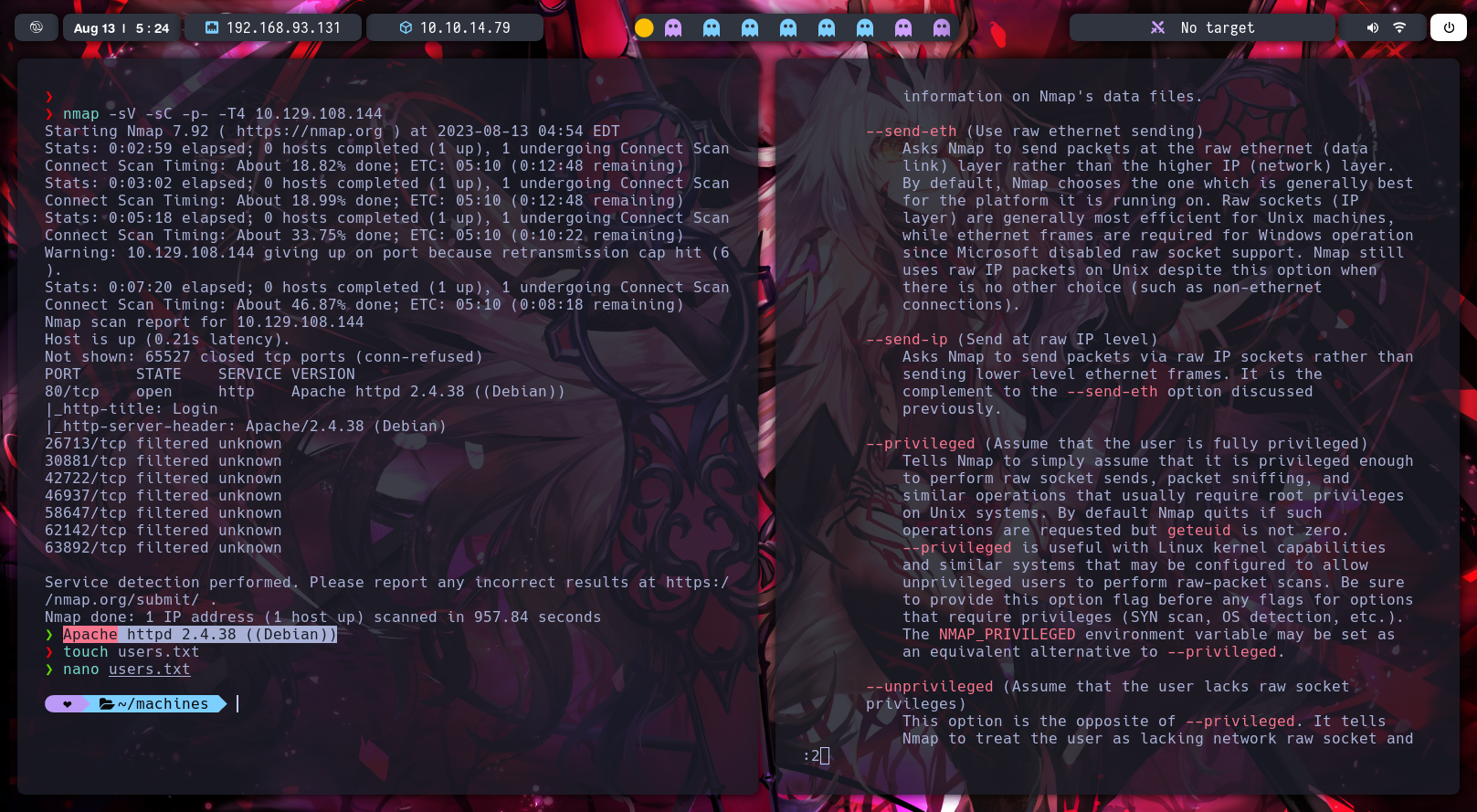
I got the response for the task 4. “Apache httpd 2.4.38 ((Debian))”
4th HTB Task Solving
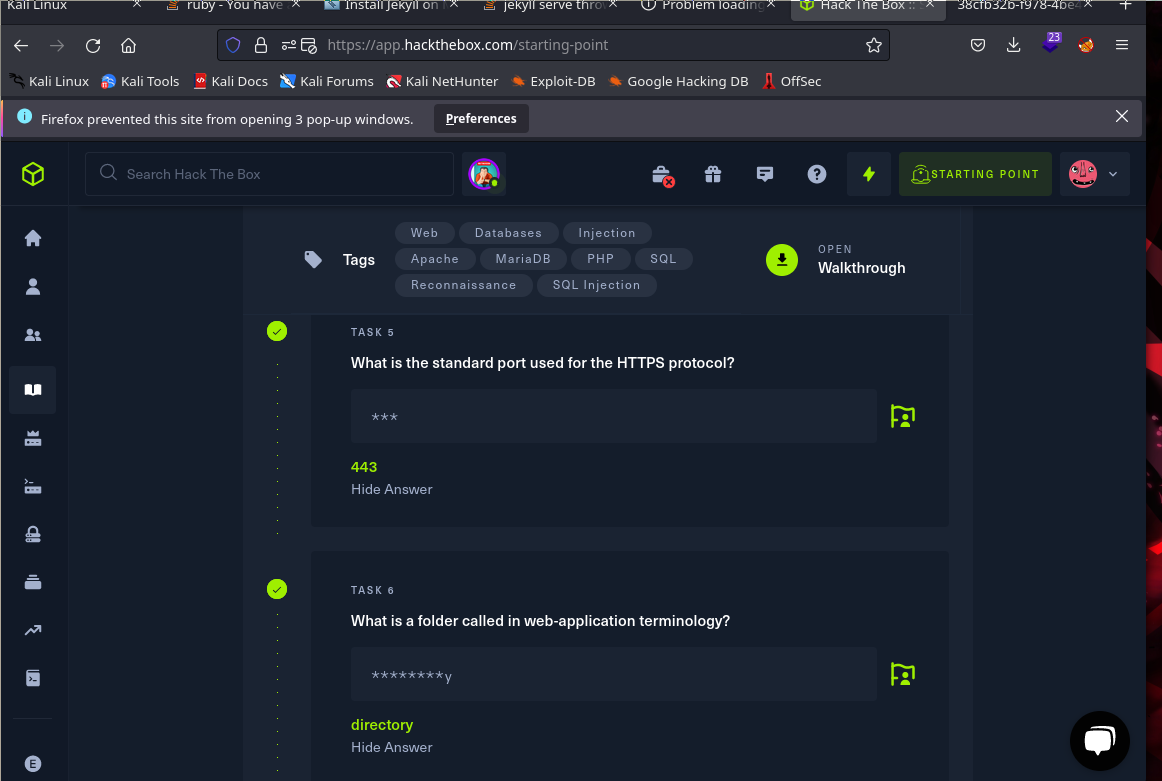
The standar port used for the HTTPS protocol is an easy response using google “443”. Because the old common port was 80, but when we used only HTTP, currently the most common port for HTTP-S (http secure) is the port 443. The next task is the name for the folders in web applications, it is a word than finally with y, the most accurate response is “directory”.
5th HTB Task Solving
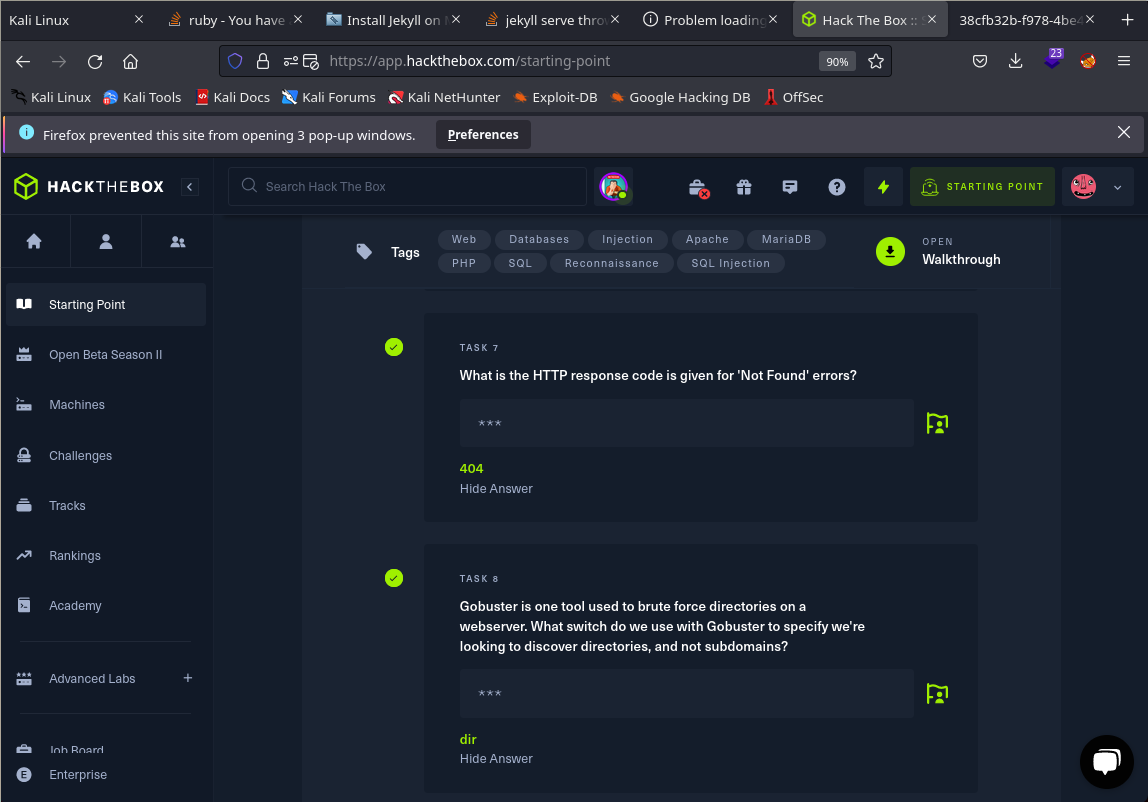
The 7th task is about the number of Not Found web errors, it is the most common “404”, i like programmer saw this kind of errors. The next task is about discover directories and not subdomains using Gobuster. It is visible using command –help in Gobuster and the correct response is “dir”.
6th HTB Task Solving
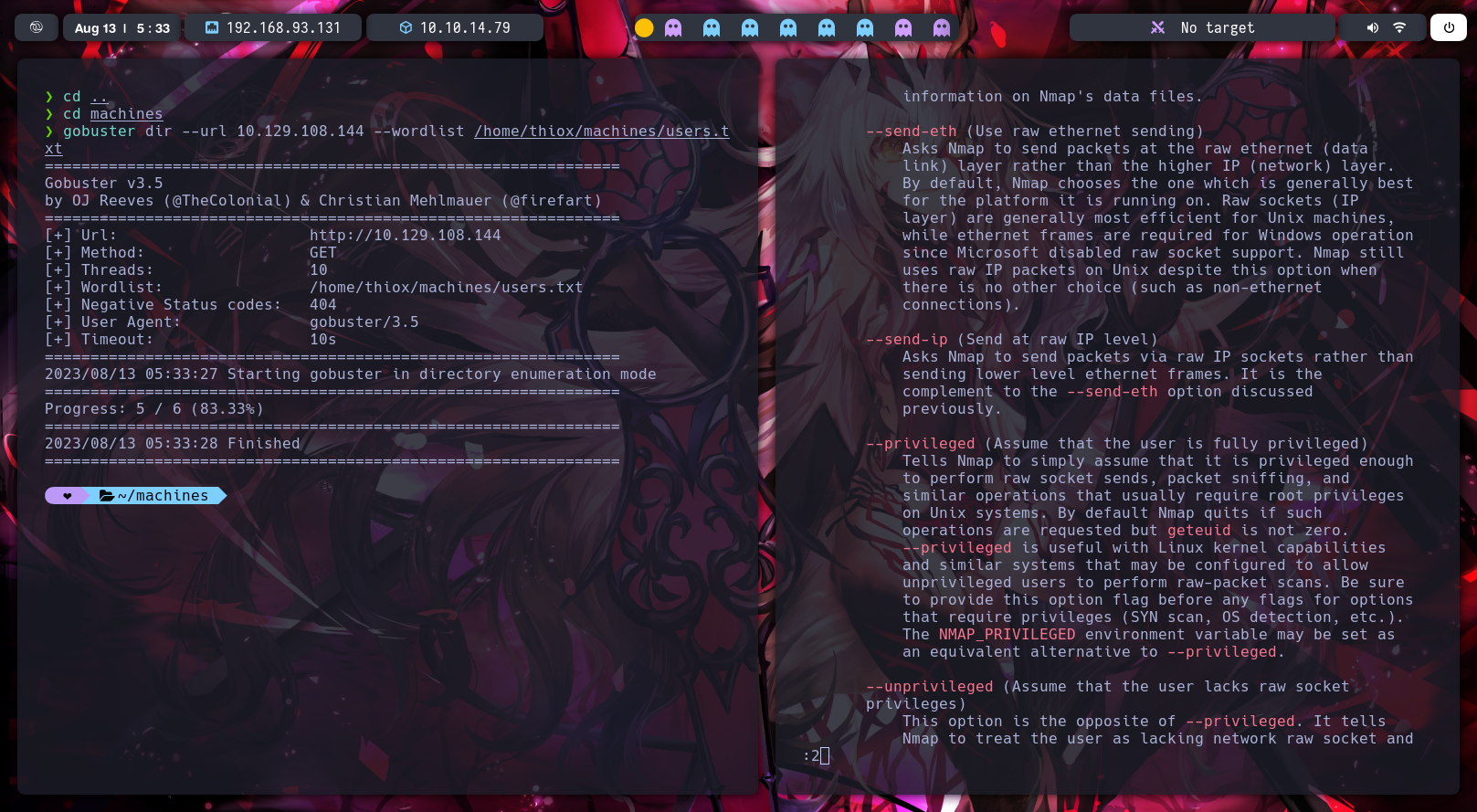
We used all previous commands mentioned in this document.

7th HTB Task Solving
We founded a web called LOG IN and how it is part of injection information, we only need use the most common users in this case “admin” + “/common injections strings like – ‘#” and for the password we use whatever password because we are doing SQL Injection.
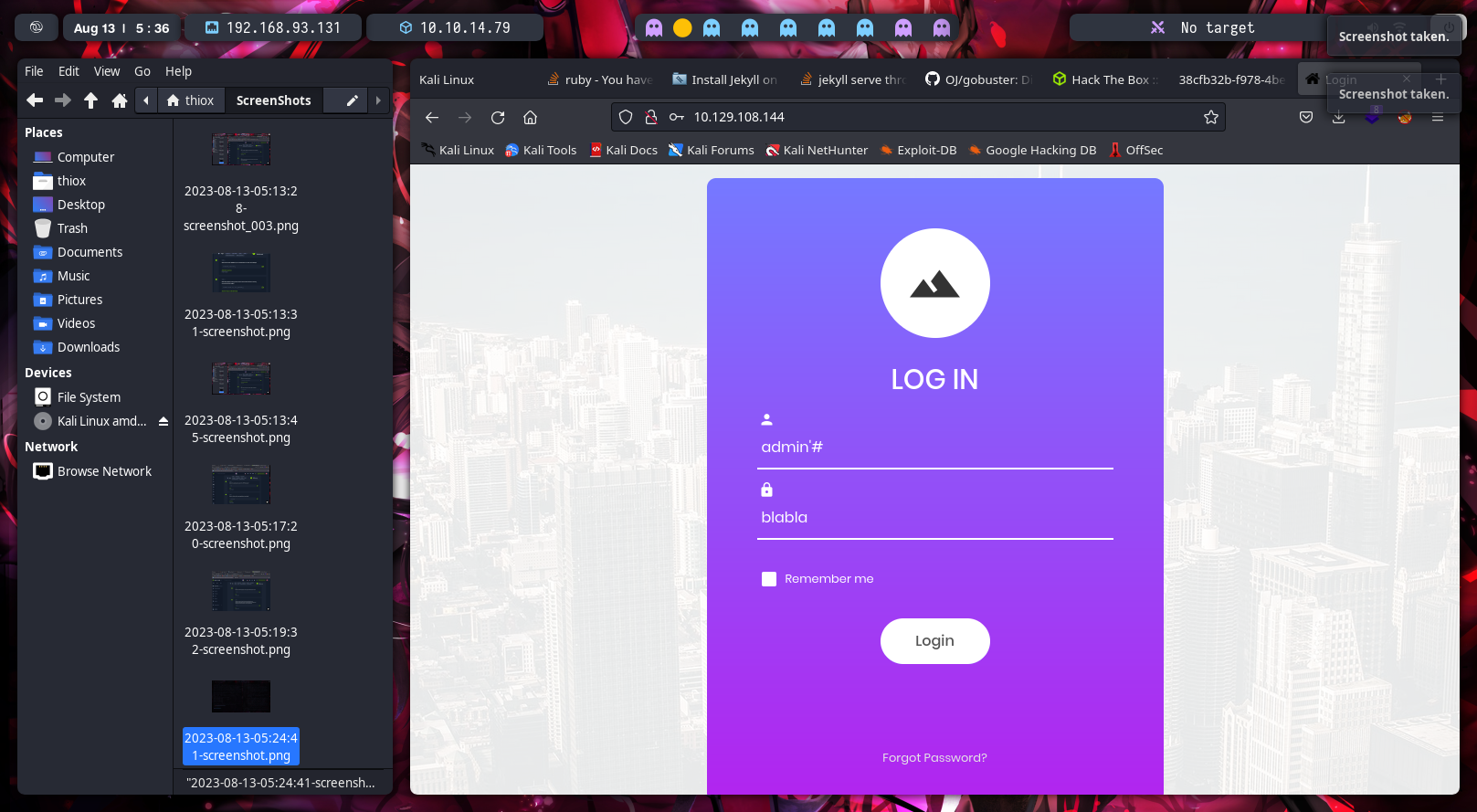
8th We founded the flag
We used the last credentials and we got the flag
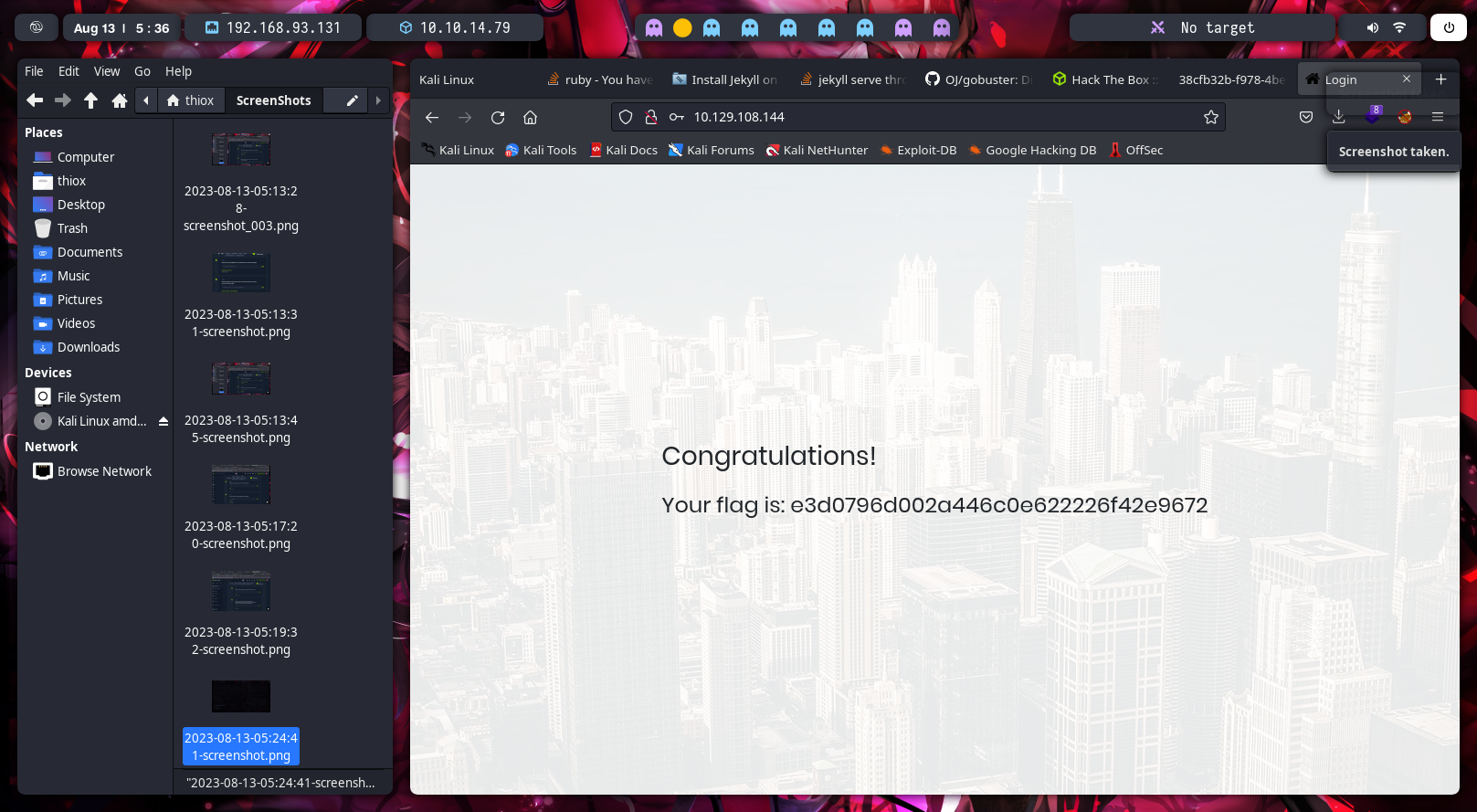
Last step
Finally the last step is to put all the answers how the word and the flag.